CVE-2024-34693
Apache Superset: Server arbitrary file read
Description
Improper Input Validation vulnerability in Apache Superset, allows for an authenticated attacker to create a MariaDB connection with local_infile enabled. If both the MariaDB server (off by default) and the local mysql client on the web server are set to allow for local infile, it's possible for the attacker to execute a specific MySQL/MariaDB SQL command that is able to read files from the server and insert their content on a MariaDB database table.This issue affects Apache Superset: before 3.1.3 and version 4.0.0 Users are recommended to upgrade to version 4.0.1 or 3.1.3, which fixes the issue.
INFO
Published Date :
June 20, 2024, 9:15 a.m.
Last Modified :
Feb. 13, 2025, 6:18 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | MEDIUM | [email protected] | ||||
| CVSS 3.1 | MEDIUM | [email protected] |
Public PoC/Exploit Available at Github
CVE-2024-34693 has a 3 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-34693.
| URL | Resource |
|---|---|
| http://www.openwall.com/lists/oss-security/2024/06/20/1 | Mailing List |
| https://lists.apache.org/thread/1803x1s34m7r71h1k0q1njol8k6fmyon | Mailing List |
| http://www.openwall.com/lists/oss-security/2024/06/20/1 | Mailing List |
| https://lists.apache.org/thread/1803x1s34m7r71h1k0q1njol8k6fmyon | Mailing List |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-34693 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-34693
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
None
Python
None
CVE-2024-34693: Server Arbitrary File Read in Apache Superset
0-day arbitrary-file-read cve cves cve-2024-34693
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-34693 vulnerability anywhere in the article.

-
Daily CyberSecurity
CVE-2025-48912: Apache Superset Flaw Allows Row-Level Security Bypass via SQL Injection
A serious security vulnerability has been discovered in Apache Superset, a widely used open-source data exploration and visualization platform. The flaw exposes sensitive datasets to unauthorized acce ... Read more

-
Cybersecurity News
CVE-2024-55633: Apache Superset Vulnerability Exposes Sensitive Data to Unauthorized Modification
A newly discovered vulnerability in Apache Superset, a popular open-source business intelligence platform, could allow attackers to gain unauthorized write access to sensitive data. Tracked as CVE-202 ... Read more

-
Cybersecurity News
Apache Superset Patches Multi Security Flaws in Latest Release
The Apache Software Foundation has announced the release of Apache Superset 4.1.0, an important update that addresses three significant security vulnerabilities affecting the widely used open-source b ... Read more

-
Cybersecurity News
Linux Leaps to Record 4.44% Market Share: Open-Source OS Hits All-Time High in July
Recent data from StatCounter indicates that Linux’s market share has ascended to an unprecedented 4.44% in July. This marks a substantial increase from the 3.12% recorded during the corresponding peri ... Read more

-
Cybersecurity News
Azure Kubernetes Services at Risk: “WireServing” Threat Revealed
Permissions granted to the embedded TLS certificatesA newly discovered vulnerability in Azure Kubernetes Services (AKS) has been revealed by Mandiant, a leading cybersecurity firm. The vulnerability, ... Read more

-
Cybersecurity News
Congress Scrutinizes TP-Link Routers Over Cybersecurity Concerns
Two members of Congress have urged the U.S. Department of Commerce to investigate the cybersecurity risks associated with Wi-Fi routers manufactured by the Chinese company TP-Link Technologies, and th ... Read more
-
Cybersecurity News
Xeon Sender Abuses SaaS APIs for Massive SMS Attacks
SVG SMS variant of Xeon Sender | Image: SentinelOneSecurity researchers at SentinelOne have uncovered a new cloud-based attack tool called Xeon Sender (aka XeonV5, SVG Sender) that enables threat acto ... Read more

-
Cybersecurity News
TA453 Deploys New BlackSmith Malware Toolset in Phishing Attack on Religious Figure
Cybersecurity firm Proofpoint has uncovered a new phishing campaign by the Iranian-backed threat actor TA453 (aka Charming Kitten, Mint Sandstorm, APT42). In this campaign, TA453 impersonated the Inst ... Read more
-
Cybersecurity News
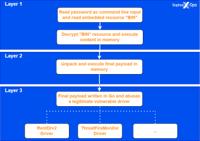
EDRKillShifter: A New EDR-Killing Tool in Ransomware Attack
High-level overview of the loader execution process | Image: SophosSophos researchers have discovered a new threat: EDRKillShifter, a sophisticated tool designed to dismantle endpoint detection and re ... Read more

-
Cybersecurity News
Django Releases Security Updates to Address Critical Flaw (CVE-2024-42005, CVSS 9.8)
The Django team has issued security updates for Django 5.0.8 and 4.2.15 to address multiple vulnerabilities, including potential denial-of-service (DoS) attacks and a critical SQL injection vulnerabil ... Read more
The following table lists the changes that have been made to the
CVE-2024-34693 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
CVE Modified by [email protected]
Feb. 13, 2025
Action Type Old Value New Value Changed Description Improper Input Validation vulnerability in Apache Superset, allows for an authenticated attacker to create a MariaDB connection with local_infile enabled. If both the MariaDB server (off by default) and the local mysql client on the web server are set to allow for local infile, it's possible for the attacker to execute a specific MySQL/MariaDB SQL command that is able to read files from the server and insert their content on a MariaDB database table.This issue affects Apache Superset: before 3.1.3 and version 4.0.0 Users are recommended to upgrade to version 4.0.1 or 3.1.3, which fixes the issue. Improper Input Validation vulnerability in Apache Superset, allows for an authenticated attacker to create a MariaDB connection with local_infile enabled. If both the MariaDB server (off by default) and the local mysql client on the web server are set to allow for local infile, it's possible for the attacker to execute a specific MySQL/MariaDB SQL command that is able to read files from the server and insert their content on a MariaDB database table.This issue affects Apache Superset: before 3.1.3 and version 4.0.0 Users are recommended to upgrade to version 4.0.1 or 3.1.3, which fixes the issue. -
Initial Analysis by [email protected]
Feb. 11, 2025
Action Type Old Value New Value Added CVSS V3.1 NIST AV:N/AC:H/PR:L/UI:N/S:U/C:H/I:N/A:N Added CWE NIST NVD-CWE-noinfo Added CPE Configuration OR *cpe:2.3:a:apache:superset:*:*:*:*:*:*:*:* versions up to (excluding) 3.1.3 *cpe:2.3:a:apache:superset:*:*:*:*:*:*:*:* versions from (including) 4.0.0 up to (excluding) 4.0.1 Changed Reference Type http://www.openwall.com/lists/oss-security/2024/06/20/1 No Types Assigned http://www.openwall.com/lists/oss-security/2024/06/20/1 Mailing List Changed Reference Type http://www.openwall.com/lists/oss-security/2024/06/20/1 No Types Assigned http://www.openwall.com/lists/oss-security/2024/06/20/1 Mailing List Changed Reference Type https://lists.apache.org/thread/1803x1s34m7r71h1k0q1njol8k6fmyon No Types Assigned https://lists.apache.org/thread/1803x1s34m7r71h1k0q1njol8k6fmyon Mailing List Changed Reference Type https://lists.apache.org/thread/1803x1s34m7r71h1k0q1njol8k6fmyon No Types Assigned https://lists.apache.org/thread/1803x1s34m7r71h1k0q1njol8k6fmyon Mailing List -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Nov. 21, 2024
Action Type Old Value New Value Added Reference http://www.openwall.com/lists/oss-security/2024/06/20/1 Added Reference https://lists.apache.org/thread/1803x1s34m7r71h1k0q1njol8k6fmyon -
CVE Modified by [email protected]
Jun. 20, 2024
Action Type Old Value New Value Added Reference Apache Software Foundation http://www.openwall.com/lists/oss-security/2024/06/20/1 [No types assigned] -
CVE Received by [email protected]
Jun. 20, 2024
Action Type Old Value New Value Added Description Improper Input Validation vulnerability in Apache Superset, allows for an authenticated attacker to create a MariaDB connection with local_infile enabled. If both the MariaDB server (off by default) and the local mysql client on the web server are set to allow for local infile, it's possible for the attacker to execute a specific MySQL/MariaDB SQL command that is able to read files from the server and insert their content on a MariaDB database table.This issue affects Apache Superset: before 3.1.3 and version 4.0.0 Users are recommended to upgrade to version 4.0.1 or 3.1.3, which fixes the issue. Added Reference Apache Software Foundation https://lists.apache.org/thread/1803x1s34m7r71h1k0q1njol8k6fmyon [No types assigned] Added CWE Apache Software Foundation CWE-20 Added CVSS V3.1 Apache Software Foundation AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:N/A:N


