CVEFeed Newsroom – Latest Cybersecurity Updates
The "Cyber Newsroom Feed" module is a live feed of the latest cyber news enriched with CVE and vulnerability data. The feed is updated every 5 minutes and includes the latest news from the cyber security industry. The feed is designed to provide users with a comprehensive overview of the latest cyber security news and trends.

-
CybersecurityNews
FortiPAM and FortiSwitch Manager Vulnerability Let Attackers Bypass Authentication Process
Fortinet has issued an urgent advisory revealing a critical weakness in its FortiPAM and FortiSwitch Manager products that could allow attackers to sidestep authentication entirely through brute-force ...

-
CybersecurityNews
FortiOS CLI Command Bypass Vulnerability Let Attacker Execute System Commands
Fortinet disclosed a high-severity vulnerability in its FortiOS operating system on October 14, 2025, that could enable local authenticated attackers to execute arbitrary system commands. Tracked as C ...

-
BleepingComputer
Microsoft October 2025 Patch Tuesday fixes 6 zero-days, 172 flaws
Today is Microsoft's October 2025 Patch Tuesday, which includes security updates for 172 flaws, including six zero-day vulnerabilities.This Patch Tuesday also addresses eight "Critical" vulnerabilitie ...

-
CybersecurityNews
Microsoft October 2025 Patch Tuesday – 4 Zero-days and 172 Vulnerabilities Patched
Microsoft rolled out its October 2025 Patch Tuesday updates, addressing a staggering 172 vulnerabilities across its ecosystem, including four zero-day flaws, of which two are actively exploited in the ...

-
BleepingComputer
Oracles silently fixes zero-day exploit leaked by ShinyHunters
Oracle has silently fixed an Oracle E-Business Suite vulnerability (CVE-2025-61884) that was actively exploited to breach servers, with a proof-of-concept exploit publicly leaked by the ShinyHunters e ...

-
BleepingComputer
Oracle silently fixes zero-day exploit leaked by ShinyHunters
Oracle has silently fixed an Oracle E-Business Suite vulnerability (CVE-2025-61884) that was actively exploited to breach servers, with a proof-of-concept exploit publicly leaked by the ShinyHunters e ...

-
CybersecurityNews
UEFI Shell Vulnerabilities Could Let Hackers Bypass Secure Boot on 200,000+ Laptops
Hackers can exploit vulnerabilities in signed UEFI shells to bypass Secure Boot protections on over 200,000 Framework laptops and desktops. According to Eclypsium, these vulnerabilities expose fundame ...

-
BleepingComputer
Security firms debate CVE credit in overlapping vulnerability reports
Cybersecurity company FuzzingLabs has accused the Y Combinator-backed startup, Gecko Security, of replicating its vulnerability disclosures and backdating blog posts. According to the company, Gecko f ...

-
BleepingComputer
Security firms dispute credit for overlapping CVE reports
Cybersecurity company FuzzingLabs has accused the Y Combinator-backed startup, Gecko Security, of replicating its vulnerability disclosures and backdating blog posts. According to the company, Gecko f ...
-
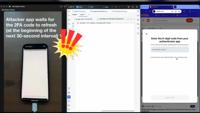
CybersecurityNews
New Pixnapping Attack Steals 2FA Codes From Google Authenticator Within 30 Seconds
Pixnapping, a novel class of side-channel attacks targeting Android devices that can covertly extract sensitive screen data, including two-factor authentication (2FA) codes from Google Authenticator i ...


