CVE-2023-22527
Atlassian Confluence Data Center and Server Template Injection Vulnerability - [Actively Exploited]
Description
A template injection vulnerability on older versions of Confluence Data Center and Server allows an unauthenticated attacker to achieve RCE on an affected instance. Customers using an affected version must take immediate action. Most recent supported versions of Confluence Data Center and Server are not affected by this vulnerability as it was ultimately mitigated during regular version updates. However, Atlassian recommends that customers take care to install the latest version to protect their instances from non-critical vulnerabilities outlined in Atlassian’s January Security Bulletin.
INFO
Published Date :
Jan. 16, 2024, 5:15 a.m.
Last Modified :
Oct. 24, 2025, 1:38 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
Atlassian Confluence Data Center and Server contain an unauthenticated OGNL template injection vulnerability that can lead to remote code execution.
Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable.
Known Detected Jan 24, 2024
https://confluence.atlassian.com/security/cve-2023-22527-rce-remote-code-execution-vulnerability-in-confluence-data-center-and-confluence-server-1333990257.html; https://nvd.nist.gov/vuln/detail/CVE-2023-22527
Affected Products
The following products are affected by CVE-2023-22527
vulnerability.
Even if cvefeed.io is aware of the exact versions of the
products
that
are
affected, the information is not represented in the table below.
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.0 | CRITICAL | [email protected] | ||||
| CVSS 3.1 | CRITICAL | [email protected] |
Solution
- Upgrade to Atlassian Confluence Server version 8.5.4, 8.6.0, 8.7.1, or later.
- If unable to upgrade, review the Atlassian Security Bulletin for further guidance.
Public PoC/Exploit Available at Github
CVE-2023-22527 has a 98 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2023-22527.
| URL | Resource |
|---|---|
| http://packetstormsecurity.com/files/176789/Atlassian-Confluence-SSTI-Injection.html | Exploit Third Party Advisory VDB Entry |
| https://confluence.atlassian.com/pages/viewpage.action?pageId=1333335615 | Vendor Advisory |
| https://jira.atlassian.com/browse/CONFSERVER-93833 | Issue Tracking Vendor Advisory |
| http://packetstormsecurity.com/files/176789/Atlassian-Confluence-SSTI-Injection.html | Exploit Third Party Advisory VDB Entry |
| https://confluence.atlassian.com/pages/viewpage.action?pageId=1333335615 | Vendor Advisory |
| https://jira.atlassian.com/browse/CONFSERVER-93833 | Issue Tracking Vendor Advisory |
| https://www.vicarius.io/vsociety/posts/pwning-confluence-via-ognl-injection-for-fun-and-learning-cve-2023-22527 | Exploit |
| https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2023-22527 | US Government Resource |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2023-22527 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2023-22527
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
None
Лабораторная работа №2 по дисциплине ЗПОЗАС
Fully automated Confluence RCE exploit (CVE-2023-22527 + OGNL injection) 100% from scratch • Python • 2025
Python
All PoC
PowerShell Python Java Shell C Makefile PHP Lua Roff Ruby
None
护网2024-POC收录备份
备份的漏洞库,3月开始我们来维护
None
CVE POC repo 자동 수집기
Python
None
None
None
None
Go PHP JavaScript Groovy Java Python VBScript
None
HTML
None
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2023-22527 vulnerability anywhere in the article.

-
Daily CyberSecurity
The Great Recalibration: Amazon Cuts 16,000 More Roles in Massive Shift to AI-First Future
The retail and technology titan Amazon has proclaimed a substantial expansion of its retrenchment efforts, signaling a new wave of layoffs poised to affect 16,000 corporate personnel. This maneuver fo ... Read more
-
Daily CyberSecurity
The “Surprise Metric”: Google’s New AI Architecture Outperforms GPT-4 in Memory
Do you recall the familiar frustration of reading a lengthy article only to forget the earlier sections by the time you reach the end? It appears that even AI now seeks to remedy this problem. Google’ ... Read more

-
Hackread - Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Years Long Linux Cryptominer Spotted Using Legit Sites to Spread Malware
A recent investigation by VulnCheck has exposed a cryptomining campaign that has been running unnoticed for years. The threat actor behind this operation, using the Linuxsys miner, has been targeting ... Read more

-
The Hacker News
Hackers Exploit Apache HTTP Server Flaw to Deploy Linuxsys Cryptocurrency Miner
Jul 17, 2025Ravie LakshmananCryptocurrency / Vulnerability Cybersecurity researchers have discovered a new campaign that exploits a known security flaw impacting Apache HTTP Server to deliver a cryp ... Read more
-
Cybersecurity News
LockBit 4.0: A Deep Dive into the Evolving Ransomware
LockBit has been a major player in the ransomware world since 2019, known for its sophisticated tactics and significant impact on organizations across various industries. The group operates under a Ra ... Read more

-
Cybersecurity News
From Confluence Vulnerability (CVE-2023-22527) to LockBit Encryption: A Rapid Attack Chain
LockBit ransom note | Image: The DFIR ReportSecurity researchers at The DFIR Report have uncovered a highly coordinated attack that leveraged a critical remote code execution (RCE) vulnerability in Co ... Read more

-
Cyber Security News
Wireshark 4.4.4 Released With Fix for Vulnerability That Triggers DoS Attack
The Wireshark Foundation has released version 4.4.4 of its widely used network protocol analyzer, addressing a high-severity vulnerability that could allow attackers to trigger denial-of-service (DoS) ... Read more

-
Cyber Security News
Hackers Exploited Confluence Server Vulnerability To Deploy LockBit Ransomware
A sophisticated ransomware attack leveraging a critical Atlassian Confluence vulnerability (CVE-2023-22527, CVSS 10.0) has been uncovered, culminating in the deployment of LockBit Black ransomware acr ... Read more

-
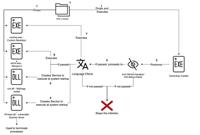
TheCyberThrone
Most Exploited Vulnerabilities in 2024 Top 20 Analysis
In 2024, the cybersecurity landscape saw a significant number of exploited vulnerabilities, highlighting the ongoing challenges organizations face in protecting their systems and data.Some key trends ... Read more
-
Cybersecurity News
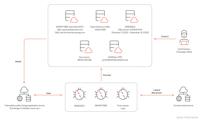
Evasive Malware Campaign Leverages CleverSoar Installer & Nidhogg Rootkit
CleverSoar Attack Flow | Image: Rapid7Rapid7 Labs has uncovered a sophisticated malware campaign employing the newly identified CleverSoar installer, a highly evasive threat targeting Chinese and Viet ... Read more
-
Cybersecurity News
CVE-2024-21887 and More: How Earth Estries APT Group Exploits VPNs & Servers
Campaign Alpha overview | Image: Trend MicroIn a detailed report from Trend Micro, the Chinese advanced persistent threat (APT) group Earth Estries, also known by aliases like Salt Typhoon and GhostEm ... Read more

-
Cybersecurity News
Critical Vulnerabilities in QNAP Notes Station 3: Update Now to Protect Your Data
QNAP has issued a security advisory regarding multiple critical vulnerabilities in Notes Station 3, a popular application for managing and sharing notes on QNAP devices. These vulnerabilities, with CV ... Read more

-
Cybersecurity News
Sonatype Nexus Repository 2 Hit By RCE (CVE-2024-5082) and XSS (CVE-2024-5083) Flaws
Sonatype has issued two security advisories for its Nexus Repository Manager 2.x, a popular repository manager used by organizations worldwide to store and distribute software artifacts, warning users ... Read more

-
security.nl
Amerikaanse ziekenhuizen gewaarschuwd voor Godzilla webshell
Het Amerikaanse ministerie van Volksgezondheid heeft ziekenhuizen en andere medische instellingen gewaarschuwd voor de 'Godzilla webshell' die bij aanvallen wordt ingezet en lastig te detecteren is (p ... Read more

-
Cybersecurity News
Frag Ransomware: A New Threat Exploits Veeam Vulnerability (CVE-2024-40711)
The Frag ransom note | Image: SophosSophos X-Ops recently uncovered Frag ransomware in a series of cyberattacks exploiting a vulnerability in Veeam backup servers, designated CVE-2024-40711. This newl ... Read more
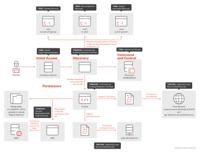
-
Cybersecurity News
Atlassian Confluence Vulnerability CVE-2023-22527 Exploited for Cryptomining
Attach chain | Image: Trend MicroIn a recently disclosed report by Trend Micro, attackers were observed exploiting a vulnerability in Atlassian’s Confluence servers (CVE-2023-22527) to hijack victim r ... Read more

-
Trend Micro
Attacker Abuses Victim Resources to Reap Rewards from Titan Network
Cyber Threats In this blog entry, we discuss how an attacker took advantage of the Atlassian Confluence vulnerability CVE-2023-22527 to connect servers to the Titan Network for cryptomining purposes. ... Read more
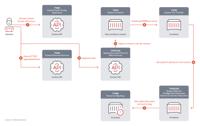
-
Cybersecurity News
Cryptojacking Alert: Hackers Exploit gRPC and HTTP/2 to Deploy Miners
Attack chain | Image: Trend MicroTrend Micro researchers have uncovered a new and unconventional method used by cybercriminals to deploy the SRBMiner cryptominer on Docker remote API servers. This att ... Read more
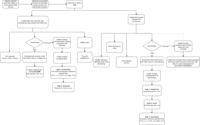
-
Cybersecurity News
LemonDuck Exploits EternalBlue Vulnerability for Cryptomining Attacks
A recent report from security researchers at Aufa and NetbyteSEC Interns sheds light on the resurgence of the LemonDuck malware, which is now exploiting the EternalBlue vulnerability (CVE-2017-0144) i ... Read more
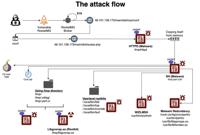
-
Cybersecurity News
Linux Servers Under Siege: “Perfctl” Malware Evades Detection for Years
The entire attack flow | Image: Aqua NautilusIn a recent report by Aqua Nautilus researchers Assaf Morag and Idan Revivo, the Linux server community has been alerted to the presence of a particularly ... Read more
The following table lists the changes that have been made to the
CVE-2023-22527 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Oct. 24, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2023-22527 Types: US Government Resource -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2023-22527 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2023-22527 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2023-22527 -
Modified Analysis by [email protected]
Feb. 09, 2025
Action Type Old Value New Value Changed Reference Type https://www.vicarius.io/vsociety/posts/pwning-confluence-via-ognl-injection-for-fun-and-learning-cve-2023-22527 No Types Assigned https://www.vicarius.io/vsociety/posts/pwning-confluence-via-ognl-injection-for-fun-and-learning-cve-2023-22527 Exploit -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Nov. 21, 2024
Action Type Old Value New Value Added Reference http://packetstormsecurity.com/files/176789/Atlassian-Confluence-SSTI-Injection.html Added Reference https://confluence.atlassian.com/pages/viewpage.action?pageId=1333335615 Added Reference https://jira.atlassian.com/browse/CONFSERVER-93833 Added Reference https://www.vicarius.io/vsociety/posts/pwning-confluence-via-ognl-injection-for-fun-and-learning-cve-2023-22527 -
Modified Analysis by [email protected]
Aug. 14, 2024
Action Type Old Value New Value -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Jul. 03, 2024
Action Type Old Value New Value Added CWE CISA-ADP CWE-74 -
Modified Analysis by [email protected]
Jun. 10, 2024
Action Type Old Value New Value Changed Reference Type http://packetstormsecurity.com/files/176789/Atlassian-Confluence-SSTI-Injection.html No Types Assigned http://packetstormsecurity.com/files/176789/Atlassian-Confluence-SSTI-Injection.html Exploit, Third Party Advisory, VDB Entry Changed Reference Type https://jira.atlassian.com/browse/CONFSERVER-93833 Permissions Required https://jira.atlassian.com/browse/CONFSERVER-93833 Issue Tracking, Vendor Advisory Changed CPE Configuration OR *cpe:2.3:a:atlassian:confluence_data_center:*:*:*:*:*:*:*:* versions from (including) 8.0.0 up to (excluding) 8.5.4 *cpe:2.3:a:atlassian:confluence_data_center:*:*:*:*:*:*:*:* versions from (including) 8.7.0 up to (excluding) 8.7.1 OR *cpe:2.3:a:atlassian:confluence_data_center:*:*:*:*:*:*:*:* versions from (including) 8.0.0 up to (excluding) 8.5.4 *cpe:2.3:a:atlassian:confluence_data_center:8.7.0:*:*:*:*:*:*:* -
CVE Modified by [email protected]
May. 14, 2024
Action Type Old Value New Value -
CVE Modified by [email protected]
Jan. 26, 2024
Action Type Old Value New Value Added Reference Atlassian http://packetstormsecurity.com/files/176789/Atlassian-Confluence-SSTI-Injection.html [No types assigned] -
CVE CISA KEV Update by 9119a7d8-5eab-497f-8521-727c672e3725
Jan. 25, 2024
Action Type Old Value New Value Added Vulnerability Name Atlassian Confluence Data Center and Server Template Injection Vulnerability Added Required Action Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable. Added Due Date 2024-02-14 Added Date Added 2024-01-24 -
Initial Analysis by [email protected]
Jan. 24, 2024
Action Type Old Value New Value Added CVSS V3.1 NIST AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Changed Reference Type https://confluence.atlassian.com/pages/viewpage.action?pageId=1333335615 No Types Assigned https://confluence.atlassian.com/pages/viewpage.action?pageId=1333335615 Vendor Advisory Changed Reference Type https://jira.atlassian.com/browse/CONFSERVER-93833 No Types Assigned https://jira.atlassian.com/browse/CONFSERVER-93833 Permissions Required Added CWE NIST CWE-74 Added CPE Configuration OR *cpe:2.3:a:atlassian:confluence_data_center:*:*:*:*:*:*:*:* versions from (including) 8.0.0 up to (excluding) 8.5.4 *cpe:2.3:a:atlassian:confluence_data_center:*:*:*:*:*:*:*:* versions from (including) 8.7.0 up to (excluding) 8.7.1 Added CPE Configuration OR *cpe:2.3:a:atlassian:confluence_server:*:*:*:*:*:*:*:* versions from (including) 8.0.0 up to (excluding) 8.5.4 -
CVE Modified by [email protected]
Jan. 16, 2024
Action Type Old Value New Value Changed Description Summary of Vulnerability A template injection vulnerability on older versions of Confluence Data Center and Server allows an unauthenticated attacker to achieve RCE on an affected instance. Customers using an affected version must take immediate action. Most recent supported versions of Confluence Data Center and Server are not affected by this vulnerability as it was ultimately mitigated during regular version updates. However, Atlassian recommends that customers take care to install the latest version to protect their instances from non-critical vulnerabilities outlined in Atlassian’s January Security Bulletin. See “What You Need to Do” for detailed instructions. {panel:bgColor=#deebff} Atlassian Cloud sites are not affected by this vulnerability. If your Confluence site is accessed via an atlassian.net domain, it is hosted by Atlassian and is not vulnerable to this issue. {panel} Affected Versions ||Product||Affected Versions|| |Confluence Data Center and Server|8.0.x 8.1.x 8.2.x 8.3.x 8.4.x 8.5.0 8.5.1 8.5.2 8.5.3| Fixed Versions ||Product||Fixed Versions|| |Confluence Data Center and Server|8.5.4 (LTS)| |Confluence Data Center|8.6.0 or later (Data Center Only) 8.7.1 or later (Data Center Only)| What You Need To Do Immediately patch to a fixed version Atlassian recommends that you patch each of your affected installations to the latest version. The listed Fixed Versions are no longer the most up-to-date versions and do not protect your instance from other non-critical vulnerabilities as outlined in Atlassian’s January Security Bulletin. ||Product||Fixed Versions||Latest Versions|| |Confluence Data Center and Server|8.5.4 (LTS)|8.5.5 (LTS)| |Confluence Data Center|8.6.0 or later (Data Center Only) 8.7.1 or later (Data Center Only)|8.7.2 or later (Data Center Only)| For additional details, please see full advisory. A template injection vulnerability on older versions of Confluence Data Center and Server allows an unauthenticated attacker to achieve RCE on an affected instance. Customers using an affected version must take immediate action. Most recent supported versions of Confluence Data Center and Server are not affected by this vulnerability as it was ultimately mitigated during regular version updates. However, Atlassian recommends that customers take care to install the latest version to protect their instances from non-critical vulnerabilities outlined in Atlassian’s January Security Bulletin. -
CVE Modified by [email protected]
Jan. 16, 2024
Action Type Old Value New Value Changed Description Summary of Vulnerability A template injection vulnerability on older versions of Confluence Data Center and Server allows an unauthenticated attacker to achieve RCE on an affected instance. Customers using an affected version must take immediate action. Most recent supported versions of Confluence Data Center and Server are not affected by this vulnerability as it was ultimately mitigated during regular version updates. However, Atlassian recommends that customers take care to install the latest version to protect their instances from non-critical vulnerabilities outlined in Atlassian’s January Security Bulletin. See “What You Need to Do” for detailed instructions. {panel:bgColor=#deebff} Atlassian Cloud sites are not affected by this vulnerability. If your Confluence site is accessed via an atlassian.net domain, it is hosted by Atlassian and is not vulnerable to this issue. {panel} Affected Versions ||Product||Affected Versions|| |Confluence Data Center and Server| 8.0.x 8.1.x 8.2.x 8.3.x 8.4.x 8.5.0 8.5.1 8.5.2 8.5.3| Fixed Versions ||Product||Fixed Versions|| |Confluence Data Center and Server|8.5.4 (LTS)| |Confluence Data Center| 8.6.0 or later (Data Center Only) 8.7.1 or later (Data Center Only)| What You Need To Do Immediately patch to a fixed version Atlassian recommends that you patch each of your affected installations to the latest version. The listed Fixed Versions are no longer the most up-to-date versions and do not protect your instance from other non-critical vulnerabilities as outlined in Atlassian’s January Security Bulletin. ||Product||Fixed Versions||Latest Versions|| |Confluence Data Center and Server| 8.5.4 (LTS)| 8.5.5 (LTS) |Confluence Data Center| 8.6.0 or later (Data Center Only) 8.7.1 or later (Data Center Only)| 8.6.3 or later (Data Center Only) 8.7.2 or later (Data Center Only) For additional details, please see full advisory. Summary of Vulnerability A template injection vulnerability on older versions of Confluence Data Center and Server allows an unauthenticated attacker to achieve RCE on an affected instance. Customers using an affected version must take immediate action. Most recent supported versions of Confluence Data Center and Server are not affected by this vulnerability as it was ultimately mitigated during regular version updates. However, Atlassian recommends that customers take care to install the latest version to protect their instances from non-critical vulnerabilities outlined in Atlassian’s January Security Bulletin. See “What You Need to Do” for detailed instructions. {panel:bgColor=#deebff} Atlassian Cloud sites are not affected by this vulnerability. If your Confluence site is accessed via an atlassian.net domain, it is hosted by Atlassian and is not vulnerable to this issue. {panel} Affected Versions ||Product||Affected Versions|| |Confluence Data Center and Server|8.0.x 8.1.x 8.2.x 8.3.x 8.4.x 8.5.0 8.5.1 8.5.2 8.5.3| Fixed Versions ||Product||Fixed Versions|| |Confluence Data Center and Server|8.5.4 (LTS)| |Confluence Data Center|8.6.0 or later (Data Center Only) 8.7.1 or later (Data Center Only)| What You Need To Do Immediately patch to a fixed version Atlassian recommends that you patch each of your affected installations to the latest version. The listed Fixed Versions are no longer the most up-to-date versions and do not protect your instance from other non-critical vulnerabilities as outlined in Atlassian’s January Security Bulletin. ||Product||Fixed Versions||Latest Versions|| |Confluence Data Center and Server|8.5.4 (LTS)|8.5.5 (LTS)| |Confluence Data Center|8.6.0 or later (Data Center Only) 8.7.1 or later (Data Center Only)|8.7.2 or later (Data Center Only)| For additional details, please see full advisory. -
CVE Received by [email protected]
Jan. 16, 2024
Action Type Old Value New Value Added Description Summary of Vulnerability A template injection vulnerability on older versions of Confluence Data Center and Server allows an unauthenticated attacker to achieve RCE on an affected instance. Customers using an affected version must take immediate action. Most recent supported versions of Confluence Data Center and Server are not affected by this vulnerability as it was ultimately mitigated during regular version updates. However, Atlassian recommends that customers take care to install the latest version to protect their instances from non-critical vulnerabilities outlined in Atlassian’s January Security Bulletin. See “What You Need to Do” for detailed instructions. {panel:bgColor=#deebff} Atlassian Cloud sites are not affected by this vulnerability. If your Confluence site is accessed via an atlassian.net domain, it is hosted by Atlassian and is not vulnerable to this issue. {panel} Affected Versions ||Product||Affected Versions|| |Confluence Data Center and Server| 8.0.x 8.1.x 8.2.x 8.3.x 8.4.x 8.5.0 8.5.1 8.5.2 8.5.3| Fixed Versions ||Product||Fixed Versions|| |Confluence Data Center and Server|8.5.4 (LTS)| |Confluence Data Center| 8.6.0 or later (Data Center Only) 8.7.1 or later (Data Center Only)| What You Need To Do Immediately patch to a fixed version Atlassian recommends that you patch each of your affected installations to the latest version. The listed Fixed Versions are no longer the most up-to-date versions and do not protect your instance from other non-critical vulnerabilities as outlined in Atlassian’s January Security Bulletin. ||Product||Fixed Versions||Latest Versions|| |Confluence Data Center and Server| 8.5.4 (LTS)| 8.5.5 (LTS) |Confluence Data Center| 8.6.0 or later (Data Center Only) 8.7.1 or later (Data Center Only)| 8.6.3 or later (Data Center Only) 8.7.2 or later (Data Center Only) For additional details, please see full advisory. Added Reference Atlassian https://confluence.atlassian.com/pages/viewpage.action?pageId=1333335615 [No types assigned] Added Reference Atlassian https://jira.atlassian.com/browse/CONFSERVER-93833 [No types assigned] Added CVSS V3 Atlassian AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
Vulnerability Scoring Details
Base CVSS Score: 9.8
Base CVSS Score: 10
Exploit Prediction
EPSS is a daily estimate of the probability of exploitation activity being observed over the next 30 days.
94.36 }} 0.01%
score
0.99960
percentile


