CVE-2024-39717
Versa Director Dangerous File Type Upload Vulnerability - [Actively Exploited]
Description
The Versa Director GUI provides an option to customize the look and feel of the user interface. This option is only available for a user logged with Provider-Data-Center-Admin or Provider-Data-Center-System-Admin. (Tenant level users do not have this privilege). The “Change Favicon” (Favorite Icon) option can be mis-used to upload a malicious file ending with .png extension to masquerade as image file. This is possible only after a user with Provider-Data-Center-Admin or Provider-Data-Center-System-Admin has successfully authenticated and logged in.
INFO
Published Date :
Aug. 22, 2024, 7:15 p.m.
Last Modified :
Oct. 30, 2025, 8:40 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
The Versa Director GUI contains an unrestricted upload of file with dangerous type vulnerability that allows administrators with Provider-Data-Center-Admin or Provider-Data-Center-System-Admin privileges to customize the user interface. The “Change Favicon” (Favorite Icon) enables the upload of a .png file, which can be exploited to upload a malicious file with a .png extension disguised as an image.
Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable.
https://versa-networks.com/blog/versa-security-bulletin-update-on-cve-2024-39717-versa-director-dangerous-file-type-upload-vulnerability/; https://nvd.nist.gov/vuln/detail/CVE-2024-39717
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.0 | MEDIUM | [email protected] | ||||
| CVSS 3.1 | HIGH | [email protected] |
Solution
- Upgrade to Versa Director 22.1.4 or later.
Public PoC/Exploit Available at Github
CVE-2024-39717 has a 5 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-39717.
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-39717 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-39717
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
None
Interactive 3D visualization of China's Volt Typhoon APT attacking US critical infrastructure. Shows real 72-hour attack chain from CVE-2024-39717 exploit to water/power grid compromise. Based on CISA advisories & Microsoft threat intel.
HTML JavaScript CSS
A YARA rule to detect VersaMem malware samples
YARA
Ostorlab KEV: One-command to detect most remotely known exploitable vulnerabilities. Sourced from CISA KEV, Google's Tsunami, Ostorlab's Asteroid and Bug Bounty programs.
cisa-kev vulnerability 0day cisa exploits
None
Python Jupyter Notebook HTML
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-39717 vulnerability anywhere in the article.

-
Cybersecurity News
Australia Bans Kaspersky Products from Government Systems, Citing “Unacceptable Security Risk”
The Australian Government has issued a new directive banning the use of Kaspersky Lab products and web services across all government systems and devices. The directive, issued by the Department of Ho ... Read more

-
The Register
China's cyber intrusions took a sinister turn in 2024
The Chinese government's intrusions into America's telecommunications and other critical infrastructure networks this year appears to signal a shift from cyberspying as usual to prepping for destructi ... Read more

-
The Cyber Express
Microsoft, Ivanti, and More: 2024 KEV Catalog Highlights Vendor Vulnerabilities
In 2024, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) continued to build on its critical cybersecurity initiative by expanding its Known Exploited Vulnerabilities (KEV) catalog. Th ... Read more

-
Cybersecurity News
Volt Typhoon: Chinese State-Sponsored APT Targets U.S. Critical Infrastructure
The Tenable Security Response Team has uncovered critical details about Volt Typhoon, a state-sponsored Advanced Persistent Threat (APT) group linked to the People’s Republic of China. The group has b ... Read more

-
Cybersecurity News
CVE-2024-42450 (CVSS 10): Versa Networks Addresses Critical Vulnerability in Versa Director
Versa Networks has issued a security advisory addressing a critical vulnerability (CVE-2024-42450) affecting its Versa Director software. The vulnerability, which carries a CVSS score of 10, could all ... Read more

-
SentinelOne
The Good, the Bad and the Ugly in Cybersecurity – Week 46
The Good | Extortionist Sentenced to 10 Years For Cybercrimes Against U.S. Medical Clinics This week, the FBI sentenced Robert Purbeck to 10 years in prison for stealing personal data from over 132,00 ... Read more

-
The Register
China's Volt Typhoon crew and its botnet surge back with a vengeance
China's Volt Typhoon crew and its botnet are back, compromising old Cisco routers once again to break into critical infrastructure networks and kick off cyberattacks, according to security researchers ... Read more

-
The Register
China's Volt Typhoon reportedly breached Singtel in 'test-run' for US telecom attacks
Chinese government cyberspies Volt Typhoon reportedly breached Singapore Telecommunications over the summer as part of their ongoing attacks against critical infrastructure operators. The digital brea ... Read more

-
The Hacker News
China Accuses U.S. of Fabricating Volt Typhoon to Hide Its Own Hacking Campaigns
China's National Computer Virus Emergency Response Center (CVERC) has doubled down on claims that the threat actor known as the Volt Typhoon is a fabrication of the U.S. and its allies. The agency, in ... Read more
-
Cybersecurity News
Proxmox Virtual Environment and Mail Gateway Exposed to Critical API Vulnerability
A critical vulnerability has been identified in Proxmox Virtual Environment (VE) and Proxmox Mail Gateway (PMG) that could allow unauthorized access to sensitive files and potentially lead to a full s ... Read more

-
The Cyber Express
Versa Director Flaw Could Lead to API Attacks, Token Theft
Vulnerabilities in Versa Director are never a small matter, as the platform manages network configurations for Versa’s SD-WAN software – which is often used by internet service providers (ISPs) and ma ... Read more

-
Cybersecurity News
Versa Networks Exposes Critical API Vulnerability in Versa Director (CVE-2024-45229)
Versa Networks has issued a security advisory regarding a vulnerability discovered in its Versa Director product, CVE-2024-45229. This vulnerability, which carries a CVSS score of 6.6, could potential ... Read more
-
Cybersecurity News
Zero-Click Calendar Invite: Critical macOS Vulnerability Chain Uncovered
In a recent analysis, security researcher Mikko Kenttälä exposed a critical zero-click vulnerability chain in macOS, potentially affecting millions of users. This exploit, dubbed the “Zero-Click Calen ... Read more

-
Dark Reading
When Startup Founders Should Start Thinking About Cybersecurity
Source: Illia Uriadnikov via Alamy Stock PhotoIt was a tale of two startups."A company that I invested in — about, oh, five years ago — happened to be in the proptech [property technology] space," sai ... Read more

-
TheCyberThrone
CISA KEV Update Part II – September 2024.
The US CISA added below vulnerabilities to the Known Exploited Vulnerability Catalog based on the evidence of active exploitationCVE-2024-40766 SonicWall SonicOS contains an improper access control vu ... Read more
-
Cybersecurity News
Akira Ransomware Exploits SonicWall SSLVPN Flaw (CVE-2024-40766)
SonicWall has issued a warning: the recently patched critical access control vulnerability, tracked as CVE-2024-40766, is now actively exploited in the wild. The flaw, originally thought to impact onl ... Read more
-
Cybersecurity News
RomCom Group’s Underground Ransomware Exploits Microsoft Zero-Day Flaw
The data leak site for Underground ransomwareFortiGuard Labs found a new ransomware variant, Underground, that has been linked to the Russia-based RomCom group (also known as Storm-0978). This insidio ... Read more

-
Cybersecurity News
Google Patches Actively Exploited Zero-Day in September Android Update
Google’s September 2024 Android security patch addresses 36 vulnerabilities, one of which has already been exploited in active targeted attacks. The zero-day flaw, tracked as CVE-2024-32896 (CVSS scor ... Read more
-
Cybersecurity News
CVE-2024-8105: An UEFI Flaw Putting Millions of Devices at Risk
Image: Binarly REsearch TeamA significant vulnerability, CVE-2024-8105, dubbed PKfail, has surfaced within the UEFI ecosystem. With a CVSS score of 8.2, this flaw exposes critical UEFI security mechan ... Read more
-
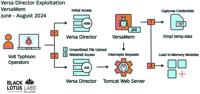
The Cyber Express
Versa Director Zero-Day Attack: A Non-Critical Vulnerability with Low Exposure Can Still Be Trouble
A zero-day vulnerability in Versa Director servers is proof that a vulnerability doesn’t require a critical severity rating and thousands of exposures to do significant damage. CVE-2024-39717, announc ... Read more
The following table lists the changes that have been made to the
CVE-2024-39717 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Oct. 30, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-39717 Types: US Government Resource -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-39717 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-39717 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-39717 -
Modified Analysis by [email protected]
Aug. 28, 2024
Action Type Old Value New Value Changed Reference Type https://versa-networks.com/blog/versa-security-bulletin-update-on-cve-2024-39717-versa-director-dangerous-file-type-upload-vulnerability/ No Types Assigned https://versa-networks.com/blog/versa-security-bulletin-update-on-cve-2024-39717-versa-director-dangerous-file-type-upload-vulnerability/ Vendor Advisory -
CVE Modified by [email protected]
Aug. 27, 2024
Action Type Old Value New Value Changed Description The Versa Director GUI provides an option to customize the look and feel of the user interface. This option is only available for a user logged with Provider-Data-Center-Admin or Provider-Data-Center-System-Admin. (Tenant level users do not have this privilege). The “Change Favicon” (Favorite Icon) option can be mis-used to upload a malicious file ending with .png extension to masquerade as image file. This is possible only after a user with Provider-Data-Center-Admin or Provider-Data-Center-System-Admin has successfully authenticated and logged in. Severity: HIGH Exploitation Status: Versa Networks is aware of one confirmed customer reported instance where this vulnerability was exploited because the Firewall guidelines which were published in 2015 & 2017 were not implemented by that customer. This non-implementation resulted in the bad actor being able to exploit this vulnerability without using the GUI. In our testing (not exhaustive, as not all numerical versions of major browsers were tested) the malicious file does not get executed on the client. There are reports of others based on backbone telemetry observations of a 3rd party provider, however these are unconfirmed to date. The Versa Director GUI provides an option to customize the look and feel of the user interface. This option is only available for a user logged with Provider-Data-Center-Admin or Provider-Data-Center-System-Admin. (Tenant level users do not have this privilege). The “Change Favicon” (Favorite Icon) option can be mis-used to upload a malicious file ending with .png extension to masquerade as image file. This is possible only after a user with Provider-Data-Center-Admin or Provider-Data-Center-System-Admin has successfully authenticated and logged in. Added Reference HackerOne https://versa-networks.com/blog/versa-security-bulletin-update-on-cve-2024-39717-versa-director-dangerous-file-type-upload-vulnerability/ [No types assigned] Removed Reference HackerOne https://support.versa-networks.com/support/solutions/articles/23000026724-versa-director-ha-port-exploit-discovery-remediation Removed Reference HackerOne https://support.versa-networks.com/support/solutions/articles/23000024323-release-21-2-3 Removed Reference HackerOne https://support.versa-networks.com/support/solutions/articles/23000025680-release-22-1-2 Removed Reference HackerOne https://support.versa-networks.com/support/solutions/articles/23000026033-release-22-1-3 -
Initial Analysis by [email protected]
Aug. 26, 2024
Action Type Old Value New Value Added CVSS V3.1 NIST AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H Changed Reference Type https://support.versa-networks.com/support/solutions/articles/23000024323-release-21-2-3 No Types Assigned https://support.versa-networks.com/support/solutions/articles/23000024323-release-21-2-3 Permissions Required Changed Reference Type https://support.versa-networks.com/support/solutions/articles/23000025680-release-22-1-2 No Types Assigned https://support.versa-networks.com/support/solutions/articles/23000025680-release-22-1-2 Permissions Required Changed Reference Type https://support.versa-networks.com/support/solutions/articles/23000026033-release-22-1-3 No Types Assigned https://support.versa-networks.com/support/solutions/articles/23000026033-release-22-1-3 Permissions Required Changed Reference Type https://support.versa-networks.com/support/solutions/articles/23000026724-versa-director-ha-port-exploit-discovery-remediation No Types Assigned https://support.versa-networks.com/support/solutions/articles/23000026724-versa-director-ha-port-exploit-discovery-remediation Permissions Required Added CWE NIST CWE-434 Added CPE Configuration OR *cpe:2.3:a:versa-networks:versa_director:21.2.2:*:*:*:*:*:*:* *cpe:2.3:a:versa-networks:versa_director:21.2.3:*:*:*:*:*:*:* *cpe:2.3:a:versa-networks:versa_director:22.1.1:*:*:*:*:*:*:* *cpe:2.3:a:versa-networks:versa_director:22.1.2:*:*:*:*:*:*:* *cpe:2.3:a:versa-networks:versa_director:22.1.3:*:*:*:*:*:*:* -
CVE CISA KEV Update by 9119a7d8-5eab-497f-8521-727c672e3725
Aug. 24, 2024
Action Type Old Value New Value Added Vulnerability Name Versa Director Dangerous File Type Upload Vulnerability Added Required Action Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable. Added Due Date 2024-09-13 Added Date Added 2024-08-23 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Aug. 23, 2024
Action Type Old Value New Value Added CWE CISA-ADP CWE-434 -
CVE Received by [email protected]
Aug. 22, 2024
Action Type Old Value New Value Added Description The Versa Director GUI provides an option to customize the look and feel of the user interface. This option is only available for a user logged with Provider-Data-Center-Admin or Provider-Data-Center-System-Admin. (Tenant level users do not have this privilege). The “Change Favicon” (Favorite Icon) option can be mis-used to upload a malicious file ending with .png extension to masquerade as image file. This is possible only after a user with Provider-Data-Center-Admin or Provider-Data-Center-System-Admin has successfully authenticated and logged in. Severity: HIGH Exploitation Status: Versa Networks is aware of one confirmed customer reported instance where this vulnerability was exploited because the Firewall guidelines which were published in 2015 & 2017 were not implemented by that customer. This non-implementation resulted in the bad actor being able to exploit this vulnerability without using the GUI. In our testing (not exhaustive, as not all numerical versions of major browsers were tested) the malicious file does not get executed on the client. There are reports of others based on backbone telemetry observations of a 3rd party provider, however these are unconfirmed to date. Added Reference HackerOne https://support.versa-networks.com/support/solutions/articles/23000026724-versa-director-ha-port-exploit-discovery-remediation [No types assigned] Added Reference HackerOne https://support.versa-networks.com/support/solutions/articles/23000024323-release-21-2-3 [No types assigned] Added Reference HackerOne https://support.versa-networks.com/support/solutions/articles/23000025680-release-22-1-2 [No types assigned] Added Reference HackerOne https://support.versa-networks.com/support/solutions/articles/23000026033-release-22-1-3 [No types assigned] Added CVSS V3 HackerOne AV:N/AC:H/PR:H/UI:N/S:U/C:H/I:H/A:H


