CVE-2024-37085
VMware ESXi Authentication Bypass Vulnerability - [Actively Exploited]
Description
VMware ESXi contains an authentication bypass vulnerability. A malicious actor with sufficient Active Directory (AD) permissions can gain full access to an ESXi host that was previously configured to use AD for user management https://blogs.vmware.com/vsphere/2012/09/joining-vsphere-hosts-to-active-directory.html by re-creating the configured AD group ('ESXi Admins' by default) after it was deleted from AD.
INFO
Published Date :
June 25, 2024, 3:15 p.m.
Last Modified :
Oct. 30, 2025, 7:52 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
VMware ESXi contains an authentication bypass vulnerability. A malicious actor with sufficient Active Directory (AD) permissions can gain full access to an ESXi host that was previously configured to use AD for user management by re-creating the configured AD group ('ESXi Admins' by default) after it was deleted from AD.
Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable.
Known Detected Jul 30, 2024
https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/24505; https://nvd.nist.gov/vuln/detail/CVE-2024-37085
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | MEDIUM | [email protected] | ||||
| CVSS 3.1 | HIGH | [email protected] |
Solution
- Upgrade to VMware ESXi 8.0 Update 3 or later.
Public PoC/Exploit Available at Github
CVE-2024-37085 has a 12 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-37085.
| URL | Resource |
|---|---|
| https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/24505 | Patch Vendor Advisory |
| https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/24505 | Patch Vendor Advisory |
| https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-37085 | US Government Resource |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-37085 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-37085
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
Digital forensics tools for triaging incidents on VMware ESXi servers.
Shell
Auto Scanner of AD
Dockerfile Python
Comprehensive Cyber Threat Intelligence Report for Threat Actor AKIRA
HTML
Threat hunting with KQL — mapping adversary behavior across the MITRE ATT&CK chain 🔗
Python
None
None
CVE-2024-37085 unauthenticated shell upload to full administrator on domain-joined esxi hypervisors.
CVE-2024-37085 VMware ESXi RCE Vulnerability
Python
Vulnerability Scanner for CVE-2024-37085 and Exploits ( For Educational Purpose only)
Python
A GitHub repo to store the blogs, tutorials, and research I read, along with a brief summary of what they were about.
JavaScript
A Huge Learning Resources with Labs For Offensive Security Players
api infrastructure learning security mobile web hack hacking owasp cybersecurity web-security mobile-security offensive offensive-security red-team owasp-top-10 redteam cloud-security api-security red-teaming
None
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-37085 vulnerability anywhere in the article.

-
BleepingComputer
The Hidden Risk in Virtualization: Why Hypervisors are a Ransomware Magnet
Author: Dray Agha, Senior Manager, Hunt & Response, at Huntress Labs Hypervisors are the backbone of modern virtualized environments, but when compromised, they can become a force multiplier for attac ... Read more
-
Huntress
Hardening the Hypervisor: Practical Defenses Against Ransomware Targeting ESXi
Hypervisors are the backbone of modern virtualized environments, but when compromised, they can become a force multiplier for attackers. A single breach at this layer can put dozens or even hundreds o ... Read more

-
The Cyber Express
Akira Ransomware Group Poses ‘Imminent Threat’ to Critical Infrastructure: CISA
The Akira ransomware group poses an “imminent threat to critical infrastructure,” the U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned today. CISA joined with the FBI, other U.S. ag ... Read more

-
Daily CyberSecurity
VMScape (CVE-2025-40300): A New CPU Flaw Threatens Cloud Security
Security researchers at ETH Zurich have published a study revealing how attackers can break through virtualization boundaries with a technique they call VMScope (CVE-2025-40300). By exploiting microar ... Read more
-
Google Cloud
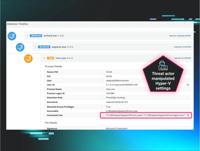
Beyond Convenience: Exposing the Risks of VMware vSphere Active Directory Integration
Written by: Stuart Carrera, Brian Meyer Executive Summary Broadcom's VMware vSphere product remains a popular choice for private cloud virtualization, underpinning critical infrastructure. Far from fa ... Read more

-
Help Net Security
Released: MITRE ATT&CK v17.0, now with ESXi attack TTPs
MITRE has released the latest version of its ATT&CK framework, which now also includes a new section (“matrix”) to cover the tactics, techniques and procedures (TTPs) used to target VMware ESXi hyperv ... Read more

-
Cyber Security News
VMware ESXi Vulnerabilities Exploited in Wild to Execute Malicious Code
VMware has issued a critical security advisory (VMSA-2025-0004) warning of active exploitation of three vulnerabilities in its ESXi, Workstation, and Fusion products. These flaws, CVE-2025-22224, CVE- ... Read more

-
Cybersecurity News
CVE-2025-0159 (CVSS 9.1): Critical IBM Storage Flaw Allows Authentication Bypass
IBM has issued a security bulletin disclosing two vulnerabilities affecting the graphical user interface (GUI) of several IBM Storage Virtualize products. These vulnerabilities, tracked as CVE-2025-01 ... Read more

-
The Register
Ransomware criminals love CISA's KEV list – and that's a bug, not a feature
Fresh research suggests attackers are actively monitoring databases of vulnerabilities that are known to be useful in carrying out ransomware attacks. GreyNoise's annual Mass Internet Exploitation Rep ... Read more

-
TheCyberThrone
Most Exploited Vulnerabilities in 2024 Top 20 Analysis
In 2024, the cybersecurity landscape saw a significant number of exploited vulnerabilities, highlighting the ongoing challenges organizations face in protecting their systems and data.Some key trends ... Read more

-
Kaspersky
IT threat evolution in Q3 2024. Non-mobile statistics
IT threat evolution in Q3 2024 IT threat evolution in Q3 2024. Non-mobile statistics IT threat evolution in Q3 2024. Mobile statistics The statistics presented here are based on detection verdicts by ... Read more

-
TheCyberThrone
The CyberThrone Most Exploited Vulnerabilities Top 10 – October 2024
Welcome to TheCyberThrone most exploited vulnerabilities review. This review is for the month of October 2024CVE-2024-21762: Fortinet FortiOS: Out-of-bounds WriteCVSS 3.1 score : 9.8 CISA KEV : Y ... Read more

-
The Hacker News
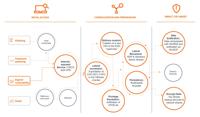
Ransomware Gangs Use LockBit's Fame to Intimidate Victims in Latest Attacks
Threat actors have been observed abusing Amazon S3 (Simple Storage Service) Transfer Acceleration feature as part of ransomware attacks designed to exfiltrate victim data and upload them to S3 buckets ... Read more
-
Cybersecurity News
Akira Ransomware Exploit CVE-2024-40766 in SonicWall SonicOS
The attack chain | Image: S-RMThe notorious Akira ransomware group continues to adapt and refine its methods, solidifying its position as one of the most significant threats in the cyber landscape. Ac ... Read more
-
Cybersecurity News
PoC Exploit Released for Windows Hyper-V Zero-Day Vulnerability CVE-2024-38080
Security researcher Pwndorei published a detailed analysis alongside a proof-of-concept (PoC) exploit code for a patched zero-day vulnerability in Windows Hyper-V, tracked as CVE-2024-38080. This crit ... Read more

-
Cybersecurity News
BlackByte Ransomware Group Exploits VMware CVE-2024-37085 Flaw, Shifts Tactics
The BlackByte ransomware group has re-emerged with an unsettling surge in activity and a refined set of tactics, techniques, and procedures (TTPs) that pose a heightened risk to organizations. Cisco T ... Read more

-
Hackread - Latest Cybersecurity, Tech, Crypto & Hacking News
BlackByte Ransomware Exploits New VMware Flaw in VPN-Based Attacks
BlackByte ransomware group is leveraging a newly discovered VMware ESXi vulnerability and VPN access to launch a new wave of attacks. Cisco Talos reveals the group’s tactics, urging organizations to p ... Read more

-
Dark Reading
BlackByte Targets ESXi Bug With Ransomware to Access Virtual Assets
Source: mayam_studio via ShutterstockThreat actors using the infamous BlackByte ransomware strain have joined the rapidly growing number of cybercriminals targeting a recent authentication bypass vuln ... Read more

-
The Hacker News
BlackByte Ransomware Exploits VMware ESXi Flaw in Latest Attack Wave
The threat actors behind the BlackByte ransomware group have been observed likely exploiting a recently patched security flaw impacting VMware ESXi hypervisors, while also leveraging various vulnerabl ... Read more

-
Help Net Security
BlackByte affiliates use new encryptor and new TTPs
BlackByte, the ransomware-as-a-service gang believed to be one of Conti’s splinter groups, has (once again) created a new iteration of its encryptor. “Talos observed some differences in the recent Bla ... Read more
The following table lists the changes that have been made to the
CVE-2024-37085 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Oct. 30, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-37085 Types: US Government Resource -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-37085 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-37085 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-37085 -
Modified Analysis by [email protected]
Dec. 20, 2024
Action Type Old Value New Value Changed CPE Configuration OR *cpe:2.3:a:vmware:cloud_foundation:*:*:*:*:*:*:*:* versions from (including) 4.0 up to (including) 5.2 *cpe:2.3:o:vmware:esxi:7.0:*:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:-:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:a:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:b:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:c:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1a:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1c:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1d:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_2:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_2b:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_2c:*:*:*:*:*:* OR *cpe:2.3:a:vmware:cloud_foundation:*:*:*:*:*:*:*:* versions from (including) 4.0 up to (excluding) 5.2 *cpe:2.3:o:vmware:esxi:7.0:*:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:-:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:a:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:b:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:c:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1a:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1c:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1d:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_2:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_2b:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_2c:*:*:*:*:*:* -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Nov. 21, 2024
Action Type Old Value New Value Added Reference https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/24505 -
Modified Analysis by [email protected]
Aug. 08, 2024
Action Type Old Value New Value Removed CWE NIST NVD-CWE-Other Added CWE NIST CWE-287 Changed CPE Configuration OR *cpe:2.3:a:vmware:cloud_foundation:*:*:*:*:*:*:*:* versions from (including) 4.0 up to (including) 4.5.2 *cpe:2.3:a:vmware:cloud_foundation:*:*:*:*:*:*:*:* versions from (including) 5.0 up to (excluding) 5.2 *cpe:2.3:o:vmware:esxi:7.0:*:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:-:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:a:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:b:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:c:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1a:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1c:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1d:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_2:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_2b:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_2c:*:*:*:*:*:* OR *cpe:2.3:a:vmware:cloud_foundation:*:*:*:*:*:*:*:* versions from (including) 4.0 up to (including) 5.2 *cpe:2.3:o:vmware:esxi:7.0:*:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:-:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:a:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:b:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:c:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1a:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1c:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1d:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_2:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_2b:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_2c:*:*:*:*:*:* -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Aug. 01, 2024
Action Type Old Value New Value Added CWE CISA-ADP CWE-305 -
Initial Analysis by [email protected]
Jul. 31, 2024
Action Type Old Value New Value Added CVSS V3.1 NIST AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H Changed Reference Type https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/24505 No Types Assigned https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/24505 Patch, Vendor Advisory Added CWE NIST NVD-CWE-Other Added CPE Configuration OR *cpe:2.3:a:vmware:cloud_foundation:*:*:*:*:*:*:*:* versions from (including) 4.0 up to (including) 4.5.2 *cpe:2.3:a:vmware:cloud_foundation:*:*:*:*:*:*:*:* versions from (including) 5.0 up to (excluding) 5.2 *cpe:2.3:o:vmware:esxi:7.0:*:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:-:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:a:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:b:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:c:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1a:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1c:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_1d:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_2:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_2b:*:*:*:*:*:* *cpe:2.3:o:vmware:esxi:8.0:update_2c:*:*:*:*:*:* -
CVE CISA KEV Update by 9119a7d8-5eab-497f-8521-727c672e3725
Jul. 31, 2024
Action Type Old Value New Value Added Date Added 2024-07-30 Added Required Action Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable. Added Due Date 2024-08-20 Added Vulnerability Name VMware ESXi Authentication Bypass Vulnerability -
CVE Received by [email protected]
Jun. 25, 2024
Action Type Old Value New Value Added Description VMware ESXi contains an authentication bypass vulnerability. A malicious actor with sufficient Active Directory (AD) permissions can gain full access to an ESXi host that was previously configured to use AD for user management https://blogs.vmware.com/vsphere/2012/09/joining-vsphere-hosts-to-active-directory.html by re-creating the configured AD group ('ESXi Admins' by default) after it was deleted from AD. Added Reference VMware https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/24505 [No types assigned] Added CVSS V3.1 VMware AV:N/AC:L/PR:H/UI:R/S:U/C:H/I:H/A:H