CVE-2024-42327
SQL injection in user.get API
Description
A non-admin user account on the Zabbix frontend with the default User role, or with any other role that gives API access can exploit this vulnerability. An SQLi exists in the CUser class in the addRelatedObjects function, this function is being called from the CUser.get function which is available for every user who has API access.
INFO
Published Date :
Nov. 27, 2024, 12:15 p.m.
Last Modified :
Oct. 8, 2025, 4:41 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] |
Solution
- There is no known solution at this time.
Public PoC/Exploit Available at Github
CVE-2024-42327 has a 34 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-42327.
| URL | Resource |
|---|---|
| https://support.zabbix.com/browse/ZBX-25623 | Vendor Advisory |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-42327 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-42327
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
None
这是一个用于扫描Zabbix系统中常见漏洞的工具,提供了图形界面(GUI)和命令行(CLI)两种使用方式。
Python
Wiki漏洞库管理系统&网络安全知识库-渗透测试常见漏洞知识库文档-该网站收集了Web应用层漏洞、中间件安全缺陷、系统配置不当、移动端(Android)安全问题、权限提升、RCE、网络设备及IOT安全。
cve cves cyber-security cybersecurity exploit payload pentest pentesting pentesting-tools poc redteam redteam-tools security security-scan vlun wiki android iotsecurity webscan webscanner
备份的漏洞库,3月开始我们来维护
None
None
PoCs & Exploits
JavaScript Shell Python PHP
None
HTML
This is for educational porpuses only. Please do not use agains unathorized systems.
Python
wy876
Python
wy876 POC | wy876的poc仓库已删库,该项目为其仓库镜像
备份的漏洞库,3月开始我们来维护
2023HW漏洞整理,收集整理漏洞EXp/POC,大部分漏洞来源网络,目前收集整理了300多个poc/exp,长期更新。
漏洞文库 wiki.wy876.cn
HTML
Recull d'apunts, cheatsheet, scripts i writeups com a formació per les diferents certificacions planejades.
Shell Python
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-42327 vulnerability anywhere in the article.
-
Daily CyberSecurity
CVE-2025-27237: Zabbix Agent Flaw Allows Local Privilege Escalation via OpenSSL DLL Injection
A newly disclosed vulnerability in the Zabbix Agent and Agent 2 for Windows could allow local attackers to gain elevated privileges by exploiting a DLL injection flaw in the software’s OpenSSL configu ... Read more

-
Daily CyberSecurity
Multiple Vulnerabilities in Zabbix Open the Door to XSS, DoS, and SQL Injection
Zabbix, a cornerstone in IT infrastructure monitoring fixed five newly disclosed security vulnerabilities ranging from low-severity information leaks to high-impact SQL injection and denial-of-service ... Read more
-
Cybersecurity News
CVE-2024-45387: PoC Published for Critical SQL Injection in Apache Traffic Control
Security researcher Abdelrhman Zayed, in collaboration with Mohamed Abdelhady, has published proof-of-concept (PoC) exploit code for CVE-2024-45387, a critical SQL injection vulnerability in Apache Tr ... Read more

-
Cybersecurity News
CVE-2024-9474 Exploited: LITTLELAMB.WOOLTEA Backdoor Discovered in Palo Alto Devices
Northwave Cyber Security has identified a sophisticated backdoor, LITTLELAMB.WOOLTEA, targeting Palo Alto Networks firewalls.The backdoor was uncovered during a forensic investigation into a compromis ... Read more

-
Cybersecurity News
CVE-2024-56337: Apache Tomcat Patches Critical RCE Vulnerability
The Apache Software Foundation recently released a critical security update to address a remote code execution (RCE) vulnerability in Apache Tomcat, identified as CVE-2024-56337. This vulnerability af ... Read more

-
Cybersecurity News
336,000 Prometheus Servers at Risk: Urgent Security Alert
In a recent investigation, Aqua Nautilus uncovered alarming security vulnerabilities within the Prometheus ecosystem. Their research highlights critical flaws spanning information disclosure, denial-o ... Read more

-
TheCyberThrone
TheCyberThrone Security BiWeekly Review – December 14, 2024
Welcome to TheCyberThrone cybersecurity week in review will be posted covering the important security happenings. This review is for the weeks ending Saturday, November 30, 2024.Jenkins fixes multiple ... Read more

-
Cybersecurity News
Abusing Microsoft’s UI Automation Framework: The New Evasion Technique Bypassing EDR
Akamai security researcher Tomer Peled has unveiled a novel attack technique exploiting Microsoft’s legacy UI Automation framework, a tool originally designed to enhance computer accessibility. The fi ... Read more

-
Cybersecurity News
Modular Java Backdoor Emerges in Cleo Exploitation Campaign (CVE-2024-50623)
Rapid7 Labs and its Managed Detection and Response (MDR) team uncovered a sophisticated modular Java-based Remote Access Trojan (RAT) deployed in a multi-stage attack targeting Cleo file transfer soft ... Read more

-
Cybersecurity News
$5 Million Reward Offered After Indictment of North Korean Cyber Operatives
A federal court in St. Louis, Missouri, has indicted 14 nationals of the Democratic People’s Republic of Korea (DPRK) for a series of long-running conspiracies involving sanctions violations, wire fra ... Read more

-
Cybersecurity News
CVE-2020-12271 Exploited: FBI Seeks Chinese Hacker Behind 81,000 Device Breach
The US Department of Justice announced the unsealing of an indictment against Guan Tianfeng, a Chinese national associated with Sichuan Silence Information Technology Co. Ltd., for his alleged role in ... Read more

-
Cybersecurity News
Ivanti Connect Secure and Policy Secure Updates Address Critical Vulnerabilities
Ivanti, a leader in unified endpoint and enterprise service management, has issued patches for several high and critical vulnerabilities affecting its Connect Secure and Policy Secure solutions. These ... Read more

-
Cybersecurity News
CVE-2024-52335 (CVSS 9.8): Siemens Healthineers Addresses Critical Flaw in Medical Imaging Software
Siemens Healthineers has released a critical security update to address an unauthenticated SQL injection vulnerability in its syngo.plaza VB30E medical imaging software. The vulnerability, identified ... Read more
-
Cybersecurity News
Google Chrome Patches High-Severity Vulnerabilities – CVE-2024-12381 & CVE-2024-12382
Google has announced its Chrome browser’s latest stable channel update, addressing several security vulnerabilities, including two classified as “High” severity. The update, rolling out progressively ... Read more
-
Cybersecurity News
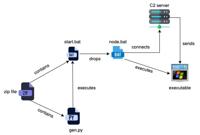
Beware of Celestial Stealer: New MaaS Targets Browsers and Crypto Wallets
A new report from Trellix Advanced Research Center has exposed the inner workings of Celestial Stealer, a sophisticated Malware-as-a-Service (MaaS) platform targeting developers, gamers, and cryptocur ... Read more
-
Cybersecurity News
Google Chrome Addresses High-Severity Flaw in V8 JavaScript Engine (CVE-2024-12053)
Google has released a security update for its Chrome web browser to mitigate a high-severity “type confusion” vulnerability (CVE-2024-12053) residing within the V8 JavaScript engine. This vulnerabilit ... Read more

-
TheCyberThrone
Apache Arrow affected by CVE-2024-52338 Code Execution Flaw
The Apache Arrow R package has been identified with a critical security vulnerability impacting versions 4.0.0 through 16.1.0, could allow attackers to execute arbitrary code on systems processing ma ... Read more

-
security.nl
Zabbix-servers via kritiek SQL injection-lek op afstand over te nemen
Een kritiek beveiligingslek in open source monitoringtool Zabbix maakt het mogelijk om kwetsbare servers door middel van SQL injection op afstand over te nemen. De ontwikkelaar heeft vorige week bevei ... Read more

-
The Hacker News
THN Recap: Top Cybersecurity Threats, Tools and Tips (Nov 25 - Dec 1)
Cyber Threats / Weekly Recap Ever wonder what happens in the digital world every time you blink? Here's something wild - hackers launch about 2,200 attacks every single day, which means someone's tryi ... Read more

-
TheCyberThrone
The CyberThrone Most Exploited Vulnerabilities Top 10 – November 2024
Welcome to TheCyberThrone most exploited vulnerabilities review. This review is for the month of November 2024CVE-2024-9463: Palo Alto OS Command InjectionCVSS 3.1 Score : 9.9 CISA KEV: YesThis vuln ... Read more
The following table lists the changes that have been made to the
CVE-2024-42327 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Initial Analysis by [email protected]
Oct. 08, 2025
Action Type Old Value New Value Added CPE Configuration OR *cpe:2.3:a:zabbix:zabbix:*:*:*:*:*:*:*:* versions from (including) 6.0.0 up to (excluding) 6.0.32 *cpe:2.3:a:zabbix:zabbix:*:*:*:*:*:*:*:* versions from (including) 6.4.0 up to (excluding) 6.4.17 *cpe:2.3:a:zabbix:zabbix:*:*:*:*:*:*:*:* versions from (including) 7.0.0 up to (excluding) 7.0.1 Added Reference Type Zabbix: https://support.zabbix.com/browse/ZBX-25623 Types: Vendor Advisory -
New CVE Received by [email protected]
Nov. 27, 2024
Action Type Old Value New Value Added Description A non-admin user account on the Zabbix frontend with the default User role, or with any other role that gives API access can exploit this vulnerability. An SQLi exists in the CUser class in the addRelatedObjects function, this function is being called from the CUser.get function which is available for every user who has API access. Added CVSS V3.1 AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H Added CWE CWE-89 Added Reference https://support.zabbix.com/browse/ZBX-25623