CVE-2019-0708
Microsoft Remote Desktop Services Remote Code Execution Vulnerability - [Actively Exploited]
Description
A remote code execution vulnerability exists in Remote Desktop Services formerly known as Terminal Services when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests, aka 'Remote Desktop Services Remote Code Execution Vulnerability'.
INFO
Published Date :
May 16, 2019, 7:29 p.m.
Last Modified :
Oct. 29, 2025, 2:45 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
Microsoft Remote Desktop Services, formerly known as Terminal Service, contains an unspecified vulnerability that allows an unauthenticated attacker to connect to the target system using RDP and send specially crafted requests. Successful exploitation allows for remote code execution. The vulnerability is also known under the moniker of BlueKeep.
Apply updates per vendor instructions.
Known Detected Feb 26, 2026
https://nvd.nist.gov/vuln/detail/CVE-2019-0708
Affected Products
The following products are affected by CVE-2019-0708
vulnerability.
Even if cvefeed.io is aware of the exact versions of the
products
that
are
affected, the information is not represented in the table below.
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 2.0 | HIGH | [email protected] | ||||
| CVSS 3.1 | CRITICAL | [email protected] | ||||
| CVSS 3.1 | CRITICAL | 134c704f-9b21-4f2e-91b3-4a467353bcc0 |
Solution
- Apply the appropriate security or cumulative update for your operating system to address the vulnerability.
- Reboot the system if required by the update process.
Public PoC/Exploit Available at Github
CVE-2019-0708 has a 506 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2019-0708.
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2019-0708 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2019-0708
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
None
Python JavaScript HTML CSS
Blue team tool for finding vulnerabilities and remediations proactively
Shell Python Jinja CSS
APT Vulnerability Assessment & Penetration Testing Lab
HTML Python
This repository presents a hands on Vulnerability Assessment and Penetration Testing (VAPT) project performed in a controlled virtual lab environment using virtual machine. The objective of this project is to demonstrate practical security testing techniques, including vulnerability identification, analysis.
Exploit Intelligence Platform MCP Server
cve database exploit vulnerability mcp-server
Makefile Python Dockerfile Shell
Search exploits, vulnerabilities, and threat intelligence from the Exploit Intelligence Platform.
cve database exploit vulnerabiity
Makefile Python Dockerfile Shell
Script that fetches CISA Known Exploited Vulnerabilities (KEV) and applies scriptable mitigations for new CVEs without waiting for Windows Update.
PowerShell
None
Shell
None
None
Python
A comprehensive suite of PowerShell-based security tools for Windows hardening, real-time threat detection, privacy protection, and vulnerability mitigation.
Batchfile PowerShell
Exploit Intel MCP Server
Python Makefile
Exploit Intel CLI Search Tool
Python Makefile
None
Python
An advanced, all-in-one Shodan skill for OpenClaw AI agents. Features Search, Scan, Alerts, Stream, Exploits, and more.
ai-agents cybersecurity openclaw python reconnaissance shodan skill
Python
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2019-0708 vulnerability anywhere in the article.

-
europa.eu
Cyber Brief 25-05 - April 2025
Cyber Brief (April 2025)May 2, 2025 - Version: 1TLP:CLEARExecutive summaryWe analysed 311 open source reports for this Cyber Brief1.Policy, cooperation, and law enforcement. The FBI sought help to ide ... Read more

-
The Hacker News
Kimsuky Exploits BlueKeep RDP Vulnerability to Breach Systems in South Korea and Japan
Cybersecurity researchers have flagged a new malicious campaign related to the North Korean state-sponsored threat actor known as Kimsuky that exploits a now-patched vulnerability impacting Microsoft ... Read more

-
Cyber Security News
Kimusky Hackers Exploiting RDP & MS Office Vulnerabilities in Targeted Attacks
A sophisticated Advanced Persistent Threat (APT) operation named Larva-24005, linked to the notorious Kimsuky threat group, has been discovered actively exploiting critical vulnerabilities in Remote D ... Read more
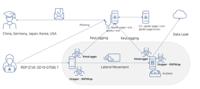
-
Daily CyberSecurity
Larva-24005: Kimsuky’s Global Cyber Espionage Campaign Exploits RDP and Office Flaws
A new cybersecurity report from the AhnLab Security intelligence Center (ASEC) has shed light on a recently identified operation linked to the notorious Kimsuky group. Dubbed “Larva-24005,” this campa ... Read more

-
Cyber Security News
Active Directory Attack Kill Chain Checklist & Tools List- 2025
The “Active Directory Kill Chain Attack & Defense” concept is a structured approach to understanding the sequence of events or stages involved in an Active Directory (AD) attack and the corresponding ... Read more

-
Cyber Security News
Hackers Exploiting Domain Controller to Deploy Ransomware Using RDP
Microsoft has recently uncovered a sharp rise in ransomware attacks exploiting domain controllers (DCs) through Remote Desktop Protocol (RDP), with the average attack costing organizations $9.36 milli ... Read more

-
The Cyber Express
December 2024 Cyble Report: Malware, Phishing, and IoT Vulnerabilities on the Rise
The latest Sensor Intelligence Report from Cyble, dated December 4–10, 2024, sheds light on a troubling increase in cyber threats, including malware intrusions, phishing scams, and attacks targeting v ... Read more

-
security.nl
VS publiceert overzicht van meest misbruikte kwetsbaarheden in 2023
De Amerikaanse autoriteiten hebben samen met cyberagentschappen uit Australië, Canada, Nieuw-Zeeland en het Verenigd Koninkrijk een overzicht van de meest misbruikte kwetsbaarheden in 2023 opgesteld. ... Read more

-
Trend Micro
Unmasking Prometei: A Deep Dive Into Our MXDR Findings
Cyber Threats How does Prometei insidiously operate in a compromised system? This Managed Extended Detection and Response investigation conducted with the help of Trend Vision One provides a comprehen ... Read more

-
Dark Reading
Why End of Life for Applications Is the Beginning of Life for Hackers
Source: Artur Szczybylo via Alamy Stock PhotoCOMMENTARYWe all get older. In IT, we face problems around aging software and keeping up with patches and updates. But there is another set of dates we sho ... Read more

-
malwaretech.com
[Video] Exploiting Windows RPC – CVE-2022-26809 Explained | Patch Analysis
Walking through my process of how I use patch analysis and reverse engineering to find vulnerabilities, then evaluate the risk and exploitability of bugs. ... Read more

-
curatedintel.org
Hacktivist group shares details related to Belarusian Railways hack
On Monday 24 January 2022, a Belarusian hacktivist group going by the name Belarusian Cyber-Partisans claimed responsibility for a limited attack against the national railway company. A primary object ... Read more

-
huntress.com
Keeping up with BlueKeep
Remote Desktop Services (RDS) benefit employees and IT administrators alike. With employees often working from anywhere, remote desktop reduces the physical burden of carrying a work laptop home 🏠. It ... Read more
The following table lists the changes that have been made to the
CVE-2019-0708 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Oct. 29, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2019-0708 Types: US Government Resource -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 22, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2019-0708 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2019-0708 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2019-0708 -
Modified Analysis by [email protected]
Apr. 07, 2025
Action Type Old Value New Value -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Feb. 07, 2025
Action Type Old Value New Value Added CVSS V3.1 AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Added CWE CWE-416 -
Modified Analysis by [email protected]
Jan. 27, 2025
Action Type Old Value New Value -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Nov. 21, 2024
Action Type Old Value New Value Added Reference http://packetstormsecurity.com/files/153133/Microsoft-Windows-Remote-Desktop-BlueKeep-Denial-Of-Service.html Added Reference http://packetstormsecurity.com/files/153627/Microsoft-Windows-RDP-BlueKeep-Denial-Of-Service.html Added Reference http://packetstormsecurity.com/files/154579/BlueKeep-RDP-Remote-Windows-Kernel-Use-After-Free.html Added Reference http://packetstormsecurity.com/files/155389/Microsoft-Windows-7-x86-BlueKeep-RDP-Use-After-Free.html Added Reference http://packetstormsecurity.com/files/162960/Microsoft-RDP-Remote-Code-Execution.html Added Reference http://www.huawei.com/en/psirt/security-advisories/huawei-sa-20190529-01-windows-en Added Reference http://www.huawei.com/en/psirt/security-notices/huawei-sn-20190515-01-windows-en Added Reference https://cert-portal.siemens.com/productcert/pdf/ssa-166360.pdf Added Reference https://cert-portal.siemens.com/productcert/pdf/ssa-406175.pdf Added Reference https://cert-portal.siemens.com/productcert/pdf/ssa-433987.pdf Added Reference https://cert-portal.siemens.com/productcert/pdf/ssa-616199.pdf Added Reference https://cert-portal.siemens.com/productcert/pdf/ssa-832947.pdf Added Reference https://cert-portal.siemens.com/productcert/pdf/ssa-932041.pdf Added Reference https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-0708 -
Modified Analysis by [email protected]
Jul. 25, 2024
Action Type Old Value New Value Removed CVSS V3 NIST AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Added CVSS V3.1 NIST AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Changed Reference Type http://packetstormsecurity.com/files/153133/Microsoft-Windows-Remote-Desktop-BlueKeep-Denial-Of-Service.html Third Party Advisory, VDB Entry http://packetstormsecurity.com/files/153133/Microsoft-Windows-Remote-Desktop-BlueKeep-Denial-Of-Service.html Exploit, Third Party Advisory, VDB Entry Changed Reference Type http://packetstormsecurity.com/files/153627/Microsoft-Windows-RDP-BlueKeep-Denial-Of-Service.html No Types Assigned http://packetstormsecurity.com/files/153627/Microsoft-Windows-RDP-BlueKeep-Denial-Of-Service.html Exploit, Third Party Advisory, VDB Entry Changed Reference Type http://packetstormsecurity.com/files/154579/BlueKeep-RDP-Remote-Windows-Kernel-Use-After-Free.html No Types Assigned http://packetstormsecurity.com/files/154579/BlueKeep-RDP-Remote-Windows-Kernel-Use-After-Free.html Exploit, Third Party Advisory, VDB Entry Changed Reference Type http://packetstormsecurity.com/files/155389/Microsoft-Windows-7-x86-BlueKeep-RDP-Use-After-Free.html No Types Assigned http://packetstormsecurity.com/files/155389/Microsoft-Windows-7-x86-BlueKeep-RDP-Use-After-Free.html Third Party Advisory, VDB Entry Changed Reference Type http://packetstormsecurity.com/files/162960/Microsoft-RDP-Remote-Code-Execution.html No Types Assigned http://packetstormsecurity.com/files/162960/Microsoft-RDP-Remote-Code-Execution.html Exploit, Third Party Advisory, VDB Entry Changed CPE Configuration OR *cpe:2.3:o:microsoft:windows_7:-:sp1:*:*:*:*:*:* *cpe:2.3:o:microsoft:windows_server_2003:-:sp2:*:*:*:*:x64:* *cpe:2.3:o:microsoft:windows_server_2003:-:sp2:*:*:*:*:x86:* *cpe:2.3:o:microsoft:windows_server_2003:r2:sp2:*:*:*:*:*:* *cpe:2.3:o:microsoft:windows_server_2008:-:sp2:*:*:*:*:*:* *cpe:2.3:o:microsoft:windows_server_2008:r2:sp1:*:*:*:*:itanium:* *cpe:2.3:o:microsoft:windows_server_2008:r2:sp1:*:*:*:*:x64:* *cpe:2.3:o:microsoft:windows_vista:-:sp2:*:*:*:*:*:* *cpe:2.3:o:microsoft:windows_xp:-:sp2:*:*:professional:*:x64:* *cpe:2.3:o:microsoft:windows_xp:-:sp3:*:*:*:*:x86:* OR *cpe:2.3:o:microsoft:windows_7:-:sp1:*:*:*:*:*:* *cpe:2.3:o:microsoft:windows_server_2008:-:sp2:*:*:*:*:*:* *cpe:2.3:o:microsoft:windows_server_2008:r2:sp1:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:axiom_multix_m_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:axiom_multix_m:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:axiom_vertix_md_trauma_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:axiom_vertix_md_trauma:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:axiom_vertix_solitaire_m_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:axiom_vertix_solitaire_m:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:mobilett_xp_digital_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:mobilett_xp_digital:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:multix_pro_acss_p_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:multix_pro_acss_p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:multix_pro_p_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:multix_pro_p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:multix_pro_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:multix_pro:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:multix_pro_acss_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:multix_pro_acss:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:multix_pro_navy_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:multix_pro_navy:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:multix_swing_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:multix_swing:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:multix_top_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:multix_top:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:multix_top_acss_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:multix_top_acss:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:multix_top_p_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:multix_top_p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:multix_top_acss_p_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:multix_top_acss_p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:vertix_solitaire_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:vertix_solitaire:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:atellica_solution_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:atellica_solution:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:aptio_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:aptio:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:streamlab_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:streamlab:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:centralink_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:centralink:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:viva_e_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:viva_e:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:viva_twin_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:viva_twin:-:*:*:*:*:*:*:* Added CPE Configuration OR *cpe:2.3:a:siemens:syngo_lab_process_manager:*:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:rapidpoint_500_firmware:*:*:*:*:*:*:*:* versions up to (including) 2.3.2 OR cpe:2.3:h:siemens:rapidpoint_500:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:siemens:lantis_firmware:*:*:*:*:*:*:*:* OR cpe:2.3:h:siemens:lantis:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:agile_controller-campus_firmware:v100r002c00:*:*:*:*:*:*:* *cpe:2.3:o:huawei:agile_controller-campus_firmware:v100r002c10:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:agile_controller-campus:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:bh620_v2_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:bh620_v2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:bh621_v2_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:bh621_v2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:bh622_v2_firmware:v100r001c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:bh622_v2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:bh640_v2_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:bh640_v2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:ch121_firmware:v100r001c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:ch121:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:ch140_firmware:v100r001c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:ch140:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:ch220_firmware:v100r001c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:ch220:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:ch221_firmware:v100r001c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:ch221:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:ch222_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:ch222:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:ch240_firmware:v100r001c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:ch240:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:ch242_firmware:v100r001c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:ch242:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:ch242_v3_firmware:v100r001c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:ch242_v3:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:e6000_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:e6000:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:e6000_chassis_firmware:v100r001c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:e6000_chassis:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:gtsoftx3000_firmware:v200r001c01spc100:*:*:*:*:*:*:* *cpe:2.3:o:huawei:gtsoftx3000_firmware:v200r002c00spc300:*:*:*:*:*:*:* *cpe:2.3:o:huawei:gtsoftx3000_firmware:v200r002c10spc100:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:gtsoftx3000:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:oceanstor_18500_firmware:v100r001c30spc300:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:oceanstor_18500:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:oceanstor_18800_firmware:v100r001c30spc300:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:oceanstor_18800:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:oceanstor_18800f_firmware:v100r001c30spc300:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:oceanstor_18800f:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:oceanstor_hvs85t_firmware:v100r001c00:*:*:*:*:*:*:* *cpe:2.3:o:huawei:oceanstor_hvs85t_firmware:v100r001c30spc200:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:oceanstor_hvs85t:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:oceanstor_hvs88t_firmware:v100r001c00:*:*:*:*:*:*:* *cpe:2.3:o:huawei:oceanstor_hvs88t_firmware:v100r001c30spc200:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:oceanstor_hvs88t:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:rh1288_v2_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:rh1288_v2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:rh1288a_v2_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:rh1288a_v2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:rh2265_v2_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:rh2265_v2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:rh2268_v2_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:rh2268_v2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:rh2285_v2_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:rh2285_v2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:rh2285h_v2_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:rh2285h_v2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:rh2288_v2_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:rh2288_v2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:rh2288a_v2_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:rh2288a_v2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:rh2288e_v2_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:rh2288e_v2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:rh2288h_v2_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:rh2288h_v2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:rh2485_v2_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:rh2485_v2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:rh5885_v2_firmware:v100r001c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:rh5885_v2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:rh5885_v3_firmware:v100r003c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:rh5885_v3:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:smc2.0_firmware:v500r002c00:*:*:*:*:*:*:* *cpe:2.3:o:huawei:smc2.0_firmware:v600r006c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:smc2.0:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:seco_vsm_firmware:v200r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:seco_vsm:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:uma_firmware:v200r001c00:*:*:*:*:*:*:* *cpe:2.3:o:huawei:uma_firmware:v300r001c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:uma:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:x6000_firmware:v100r002c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:x6000:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:x8000_firmware:v100r002c20:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:x8000:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:elog_firmware:v200r003c10:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:elog:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:huawei:espace_ecs_firmware:v300r001c00:*:*:*:*:*:*:* OR cpe:2.3:h:huawei:espace_ecs:-:*:*:*:*:*:*:* -
CVE Modified by [email protected]
May. 14, 2024
Action Type Old Value New Value -
CVE Modified by [email protected]
Jun. 03, 2021
Action Type Old Value New Value Added Reference http://packetstormsecurity.com/files/162960/Microsoft-RDP-Remote-Code-Execution.html [No Types Assigned] -
CWE Remap by [email protected]
Aug. 24, 2020
Action Type Old Value New Value Changed CWE CWE-20 CWE-416 -
CVE Modified by [email protected]
Nov. 19, 2019
Action Type Old Value New Value Added Reference http://packetstormsecurity.com/files/155389/Microsoft-Windows-7-x86-BlueKeep-RDP-Use-After-Free.html [No Types Assigned] -
CVE Modified by [email protected]
Sep. 23, 2019
Action Type Old Value New Value Added Reference http://packetstormsecurity.com/files/154579/BlueKeep-RDP-Remote-Windows-Kernel-Use-After-Free.html [No Types Assigned] -
CVE Modified by [email protected]
Jul. 15, 2019
Action Type Old Value New Value Added Reference http://packetstormsecurity.com/files/153627/Microsoft-Windows-RDP-BlueKeep-Denial-Of-Service.html [No Types Assigned] -
Modified Analysis by [email protected]
Jun. 03, 2019
Action Type Old Value New Value Changed Reference Type https://cert-portal.siemens.com/productcert/pdf/ssa-433987.pdf No Types Assigned https://cert-portal.siemens.com/productcert/pdf/ssa-433987.pdf Third Party Advisory Changed Reference Type https://cert-portal.siemens.com/productcert/pdf/ssa-832947.pdf No Types Assigned https://cert-portal.siemens.com/productcert/pdf/ssa-832947.pdf Third Party Advisory Changed Reference Type http://www.huawei.com/en/psirt/security-notices/huawei-sn-20190515-01-windows-en No Types Assigned http://www.huawei.com/en/psirt/security-notices/huawei-sn-20190515-01-windows-en Third Party Advisory Changed Reference Type https://cert-portal.siemens.com/productcert/pdf/ssa-932041.pdf No Types Assigned https://cert-portal.siemens.com/productcert/pdf/ssa-932041.pdf Third Party Advisory Changed Reference Type https://cert-portal.siemens.com/productcert/pdf/ssa-616199.pdf No Types Assigned https://cert-portal.siemens.com/productcert/pdf/ssa-616199.pdf Third Party Advisory Changed Reference Type https://cert-portal.siemens.com/productcert/pdf/ssa-166360.pdf No Types Assigned https://cert-portal.siemens.com/productcert/pdf/ssa-166360.pdf Third Party Advisory Changed Reference Type http://www.huawei.com/en/psirt/security-advisories/huawei-sa-20190529-01-windows-en No Types Assigned http://www.huawei.com/en/psirt/security-advisories/huawei-sa-20190529-01-windows-en Third Party Advisory Changed Reference Type https://cert-portal.siemens.com/productcert/pdf/ssa-406175.pdf No Types Assigned https://cert-portal.siemens.com/productcert/pdf/ssa-406175.pdf Third Party Advisory Changed Reference Type http://packetstormsecurity.com/files/153133/Microsoft-Windows-Remote-Desktop-BlueKeep-Denial-Of-Service.html No Types Assigned http://packetstormsecurity.com/files/153133/Microsoft-Windows-Remote-Desktop-BlueKeep-Denial-Of-Service.html Third Party Advisory, VDB Entry Changed CPE Configuration OR *cpe:2.3:o:microsoft:windows_7:-:sp1:*:*:*:*:*:* *cpe:2.3:o:microsoft:windows_server_2008:-:sp2:*:*:*:*:*:* *cpe:2.3:o:microsoft:windows_server_2008:r2:sp1:*:*:*:*:itanium:* *cpe:2.3:o:microsoft:windows_server_2008:r2:sp1:*:*:*:*:x64:* OR *cpe:2.3:o:microsoft:windows_7:-:sp1:*:*:*:*:*:* *cpe:2.3:o:microsoft:windows_server_2003:-:sp2:*:*:*:*:x64:* *cpe:2.3:o:microsoft:windows_server_2003:-:sp2:*:*:*:*:x86:* *cpe:2.3:o:microsoft:windows_server_2003:r2:sp2:*:*:*:*:*:* *cpe:2.3:o:microsoft:windows_server_2008:-:sp2:*:*:*:*:*:* *cpe:2.3:o:microsoft:windows_server_2008:r2:sp1:*:*:*:*:itanium:* *cpe:2.3:o:microsoft:windows_server_2008:r2:sp1:*:*:*:*:x64:* *cpe:2.3:o:microsoft:windows_vista:-:sp2:*:*:*:*:*:* *cpe:2.3:o:microsoft:windows_xp:-:sp2:*:*:professional:*:x64:* *cpe:2.3:o:microsoft:windows_xp:-:sp3:*:*:*:*:x86:* -
CVE Modified by [email protected]
May. 31, 2019
Action Type Old Value New Value Added Reference http://packetstormsecurity.com/files/153133/Microsoft-Windows-Remote-Desktop-BlueKeep-Denial-Of-Service.html [No Types Assigned] -
CVE Modified by [email protected]
May. 29, 2019
Action Type Old Value New Value Added Reference http://www.huawei.com/en/psirt/security-notices/huawei-sn-20190515-01-windows-en [No Types Assigned] -
CVE Modified by [email protected]
May. 29, 2019
Action Type Old Value New Value Added Reference http://www.huawei.com/en/psirt/security-advisories/huawei-sa-20190529-01-windows-en [No Types Assigned] -
CVE Modified by [email protected]
May. 24, 2019
Action Type Old Value New Value Added Reference https://cert-portal.siemens.com/productcert/pdf/ssa-832947.pdf [No Types Assigned] Added Reference https://cert-portal.siemens.com/productcert/pdf/ssa-616199.pdf [No Types Assigned] Added Reference https://cert-portal.siemens.com/productcert/pdf/ssa-433987.pdf [No Types Assigned] Added Reference https://cert-portal.siemens.com/productcert/pdf/ssa-406175.pdf [No Types Assigned] Added Reference https://cert-portal.siemens.com/productcert/pdf/ssa-166360.pdf [No Types Assigned] -
CVE Modified by [email protected]
May. 24, 2019
Action Type Old Value New Value Added Reference https://cert-portal.siemens.com/productcert/pdf/ssa-932041.pdf [No Types Assigned] -
Initial Analysis by [email protected]
May. 16, 2019
Action Type Old Value New Value Added CVSS V2 (AV:N/AC:L/Au:N/C:C/I:C/A:C) Added CVSS V3 AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Changed Reference Type https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-0708 No Types Assigned https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-0708 Patch, Vendor Advisory Added CWE CWE-20 Added CPE Configuration OR *cpe:2.3:o:microsoft:windows_7:-:sp1:*:*:*:*:*:* *cpe:2.3:o:microsoft:windows_server_2008:-:sp2:*:*:*:*:*:* *cpe:2.3:o:microsoft:windows_server_2008:r2:sp1:*:*:*:*:itanium:* *cpe:2.3:o:microsoft:windows_server_2008:r2:sp1:*:*:*:*:x64:* -
CVE Modified by [email protected]
May. 16, 2019
Action Type Old Value New Value Changed Description A remote code execution vulnerability exists in Remote Desktop Services – formerly known as Terminal Services – when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests, aka 'Remote Desktop Services� Remote Code Execution Vulnerability'. A remote code execution vulnerability exists in Remote Desktop Services formerly known as Terminal Services when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests, aka 'Remote Desktop Services Remote Code Execution Vulnerability'.
Vulnerability Scoring Details
Base CVSS Score: 9.8
Base CVSS Score: 10
Exploit Prediction
EPSS is a daily estimate of the probability of exploitation activity being observed over the next 30 days.
94.46 }} -0.03%
score
0.99991
percentile


