CVE-2023-4911
GNU C Library Buffer Overflow Vulnerability - [Actively Exploited]
Description
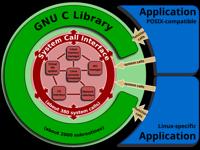
A buffer overflow was discovered in the GNU C Library's dynamic loader ld.so while processing the GLIBC_TUNABLES environment variable. This issue could allow a local attacker to use maliciously crafted GLIBC_TUNABLES environment variables when launching binaries with SUID permission to execute code with elevated privileges.
INFO
Published Date :
Oct. 3, 2023, 6:15 p.m.
Last Modified :
Feb. 13, 2026, 9:25 p.m.
Remotely Exploit :
No
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
GNU C Library's dynamic loader ld.so contains a buffer overflow vulnerability when processing the GLIBC_TUNABLES environment variable, allowing a local attacker to execute code with elevated privileges.
Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable.
This vulnerability affects a common open-source component, third-party library, or a protocol used by different products. Please check with specific vendors for information on patching status. For more information, please see: https://sourceware.org/git/?p=glibc.git;a=commitdiff;h=1056e5b4c3f2d90ed2b4a55f96add28da2f4c8fa, https://access.redhat.com/security/cve/cve-2023-4911, https://www.debian.org/security/2023/dsa-5514 ; https://nvd.nist.gov/vuln/detail/CVE-2023-4911
Affected Products
The following products are affected by CVE-2023-4911
vulnerability.
Even if cvefeed.io is aware of the exact versions of the
products
that
are
affected, the information is not represented in the table below.
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | HIGH | [email protected] | ||||
| CVSS 3.1 | HIGH | [email protected] |
Solution
- Update the affected glibc packages or the OS to the latest version.
- If applicable, ensure any dependent systems like Prism Central are also updated to a compatible version before upgrading.
Public PoC/Exploit Available at Github
CVE-2023-4911 has a 91 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2023-4911.
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2023-4911 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2023-4911
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
Linux CVE exploitation and mitigation lab – OverlayFS LPE & Looney Tunables.
None
Python HTML
None
None
None
None
An all-in-one Linux Privilege Escalation script that merges the core functionality and vectors of LinEnum, PEASS-ng, and AutoLocalPE. Delivers a consolidated, high-impact report to identify the fastest path to root.
Python
None
Standalone Container Security Tests
list of cve from 2001 to 2024
Python
None
Python C Shell PHP PowerShell ASP.NET
一个强大的Linux漏洞搜索工具,基于原始的[Linux -exploit- suggestion](https://github.com/mzet-/linux-exploit-suggester),专注于检测**2020-2024**期间最新的Linux内核特权升级漏洞。
Shell Python
None
Python Shell
None
Dockerfile Shell Python Mako HTML
Contains List of CVE's that I have found (Individual + Collaborative work)
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2023-4911 vulnerability anywhere in the article.
-
Daily CyberSecurity
Decades-Old Flaw & New Heap Corruption: Critical glibc Bugs Revealed
The maintainers of the GNU C Library (glibc), the core library that underpins the vast majority of Linux-based systems, have disclosed details on two security vulnerabilities ranging from high-severit ... Read more

-
Kaspersky
Exploits and vulnerabilities in Q3 2024
Q3 2024 saw multiple vulnerabilities discovered in Windows and Linux subsystems that are not standard for cyberattacks. This is because operating system developers have been releasing new security mit ... Read more
The following table lists the changes that have been made to the
CVE-2023-4911 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Feb. 13, 2026
Action Type Old Value New Value Added Reference Type CVE: https://www.exploit-db.com/exploits/52479 Types: Exploit, Third Party Advisory, VDB Entry -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Feb. 13, 2026
Action Type Old Value New Value Added Reference https://www.exploit-db.com/exploits/52479 -
Modified Analysis by [email protected]
Jan. 08, 2026
Action Type Old Value New Value Added CPE Configuration AND OR *cpe:2.3:o:netapp:bootstrap_os:-:*:*:*:*:*:*:* OR cpe:2.3:h:netapp:hci_compute_node:-:*:*:*:*:*:*:* Changed CPE Configuration OR *cpe:2.3:a:redhat:virtualization_host:4.0:*:*:*:*:*:*:* *cpe:2.3:a:redhat:virtualization:4.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_aus:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_tus:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_power_little_endian_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux:9.0:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_ibm_z_systems_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_arm64_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_aus:9.2:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_eus:9.2:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_power_little_endian_eus:9.2_ppc64le:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_arm64_eus:9.2_aarch64:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_ibm_z_systems_eus:9.2_s390x:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_ibm_z_systems:9.0_s390x:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_arm64:9.0_aarch64:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_eus:9.2:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_for_power_little_endian_update_services_for_sap_solutions:9.2_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_arm_64_eus:9.2_aarch64:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_arm_64:9.0_aarch64:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_arm_64_eus:8.6_aarch64:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems_eus_s390x:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_power_big_endian_eus:8.6_ppc64le:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_power_little_endian_eus:9.2_ppc64le:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_power_little_endian:9.0_ppc64le:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder:9.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_power_little_endian:9.0_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems_eus:9.2_s390x:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems:9.0_s390x:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_power_little_endian_eus:9.4_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_arm_64_eus:9.4_aarch64:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems_eus:9.4_s390x:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_aus:9.4:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_eus:9.4:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_arm64_eus:9.4_aarch64:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_ibm_z_systems_eus:9.4_s390x:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_power_little_endian_eus:9.4_ppc64le:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_eus:9.4:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_for_power_little_endian_update_services_for_sap_solutions:9.4_ppc64le:*:*:*:*:*:*:* OR *cpe:2.3:a:redhat:virtualization_host:4.0:*:*:*:*:*:*:* *cpe:2.3:a:redhat:virtualization:4.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_aus:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_tus:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_power_little_endian_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux:9.0:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_ibm_z_systems_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_arm64_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_aus:9.2:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_eus:9.2:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_power_little_endian_eus:9.2_ppc64le:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_arm64_eus:9.2_aarch64:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_ibm_z_systems_eus:9.2_s390x:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_ibm_z_systems:9.0_s390x:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_arm64:9.0_aarch64:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_eus:9.2:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_for_power_little_endian_update_services_for_sap_solutions:9.2_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_arm_64_eus:9.2_aarch64:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_arm_64:9.0_aarch64:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_arm_64_eus:8.6_aarch64:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems_eus_s390x:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_power_big_endian_eus:8.6_ppc64le:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_power_little_endian_eus:9.2_ppc64le:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_power_little_endian:9.0_ppc64le:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder:9.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_power_little_endian:9.0_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems_eus:9.2_s390x:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems:9.0_s390x:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_update_services_for_sap_solutions:9.2:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_power_little_endian_eus:9.4_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_arm_64_eus:9.4_aarch64:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems_eus:9.4_s390x:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_aus:9.4:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_eus:9.4:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_arm64_eus:9.4_aarch64:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_ibm_z_systems_eus:9.4_s390x:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_power_little_endian_eus:9.4_ppc64le:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_eus:9.4:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_for_power_little_endian_update_services_for_sap_solutions:9.4_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_update_services_for_sap_solutions:9.4:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_arm64_eus:9.6_aarch64:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_ibm_z_systems_eus:9.6_s390x:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_power_little_endian_eus:9.6_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_eus:9.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_arm_64_eus:9.6_aarch64:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems_eus:9.6_s390x:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_power_little_endian_eus:9.6_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_aus:9.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_for_power_little_endian_update_services_for_sap_solutions:9.6_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_update_services_for_sap_solutions:9.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_eus:9.6:*:*:*:*:*:*:* -
CVE Modified by [email protected]
Jan. 08, 2026
Action Type Old Value New Value Removed Reference https://access.redhat.com/errata/RHBA-2024:2413 Removed Reference Type https://access.redhat.com/errata/RHBA-2024:2413 Types: Third Party Advisory -
Modified Analysis by [email protected]
Nov. 06, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2023-4911 Types: US Government Resource -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2023-4911 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2023-4911 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2023-4911 -
Modified Analysis by [email protected]
May. 06, 2025
Action Type Old Value New Value Added Reference Type Red Hat, Inc.: https://access.redhat.com/errata/RHBA-2024:2413 Types: Third Party Advisory -
CVE Modified by [email protected]
Apr. 30, 2025
Action Type Old Value New Value Added Reference https://access.redhat.com/errata/RHBA-2024:2413 -
Modified Analysis by [email protected]
Jan. 27, 2025
Action Type Old Value New Value Changed CPE Configuration OR *cpe:2.3:a:redhat:codeready_linux_builder_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_arm64_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_ibm_z_systems_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_power_little_endian_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:virtualization:4.0:*:*:*:*:*:*:* *cpe:2.3:a:redhat:virtualization_host:4.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux:9.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_arm_64_eus:8.6_aarch64:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems_eus_s390x:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_power_big_endian_eus:8.6_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_aus:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_tus:8.6:*:*:*:*:*:*:* OR *cpe:2.3:a:redhat:codeready_linux_builder:9.0:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_eus:9.2:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_eus:9.4:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_arm64:9.0_aarch64:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_arm64_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_arm64_eus:9.2_aarch64:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_arm64_eus:9.4_aarch64:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_ibm_z_systems:9.0_s390x:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_ibm_z_systems_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_ibm_z_systems_eus:9.2_s390x:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_ibm_z_systems_eus:9.4_s390x:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_power_little_endian:9.0_ppc64le:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_power_little_endian_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_power_little_endian_eus:9.2_ppc64le:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_power_little_endian_eus:9.4_ppc64le:*:*:*:*:*:*:* *cpe:2.3:a:redhat:virtualization:4.0:*:*:*:*:*:*:* *cpe:2.3:a:redhat:virtualization_host:4.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux:9.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_eus:9.2:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_eus:9.4:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_arm_64:9.0_aarch64:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_arm_64_eus:8.6_aarch64:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_arm_64_eus:9.2_aarch64:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_arm_64_eus:9.4_aarch64:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems:9.0_s390x:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems_eus:9.2_s390x:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems_eus:9.4_s390x:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems_eus_s390x:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_power_big_endian_eus:8.6_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_power_little_endian:9.0_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_power_little_endian_eus:9.2_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_power_little_endian_eus:9.4_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_aus:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_aus:9.2:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_aus:9.4:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_for_power_little_endian_update_services_for_sap_solutions:9.2_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_for_power_little_endian_update_services_for_sap_solutions:9.4_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_tus:8.6:*:*:*:*:*:*:* Changed CPE Configuration OR *cpe:2.3:o:canonical:ubuntu_linux:22.04:*:*:*:lts:*:*:* *cpe:2.3:o:canonical:ubuntu_linux:23.04:*:*:*:*:*:*:* *cpe:2.3:o:debian:debian_linux:12.0:*:*:*:*:*:*:* *cpe:2.3:o:debian:debian_linux:13.0:*:*:*:*:*:*:* OR *cpe:2.3:o:canonical:ubuntu_linux:22.04:*:*:*:lts:*:*:* *cpe:2.3:o:canonical:ubuntu_linux:23.04:*:*:*:*:*:*:* *cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:* *cpe:2.3:o:debian:debian_linux:12.0:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:netapp:h300s_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:netapp:h300s:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:netapp:h410c_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:netapp:h410c:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:netapp:h410s_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:netapp:h410s:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:netapp:h500s_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:netapp:h500s:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:netapp:h700s_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:netapp:h700s:-:*:*:*:*:*:*:* Added CPE Configuration OR *cpe:2.3:a:netapp:ontap_select_deploy_administration_utility:-:*:*:*:*:*:*:* Changed Reference Type http://packetstormsecurity.com/files/174986/glibc-ld.so-Local-Privilege-Escalation.html No Types Assigned http://packetstormsecurity.com/files/174986/glibc-ld.so-Local-Privilege-Escalation.html Exploit, Third Party Advisory, VDB Entry Changed Reference Type http://packetstormsecurity.com/files/176288/Glibc-Tunables-Privilege-Escalation.html No Types Assigned http://packetstormsecurity.com/files/176288/Glibc-Tunables-Privilege-Escalation.html Exploit, Third Party Advisory, VDB Entry Changed Reference Type http://seclists.org/fulldisclosure/2023/Oct/11 No Types Assigned http://seclists.org/fulldisclosure/2023/Oct/11 Exploit, Mailing List, Third Party Advisory Changed Reference Type http://www.openwall.com/lists/oss-security/2023/10/03/2 No Types Assigned http://www.openwall.com/lists/oss-security/2023/10/03/2 Exploit, Mailing List Changed Reference Type http://www.openwall.com/lists/oss-security/2023/10/03/3 No Types Assigned http://www.openwall.com/lists/oss-security/2023/10/03/3 Mailing List Changed Reference Type http://www.openwall.com/lists/oss-security/2023/10/05/1 No Types Assigned http://www.openwall.com/lists/oss-security/2023/10/05/1 Mailing List Changed Reference Type http://www.openwall.com/lists/oss-security/2023/10/13/11 No Types Assigned http://www.openwall.com/lists/oss-security/2023/10/13/11 Mailing List Changed Reference Type http://www.openwall.com/lists/oss-security/2023/10/14/3 No Types Assigned http://www.openwall.com/lists/oss-security/2023/10/14/3 Mailing List Changed Reference Type http://www.openwall.com/lists/oss-security/2023/10/14/5 No Types Assigned http://www.openwall.com/lists/oss-security/2023/10/14/5 Mailing List Changed Reference Type http://www.openwall.com/lists/oss-security/2023/10/14/6 No Types Assigned http://www.openwall.com/lists/oss-security/2023/10/14/6 Mailing List Changed Reference Type https://access.redhat.com/security/cve/CVE-2023-4911 Mitigation, Third Party Advisory https://access.redhat.com/security/cve/CVE-2023-4911 Third Party Advisory Changed Reference Type https://access.redhat.com/security/cve/CVE-2023-4911 Mitigation, Third Party Advisory https://access.redhat.com/security/cve/CVE-2023-4911 Third Party Advisory Changed Reference Type https://bugzilla.redhat.com/show_bug.cgi?id=2238352 Issue Tracking, Patch, Third Party Advisory https://bugzilla.redhat.com/show_bug.cgi?id=2238352 Issue Tracking, Patch Changed Reference Type https://bugzilla.redhat.com/show_bug.cgi?id=2238352 Issue Tracking, Patch, Third Party Advisory https://bugzilla.redhat.com/show_bug.cgi?id=2238352 Issue Tracking, Patch Changed Reference Type https://lists.fedoraproject.org/archives/list/[email protected]/message/4DBUQRRPB47TC3NJOUIBVWUGFHBJAFDL/ No Types Assigned https://lists.fedoraproject.org/archives/list/[email protected]/message/4DBUQRRPB47TC3NJOUIBVWUGFHBJAFDL/ Mailing List Changed Reference Type https://lists.fedoraproject.org/archives/list/[email protected]/message/DFG4P76UHHZEWQ26FWBXG76N2QLKKPZA/ No Types Assigned https://lists.fedoraproject.org/archives/list/[email protected]/message/DFG4P76UHHZEWQ26FWBXG76N2QLKKPZA/ Mailing List Changed Reference Type https://lists.fedoraproject.org/archives/list/[email protected]/message/NDAQWHTSVOCOZ5K6KPIWKRT3JX4RTZUR/ No Types Assigned https://lists.fedoraproject.org/archives/list/[email protected]/message/NDAQWHTSVOCOZ5K6KPIWKRT3JX4RTZUR/ Mailing List Changed Reference Type https://security.gentoo.org/glsa/202310-03 No Types Assigned https://security.gentoo.org/glsa/202310-03 Third Party Advisory Changed Reference Type https://security.netapp.com/advisory/ntap-20231013-0006/ No Types Assigned https://security.netapp.com/advisory/ntap-20231013-0006/ Third Party Advisory Changed Reference Type https://www.debian.org/security/2023/dsa-5514 No Types Assigned https://www.debian.org/security/2023/dsa-5514 Mailing List -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Nov. 21, 2024
Action Type Old Value New Value Added Reference http://packetstormsecurity.com/files/174986/glibc-ld.so-Local-Privilege-Escalation.html Added Reference http://packetstormsecurity.com/files/176288/Glibc-Tunables-Privilege-Escalation.html Added Reference http://seclists.org/fulldisclosure/2023/Oct/11 Added Reference http://www.openwall.com/lists/oss-security/2023/10/03/2 Added Reference http://www.openwall.com/lists/oss-security/2023/10/03/3 Added Reference http://www.openwall.com/lists/oss-security/2023/10/05/1 Added Reference http://www.openwall.com/lists/oss-security/2023/10/13/11 Added Reference http://www.openwall.com/lists/oss-security/2023/10/14/3 Added Reference http://www.openwall.com/lists/oss-security/2023/10/14/5 Added Reference http://www.openwall.com/lists/oss-security/2023/10/14/6 Added Reference https://access.redhat.com/errata/RHSA-2023:5453 Added Reference https://access.redhat.com/errata/RHSA-2023:5454 Added Reference https://access.redhat.com/errata/RHSA-2023:5455 Added Reference https://access.redhat.com/errata/RHSA-2023:5476 Added Reference https://access.redhat.com/errata/RHSA-2024:0033 Added Reference https://access.redhat.com/security/cve/CVE-2023-4911 Added Reference https://bugzilla.redhat.com/show_bug.cgi?id=2238352 Added Reference https://lists.fedoraproject.org/archives/list/[email protected]/message/4DBUQRRPB47TC3NJOUIBVWUGFHBJAFDL/ Added Reference https://lists.fedoraproject.org/archives/list/[email protected]/message/DFG4P76UHHZEWQ26FWBXG76N2QLKKPZA/ Added Reference https://lists.fedoraproject.org/archives/list/[email protected]/message/NDAQWHTSVOCOZ5K6KPIWKRT3JX4RTZUR/ Added Reference https://security.gentoo.org/glsa/202310-03 Added Reference https://security.netapp.com/advisory/ntap-20231013-0006/ Added Reference https://www.debian.org/security/2023/dsa-5514 Added Reference https://www.qualys.com/2023/10/03/cve-2023-4911/looney-tunables-local-privilege-escalation-glibc-ld-so.txt Added Reference https://www.qualys.com/cve-2023-4911/ -
Modified Analysis by [email protected]
Sep. 17, 2024
Action Type Old Value New Value Changed Reference Type https://access.redhat.com/security/cve/CVE-2023-4911 Third Party Advisory https://access.redhat.com/security/cve/CVE-2023-4911 Mitigation, Third Party Advisory Changed Reference Type https://www.qualys.com/2023/10/03/cve-2023-4911/looney-tunables-local-privilege-escalation-glibc-ld-so.txt Exploit https://www.qualys.com/2023/10/03/cve-2023-4911/looney-tunables-local-privilege-escalation-glibc-ld-so.txt Exploit, Third Party Advisory Added CPE Configuration OR *cpe:2.3:o:canonical:ubuntu_linux:22.04:*:*:*:lts:*:*:* *cpe:2.3:o:canonical:ubuntu_linux:23.04:*:*:*:*:*:*:* *cpe:2.3:o:debian:debian_linux:12.0:*:*:*:*:*:*:* *cpe:2.3:o:debian:debian_linux:13.0:*:*:*:*:*:*:* -
CVE Modified by [email protected]
Sep. 16, 2024
Action Type Old Value New Value Removed Reference Red Hat, Inc. http://www.openwall.com/lists/oss-security/2023/10/03/3 Removed Reference Red Hat, Inc. http://www.openwall.com/lists/oss-security/2023/10/03/2 Removed Reference Red Hat, Inc. https://www.debian.org/security/2023/dsa-5514 Removed Reference Red Hat, Inc. https://security.gentoo.org/glsa/202310-03 Removed Reference Red Hat, Inc. https://lists.fedoraproject.org/archives/list/[email protected]/message/NDAQWHTSVOCOZ5K6KPIWKRT3JX4RTZUR/ Removed Reference Red Hat, Inc. https://lists.fedoraproject.org/archives/list/[email protected]/message/4DBUQRRPB47TC3NJOUIBVWUGFHBJAFDL/ Removed Reference Red Hat, Inc. https://lists.fedoraproject.org/archives/list/[email protected]/message/DFG4P76UHHZEWQ26FWBXG76N2QLKKPZA/ Removed Reference Red Hat, Inc. http://www.openwall.com/lists/oss-security/2023/10/05/1 Removed Reference Red Hat, Inc. http://seclists.org/fulldisclosure/2023/Oct/11 Removed Reference Red Hat, Inc. http://packetstormsecurity.com/files/174986/glibc-ld.so-Local-Privilege-Escalation.html Removed Reference Red Hat, Inc. https://security.netapp.com/advisory/ntap-20231013-0006/ Removed Reference Red Hat, Inc. http://www.openwall.com/lists/oss-security/2023/10/13/11 Removed Reference Red Hat, Inc. http://www.openwall.com/lists/oss-security/2023/10/14/3 Removed Reference Red Hat, Inc. http://www.openwall.com/lists/oss-security/2023/10/14/5 Removed Reference Red Hat, Inc. http://www.openwall.com/lists/oss-security/2023/10/14/6 Removed Reference Red Hat, Inc. http://packetstormsecurity.com/files/176288/Glibc-Tunables-Privilege-Escalation.html -
CVE Modified by [email protected]
May. 23, 2024
Action Type Old Value New Value -
CVE Modified by [email protected]
May. 14, 2024
Action Type Old Value New Value -
Modified Analysis by [email protected]
Feb. 22, 2024
Action Type Old Value New Value Changed Reference Type http://packetstormsecurity.com/files/174986/glibc-ld.so-Local-Privilege-Escalation.html No Types Assigned http://packetstormsecurity.com/files/174986/glibc-ld.so-Local-Privilege-Escalation.html Exploit, Third Party Advisory Changed Reference Type http://packetstormsecurity.com/files/176288/Glibc-Tunables-Privilege-Escalation.html No Types Assigned http://packetstormsecurity.com/files/176288/Glibc-Tunables-Privilege-Escalation.html Exploit, Third Party Advisory Changed Reference Type http://seclists.org/fulldisclosure/2023/Oct/11 No Types Assigned http://seclists.org/fulldisclosure/2023/Oct/11 Exploit, Mailing List, Third Party Advisory Changed Reference Type http://www.openwall.com/lists/oss-security/2023/10/13/11 No Types Assigned http://www.openwall.com/lists/oss-security/2023/10/13/11 Mailing List Changed Reference Type http://www.openwall.com/lists/oss-security/2023/10/14/3 No Types Assigned http://www.openwall.com/lists/oss-security/2023/10/14/3 Mailing List Changed Reference Type http://www.openwall.com/lists/oss-security/2023/10/14/5 No Types Assigned http://www.openwall.com/lists/oss-security/2023/10/14/5 Mailing List Changed Reference Type http://www.openwall.com/lists/oss-security/2023/10/14/6 No Types Assigned http://www.openwall.com/lists/oss-security/2023/10/14/6 Third Party Advisory Changed Reference Type https://access.redhat.com/errata/RHSA-2023:5476 No Types Assigned https://access.redhat.com/errata/RHSA-2023:5476 Third Party Advisory Changed Reference Type https://access.redhat.com/errata/RHSA-2024:0033 No Types Assigned https://access.redhat.com/errata/RHSA-2024:0033 Third Party Advisory Changed Reference Type https://security.netapp.com/advisory/ntap-20231013-0006/ No Types Assigned https://security.netapp.com/advisory/ntap-20231013-0006/ Mailing List, Third Party Advisory Changed CPE Configuration OR *cpe:2.3:a:gnu:glibc:-:*:*:*:*:*:*:* OR *cpe:2.3:a:gnu:glibc:*:*:*:*:*:*:*:* versions from (including) 2.34 up to (excluding) 2.39 Changed CPE Configuration OR *cpe:2.3:a:redhat:virtualization:4.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux:9.0:*:*:*:*:*:*:* OR *cpe:2.3:a:redhat:codeready_linux_builder_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_arm64_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_ibm_z_systems_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:codeready_linux_builder_for_power_little_endian_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:a:redhat:virtualization:4.0:*:*:*:*:*:*:* *cpe:2.3:a:redhat:virtualization_host:4.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux:9.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_eus:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_arm_64_eus:8.6_aarch64:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems_eus_s390x:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_for_power_big_endian_eus:8.6_ppc64le:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_aus:8.6:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux_server_tus:8.6:*:*:*:*:*:*:* -
CVE Modified by [email protected]
Jan. 03, 2024
Action Type Old Value New Value Added Reference Red Hat, Inc. https://access.redhat.com/errata/RHSA-2024:0033 [No types assigned] -
CVE Modified by [email protected]
Dec. 21, 2023
Action Type Old Value New Value Added Reference Red Hat, Inc. http://packetstormsecurity.com/files/176288/Glibc-Tunables-Privilege-Escalation.html [No types assigned] -
CVE Modified by [email protected]
Nov. 07, 2023
Action Type Old Value New Value Added CWE Red Hat, Inc. CWE-122 -
CVE Modified by [email protected]
Oct. 14, 2023
Action Type Old Value New Value Added Reference http://www.openwall.com/lists/oss-security/2023/10/14/6 [No Types Assigned] -
CVE Modified by [email protected]
Oct. 14, 2023
Action Type Old Value New Value Added Reference http://www.openwall.com/lists/oss-security/2023/10/14/5 [No Types Assigned] -
CVE Modified by [email protected]
Oct. 14, 2023
Action Type Old Value New Value Added Reference http://www.openwall.com/lists/oss-security/2023/10/14/3 [No Types Assigned] -
CVE Modified by [email protected]
Oct. 14, 2023
Action Type Old Value New Value Added Reference http://www.openwall.com/lists/oss-security/2023/10/13/11 [No Types Assigned] -
CVE Modified by [email protected]
Oct. 13, 2023
Action Type Old Value New Value Added Reference https://security.netapp.com/advisory/ntap-20231013-0006/ [No Types Assigned] -
CVE Modified by [email protected]
Oct. 06, 2023
Action Type Old Value New Value Added Reference http://packetstormsecurity.com/files/174986/glibc-ld.so-Local-Privilege-Escalation.html [No Types Assigned] -
CVE Modified by [email protected]
Oct. 06, 2023
Action Type Old Value New Value Added Reference http://seclists.org/fulldisclosure/2023/Oct/11 [No Types Assigned] -
CVE Modified by [email protected]
Oct. 05, 2023
Action Type Old Value New Value Added Reference https://access.redhat.com/errata/RHSA-2023:5476 [No Types Assigned] -
Initial Analysis by [email protected]
Oct. 05, 2023
Action Type Old Value New Value Added CVSS V3.1 NIST AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H Changed Reference Type http://www.openwall.com/lists/oss-security/2023/10/03/2 No Types Assigned http://www.openwall.com/lists/oss-security/2023/10/03/2 Exploit, Mailing List Changed Reference Type http://www.openwall.com/lists/oss-security/2023/10/03/3 No Types Assigned http://www.openwall.com/lists/oss-security/2023/10/03/3 Mailing List, Patch Changed Reference Type http://www.openwall.com/lists/oss-security/2023/10/05/1 No Types Assigned http://www.openwall.com/lists/oss-security/2023/10/05/1 Mailing List, Third Party Advisory Changed Reference Type https://access.redhat.com/errata/RHSA-2023:5453 No Types Assigned https://access.redhat.com/errata/RHSA-2023:5453 Third Party Advisory Changed Reference Type https://access.redhat.com/errata/RHSA-2023:5454 No Types Assigned https://access.redhat.com/errata/RHSA-2023:5454 Third Party Advisory Changed Reference Type https://access.redhat.com/errata/RHSA-2023:5455 No Types Assigned https://access.redhat.com/errata/RHSA-2023:5455 Third Party Advisory Changed Reference Type https://access.redhat.com/security/cve/CVE-2023-4911 No Types Assigned https://access.redhat.com/security/cve/CVE-2023-4911 Third Party Advisory Changed Reference Type https://bugzilla.redhat.com/show_bug.cgi?id=2238352 No Types Assigned https://bugzilla.redhat.com/show_bug.cgi?id=2238352 Issue Tracking, Patch, Third Party Advisory Changed Reference Type https://lists.fedoraproject.org/archives/list/[email protected]/message/4DBUQRRPB47TC3NJOUIBVWUGFHBJAFDL/ No Types Assigned https://lists.fedoraproject.org/archives/list/[email protected]/message/4DBUQRRPB47TC3NJOUIBVWUGFHBJAFDL/ Mailing List Changed Reference Type https://lists.fedoraproject.org/archives/list/[email protected]/message/DFG4P76UHHZEWQ26FWBXG76N2QLKKPZA/ No Types Assigned https://lists.fedoraproject.org/archives/list/[email protected]/message/DFG4P76UHHZEWQ26FWBXG76N2QLKKPZA/ Exploit, Mailing List Changed Reference Type https://lists.fedoraproject.org/archives/list/[email protected]/message/NDAQWHTSVOCOZ5K6KPIWKRT3JX4RTZUR/ No Types Assigned https://lists.fedoraproject.org/archives/list/[email protected]/message/NDAQWHTSVOCOZ5K6KPIWKRT3JX4RTZUR/ Mailing List Changed Reference Type https://security.gentoo.org/glsa/202310-03 No Types Assigned https://security.gentoo.org/glsa/202310-03 Third Party Advisory Changed Reference Type https://www.debian.org/security/2023/dsa-5514 No Types Assigned https://www.debian.org/security/2023/dsa-5514 Third Party Advisory Changed Reference Type https://www.qualys.com/2023/10/03/cve-2023-4911/looney-tunables-local-privilege-escalation-glibc-ld-so.txt No Types Assigned https://www.qualys.com/2023/10/03/cve-2023-4911/looney-tunables-local-privilege-escalation-glibc-ld-so.txt Exploit Changed Reference Type https://www.qualys.com/cve-2023-4911/ No Types Assigned https://www.qualys.com/cve-2023-4911/ Third Party Advisory Added CWE NIST CWE-787 Added CPE Configuration OR *cpe:2.3:a:gnu:glibc:-:*:*:*:*:*:*:* Added CPE Configuration OR *cpe:2.3:o:fedoraproject:fedora:37:*:*:*:*:*:*:* *cpe:2.3:o:fedoraproject:fedora:38:*:*:*:*:*:*:* *cpe:2.3:o:fedoraproject:fedora:39:*:*:*:*:*:*:* Added CPE Configuration OR *cpe:2.3:a:redhat:virtualization:4.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:* *cpe:2.3:o:redhat:enterprise_linux:9.0:*:*:*:*:*:*:* -
CVE Modified by [email protected]
Oct. 05, 2023
Action Type Old Value New Value Added Reference https://access.redhat.com/errata/RHSA-2023:5454 [No Types Assigned] Added Reference https://access.redhat.com/errata/RHSA-2023:5453 [No Types Assigned] Added Reference https://access.redhat.com/errata/RHSA-2023:5455 [No Types Assigned] -
CVE Modified by [email protected]
Oct. 05, 2023
Action Type Old Value New Value Added Reference http://www.openwall.com/lists/oss-security/2023/10/05/1 [No Types Assigned] -
CVE Modified by [email protected]
Oct. 04, 2023
Action Type Old Value New Value Added Reference https://lists.fedoraproject.org/archives/list/[email protected]/message/DFG4P76UHHZEWQ26FWBXG76N2QLKKPZA/ [No Types Assigned] -
CVE Modified by [email protected]
Oct. 04, 2023
Action Type Old Value New Value Added Reference https://lists.fedoraproject.org/archives/list/[email protected]/message/NDAQWHTSVOCOZ5K6KPIWKRT3JX4RTZUR/ [No Types Assigned] Added Reference https://lists.fedoraproject.org/archives/list/[email protected]/message/4DBUQRRPB47TC3NJOUIBVWUGFHBJAFDL/ [No Types Assigned] -
CVE Modified by [email protected]
Oct. 04, 2023
Action Type Old Value New Value Added Reference https://security.gentoo.org/glsa/202310-03 [No Types Assigned] -
CVE Modified by [email protected]
Oct. 03, 2023
Action Type Old Value New Value Added Reference https://www.debian.org/security/2023/dsa-5514 [No Types Assigned] -
CVE Modified by [email protected]
Oct. 03, 2023
Action Type Old Value New Value Added Reference http://www.openwall.com/lists/oss-security/2023/10/03/3 [No Types Assigned] Added Reference http://www.openwall.com/lists/oss-security/2023/10/03/2 [No Types Assigned]
Vulnerability Scoring Details
Base CVSS Score: 7.8
Exploit Prediction
EPSS is a daily estimate of the probability of exploitation activity being observed over the next 30 days.
64.66 }} 0.06%
score
0.98418
percentile


