CVE-2024-36877
Micro-Star International Z- and B-series Motherboards SMI Write-What-Where Condition Vulnerability
Description
Micro-Star International Z-series motherboards (Z590, Z490, and Z790) and B-series motherboards (B760, B560, B660, and B460) with firmware 7D25v14, 7D25v17 to 7D25v19, and 7D25v1A to 7D25v1H was discovered to contain a write-what-where condition in the in the SW handler for SMI 0xE3. Motherboard's with the following chipsets are affected: Intel 300, Intel 400, Intel 500, Intel 600, Intel 700, AMD 300, AMD 400, AMD 500, AMD 600 and AMD 700.
INFO
Published Date :
Aug. 12, 2024, 4:15 p.m.
Last Modified :
March 13, 2025, 8:15 p.m.
Remotely Exploit :
No
Source :
[email protected]
Affected Products
The following products are affected by CVE-2024-36877
vulnerability.
Even if cvefeed.io is aware of the exact versions of the
products
that
are
affected, the information is not represented in the table below.
No affected product recoded yet
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | HIGH | 134c704f-9b21-4f2e-91b3-4a467353bcc0 |
Public PoC/Exploit Available at Github
CVE-2024-36877 has a 3 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-36877.
| URL | Resource |
|---|---|
| https://csr.msi.com/global/product-security-advisories | |
| https://jjensn.com/at-home-in-your-firmware/ |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-36877 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-36877
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
A collection of Vulnerability Research and Reverse Engineering writeups.
None
Exploit POC for CVE-2024-36877
C++
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-36877 vulnerability anywhere in the article.

-
Daily CyberSecurity
Critical AMI BMC Vulnerability: Patch Your ASUS Workstation Now
Veteran PC users are likely familiar with encountering messages from American Megatrends International (AMI) during system startup. AMI stands as a leading provider of BIOS and UEFI firmware solutions ... Read more

-
Cybersecurity News
Bumblebee Loader Resurfaces with New Infection Chain
In a recent report from Leandro Fróes, Senior Threat Research Engineer at Netskope, a new infection chain linked to the Bumblebee loader has been uncovered. First discovered by Google’s Threat Analysi ... Read more

-
Cybersecurity News
CVE-2024-45032 (CVSS 10): Siemens Issues Critical Security Patch for Industrial Edge Management
Siemens has released a critical security advisory for its Industrial Edge Management platform, warning of an Authorization Bypass vulnerability that could have serious implications for industrial netw ... Read more
-
Cybersecurity News
CVE-2024-7012 (CVSS 9.8): Critical Foreman Flaw Exposes Red Hat Satellite to Unauthorized Access
A critical vulnerability, CVE-2024-7012, has been discovered in Foreman, a widely used open-source lifecycle management tool. This authentication bypass flaw, with a CVSS score of 9.8 (the highest sev ... Read more

-
Cybersecurity News
D-Link Won’t Fix 4 RCE Vulnerabilities in DIR-846W Router
Four severe security flaws have been found in the D-Link DIR-846W router, leaving users potentially exposed to remote attacks even after the device has reached its end-of-life.Security researchers hav ... Read more
-
Cybersecurity News
Intel SGX Security Compromised: Root Provisioning Key Extracted
Recently, researcher Mark Ermolov has successfully extracted Intel’s SGX Fuse Key0, also known as the Root Provisioning Key. This key, introduced with Intel’s Skylake processors, is a cornerstone of I ... Read more
-
Cybersecurity News
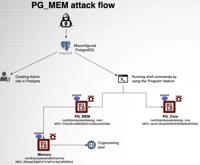
New PostgreSQL Threat: PG_MEM Malware Strikes Databases
Attack flow of PG_MEM | Image: Aqua NautilusA new and insidious threat has emerged, targeting the widely used PostgreSQL database management system. Aqua Nautilus researchers have identified a novel m ... Read more

-
Cybersecurity News
SonicWall Issues Urgent Patch for Critical Firewall Vulnerability (CVE-2024-40766)
SonicWall, a prominent network security provider, has released a security advisory warning users of a critical vulnerability (CVE-2024-40766) affecting their SonicOS operating system. The vulnerabilit ... Read more

-
Cybersecurity News
CVE-2024-36877 in MSI Motherboards Opens Door to Code Execution Attacks, PoC Published
MSI, a leading manufacturer of computer hardware, has recently disclosed a critical vulnerability, tracked as CVE-2024-36877, that affects a wide range of its motherboards. The vulnerability, residing ... Read more
The following table lists the changes that have been made to the
CVE-2024-36877 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Mar. 13, 2025
Action Type Old Value New Value Added CWE CWE-123 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 24, 2024
Action Type Old Value New Value Removed CWE CISA-ADP CWE-123 -
CVE Modified by [email protected]
Aug. 15, 2024
Action Type Old Value New Value Changed Description Micro-Star International Z-series motherboards (Z590, Z490, and Z790) and B-series motherboards (B760, B560, B660, and B460) with firmware 7D25v14, 7D25v17 to 7D25v19, and 7D25v1A to 7D25v1H was discovered to contain a write-what-where condition in the in the SW handler for SMI 0xE3. Micro-Star International Z-series motherboards (Z590, Z490, and Z790) and B-series motherboards (B760, B560, B660, and B460) with firmware 7D25v14, 7D25v17 to 7D25v19, and 7D25v1A to 7D25v1H was discovered to contain a write-what-where condition in the in the SW handler for SMI 0xE3. Motherboard's with the following chipsets are affected: Intel 300, Intel 400, Intel 500, Intel 600, Intel 700, AMD 300, AMD 400, AMD 500, AMD 600 and AMD 700. -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Aug. 13, 2024
Action Type Old Value New Value Added CWE CISA-ADP CWE-123 Added CVSS V3.1 CISA-ADP AV:L/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H -
CVE Received by [email protected]
Aug. 12, 2024
Action Type Old Value New Value Added Description Micro-Star International Z-series motherboards (Z590, Z490, and Z790) and B-series motherboards (B760, B560, B660, and B460) with firmware 7D25v14, 7D25v17 to 7D25v19, and 7D25v1A to 7D25v1H was discovered to contain a write-what-where condition in the in the SW handler for SMI 0xE3. Added Reference MITRE https://csr.msi.com/global/product-security-advisories [No types assigned] Added Reference MITRE https://jjensn.com/at-home-in-your-firmware/ [No types assigned]


