CVE-2024-29847
Ivanti EPM Deserialization RCE
Description
Deserialization of untrusted data in the agent portal of Ivanti EPM before 2022 SU6, or the 2024 September update allows a remote unauthenticated attacker to achieve remote code execution.
INFO
Published Date :
Sept. 12, 2024, 2:15 a.m.
Last Modified :
Sept. 12, 2024, 10:35 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.0 | CRITICAL | [email protected] | ||||
| CVSS 3.1 | CRITICAL | [email protected] |
Solution
- Refer to the vendor advisory for remediation details.
- Apply the appropriate security update or patch.
Public PoC/Exploit Available at Github
CVE-2024-29847 has a 3 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-29847.
| URL | Resource |
|---|---|
| https://forums.ivanti.com/s/article/Security-Advisory-EPM-September-2024-for-EPM-2024-and-EPM-2022 | Vendor Advisory |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-29847 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-29847
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
A collection of Vulnerability Research and Reverse Engineering writeups.
Exploit for CVE-2024-29847
ASP.NET
一个 CVE 漏洞预警知识库,无 exp/poc,部分包含修复方案。A knowledge base of CVE security vulnerability, no PoCs/exploits.
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-29847 vulnerability anywhere in the article.

-
Daily CyberSecurity
CVE-2026-1603: Remote Unauthenticated Attacker Can Steal Ivanti EPM Secrets
Ivanti has rolled out important security updates for its Endpoint Manager (EPM), addressing a pair of vulnerabilities that could expose sensitive credentials to hackers. The release fixes one high-sev ... Read more

-
Daily CyberSecurity
Critical Ivanti EPM Flaw (CVE-2025-10573) Risks Admin Session Hijack and Unauthenticated RCE
Ivanti has rolled out an urgent security update for its Endpoint Manager (EPM) solution, patching a cluster of severe vulnerabilities that could allow attackers to execute arbitrary code or hijack adm ... Read more

-
Daily CyberSecurity
EPM Poisoning (CVE-2025-49760): New Windows RPC Exploit Hijacks Services, Allowing Full Active Directory Compromise, PoC Releases
Security researcher Ron Ben Yizhak from SafeBreach Labs has uncovered a novel attack technique dubbed Endpoint Mapper (EPM) Poisoning, which exploits a core weakness in the Windows Remote Procedure Ca ... Read more

-
Help Net Security
PoC exploit for Ivanti Endpoint Manager vulnerabilities released (CVE-2024-13159)
A proof-of-concept (PoC) exploit for four critical Ivanti Endpoint Manager vulnerabilities has been released by Horizon3.ai researchers. The vulnerabilities – CVE-2024-10811, CVE-2024-13161, CVE-2024- ... Read more

-
TheCyberThrone
Ivanti Addressed Multiple Vulnerabilities as part of November 2024 advisories
Ivanti has released trove of security updates as part of November 2024 security advisoryIvanti Endpoint ManagerThe most critical vulnerability, CVE-2024-50330 with a CVSS score of 9.8, is a SQL injec ... Read more

-
Cybersecurity News
Ivanti Connect Secure, Policy Secure and Secure Access Client Affected by Critical Vulnerabilities
Ivanti has released urgent security updates to address a range of vulnerabilities, including critical remote code execution (RCE) flaws, in its Connect Secure, Policy Secure, and Secure Access Client ... Read more

-
Cybersecurity News
CVE-2024-50330 (CVSS 9.8): Unpatched Ivanti Endpoint Manager Vulnerable to RCE Attacks
Software company Ivanti has released urgent security updates for its Endpoint Manager to address a range of vulnerabilities, including several that could allow for remote code execution (RCE).The vuln ... Read more

-
Cybersecurity News
CISA Adds Three Actively Exploited Security Vulnerabilities to KEV Catalog, Urges Urgent Patching
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added three new security flaws to its Known Exploited Vulnerabilities (KEV) catalog, following confirmed reports of active exploita ... Read more

-
Cybersecurity News
CVE-2024-37404: Critical RCE Flaw Discovered in Ivanti Connect Secure & Policy Secure, PoC Published
Reverse Shell - Running as root User | Image: Richard WarrenIvanti has addressed a critical remote code execution (RCE) vulnerability affecting its Connect Secure and Policy Secure products, as report ... Read more
-
Cybersecurity News
Active Exploits Target Zimbra Collaboration: Over 19K Systems Vulnerable to CVE-2024-45519
Image: The Shadowserver FoundationEnterprise security firm Proofpoint has issued a critical warning regarding active exploitation attempts against Synacor’s Zimbra Collaboration platform. A recently d ... Read more
-
Cybersecurity News
0-Day Flaw CVE-2024-38200 in Microsoft Office Exposes NTLMv2 Hashes: PoC Exploit Released
A discovered zero-day vulnerability is putting Microsoft Office users at risk. Security researcher Metin Yunus Kandemir recently published the technical details and a proof-of-concept (PoC) exploit th ... Read more
-
Cybersecurity News
CVE-2024-29824: Critical Vulnerability in Ivanti Endpoint Manager Actively Exploited, PoC Published
Successfully exploiting using Burp | Image: Horizon3The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert regarding the active exploitation of a critical vulnerability ... Read more
-
Cybersecurity News
CISA Warns of Actively Exploited Ivanti vTM Flaw CVE-2024-7593 (CVSS 9.8), PoC Published
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent advisory regarding an actively exploited security vulnerability impacting Ivanti Virtual Traffic Manager (vTM), a ... Read more

-
Cybersecurity News
CVE-2024-7490: Urgent Warning for IoT Devices Using Microchip ASF, No Patch Available
The latest vulnerability disclosure identifies a significant security flaw in the Microchip Advanced Software Framework (ASF), specifically within its tinydhcp server implementation. This vulnerabilit ... Read more
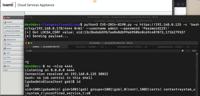
-
Cybersecurity News
PoC Exploit Releases for Exploited Vulnerability CVE-2024-8190 in Ivanti Cloud Services Appliance
Authenticated Command Injection | Image: Horizon3.aiA proof-of-concept (PoC) exploit for CVE-2024-8190, an exploited OS command injection vulnerability in Ivanti Cloud Services Appliance, is now publi ... Read more

-
Help Net Security
PoC exploit for exploited Ivanti Cloud Services Appliance flaw released (CVE-2024-8190)
CVE-2024-8190, an OS command injection vulnerability in Ivanti Cloud Services Appliance (CSA) v4.6, is under active exploitation. Details about the attacks are still unknown, but there may be more in ... Read more

-
TheCyberThrone
CISA KEV Update September 2024 -Part V
The US CISA adds two vulnerabilities to its Known Exploited Vulnerabilities Catalog based on the evidence of active exploitationThe first vulnerability tracked as CVE-2024-43461, Microsoft Windows MSH ... Read more
-
Cybersecurity News
166k+ Projects at Risk: AutoGPT’s Critical Vulnerability Explained – CVE-2024-6091 (CVSS 9.8)
A significant security vulnerability has been discovered in AutoGPT, a powerful AI tool designed to automate tasks through intelligent agents. With over 166k stars on GitHub, AutoGPT has gained popula ... Read more
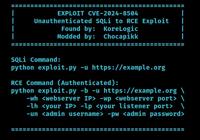
-
Cybersecurity News
Critical Flaws Found in VICIdial Contact Center Suite: CVE-2024-8503 and CVE-2024-8504, PoC Published
In a concerning development for call centers using VICIdial, a popular open-source contact center solution, two high-severity security vulnerabilities have been discovered that could lead to severe da ... Read more

-
BleepingComputer
Exploit code released for critical Ivanti RCE flaw, patch now
A proof-of-concept (PoC) exploit for CVE-2024-29847, a critical remote code execution (RCE) vulnerability in Ivanti Endpoint Manager, is now publicly released, making it crucial to update devices. The ... Read more
The following table lists the changes that have been made to the
CVE-2024-29847 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Sep. 12, 2024
Action Type Old Value New Value Added CWE CISA-ADP CWE-502 -
Initial Analysis by [email protected]
Sep. 12, 2024
Action Type Old Value New Value Added CVSS V3.1 NIST AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Changed Reference Type https://forums.ivanti.com/s/article/Security-Advisory-EPM-September-2024-for-EPM-2024-and-EPM-2022 No Types Assigned https://forums.ivanti.com/s/article/Security-Advisory-EPM-September-2024-for-EPM-2024-and-EPM-2022 Vendor Advisory Added CWE NIST CWE-502 Added CPE Configuration OR *cpe:2.3:a:ivanti:endpoint_manager:*:*:*:*:*:*:*:* versions up to (excluding) 2022 *cpe:2.3:a:ivanti:endpoint_manager:2022:-:*:*:*:*:*:* *cpe:2.3:a:ivanti:endpoint_manager:2022:su1:*:*:*:*:*:* *cpe:2.3:a:ivanti:endpoint_manager:2022:su2:*:*:*:*:*:* *cpe:2.3:a:ivanti:endpoint_manager:2022:su3:*:*:*:*:*:* *cpe:2.3:a:ivanti:endpoint_manager:2022:su4:*:*:*:*:*:* *cpe:2.3:a:ivanti:endpoint_manager:2022:su5:*:*:*:*:*:* *cpe:2.3:a:ivanti:endpoint_manager:2024:-:*:*:*:*:*:* -
CVE Received by [email protected]
Sep. 12, 2024
Action Type Old Value New Value Added Description Deserialization of untrusted data in the agent portal of Ivanti EPM before 2022 SU6, or the 2024 September update allows a remote unauthenticated attacker to achieve remote code execution. Added Reference HackerOne https://forums.ivanti.com/s/article/Security-Advisory-EPM-September-2024-for-EPM-2024-and-EPM-2022 [No types assigned] Added CVSS V3 HackerOne AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H


