CVEFeed Newsroom – Latest Cybersecurity Updates
The "Cyber Newsroom Feed" module is a live feed of the latest cyber news enriched with CVE and vulnerability data. The feed is updated every 5 minutes and includes the latest news from the cyber security industry. The feed is designed to provide users with a comprehensive overview of the latest cyber security news and trends.

-
Huntress
Active Exploitation of Gladinet CentreStack/Triofox Insecure Cryptography Vulnerability
Acknowledgments: Special thanks to John Hammond for his contributions to this investigation and write-up. TL;DR: The AES implementation of Gladinet’s CentreStack and Triofox products contains hardcode ...

-
The Hacker News
Fortinet, Ivanti, and SAP Issue Urgent Patches for Authentication and Code Execution Flaws
Fortinet, Ivanti, and SAP have moved to address critical security flaws in their products that, if successfully exploited, could result in an authentication bypass and code execution. The Fortinet vul ...
-
Daily CyberSecurity
The “Surprise Metric”: Google’s New AI Architecture Outperforms GPT-4 in Memory
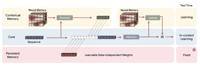
Do you recall the familiar frustration of reading a lengthy article only to forget the earlier sections by the time you reach the end? It appears that even AI now seeks to remedy this problem. Google’ ...

-
Daily CyberSecurity
Seamless Sign-In: Microsoft WebView2 Gets Entra ID for Enterprise Auth
WebView is, in essence, a browser-based control. In Windows 11, Microsoft primarily employs a Web component built upon Microsoft Edge, which itself is based on Chromium. As this control represents the ...

-
CybersecurityNews
Windows Cloud Files Mini Filter Driver 0-Day Vulnerability Exploited in the Wild to Escalate Privileges
Microsoft has released urgent security updates to address a zero-day vulnerability in the Windows Cloud Files Mini Filter Driver (cldflt.sys) that is currently being exploited in the wild. Assigned th ...

-
Daily CyberSecurity
CISA KEV Alert: WinRAR Zero-Day Used for Malware Injection and Windows UAF RCE Under Active Attack
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a new mandate for federal agencies to patch their systems immediately, following evidence of active exploitation in the wild. The ...

-
Daily CyberSecurity
Critical Fortinet Flaw Risks Unauthenticated Admin Bypass via FortiCloud SSO SAML Forgery
Fortinet has issued an urgent security advisory following the discovery of a critical vulnerability affecting its flagship network security products. The flaw, which carries a critical CVSS score of 9 ...

-
Daily CyberSecurity
Microsoft Patches Three Zero-Days Including Active Cloud Files UAF to SYSTEM and Copilot RCE
Microsoft has closed out the year with a substantial security update, addressing 72 vulnerabilities across its ecosystem in the December 2025 Patch Tuesday release. The update fixes three critical fla ...

-
Daily CyberSecurity
Critical Ivanti EPM Flaw (CVE-2025-10573) Risks Admin Session Hijack and Unauthenticated RCE
Ivanti has rolled out an urgent security update for its Endpoint Manager (EPM) solution, patching a cluster of severe vulnerabilities that could allow attackers to execute arbitrary code or hijack adm ...

-
TheCyberThrone
Microsoft Patch Tuesday December 2025
Microsoft’s final Patch Tuesday of 2025, released on December 9, addresses approximately 56-57 vulnerabilities across Windows, Office, Exchange, and related components, including three zero-days and s ...


