CVE-2024-43047
Qualcomm Multiple Chipsets Use-After-Free Vulnerability - [Actively Exploited]
Description
Memory corruption while maintaining memory maps of HLOS memory.
INFO
Published Date :
Oct. 7, 2024, 1:15 p.m.
Last Modified :
Oct. 28, 2025, 1:47 p.m.
Remotely Exploit :
No
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
Multiple Qualcomm chipsets contain a use-after-free vulnerability due to memory corruption in DSP Services while maintaining memory maps of HLOS memory.
Apply remediations or mitigations per vendor instructions or discontinue use of the product if remediation or mitigations are unavailable.
Unknown
https://git.codelinaro.org/clo/la/platform/vendor/qcom/opensource/dsp-kernel/-/commit/0e27b6c7d2bd8d0453e4465ac2ca49a8f8c440e2 ; https://nvd.nist.gov/vuln/detail/CVE-2024-43047
Affected Products
The following products are affected by CVE-2024-43047
vulnerability.
Even if cvefeed.io is aware of the exact versions of the
products
that
are
affected, the information is not represented in the table below.
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | HIGH | [email protected] |
Public PoC/Exploit Available at Github
CVE-2024-43047 has a 5 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-43047.
| URL | Resource |
|---|---|
| https://docs.qualcomm.com/product/publicresources/securitybulletin/october-2024-bulletin.html | Patch Vendor Advisory |
| https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-43047 | US Government Resource |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-43047 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-43047
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
None
None
CVE-2024-43093
None
A collection of links related to Linux kernel security and exploitation
linux-kernel kernel-exploitation exploit privilege-escalation security
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-43047 vulnerability anywhere in the article.

-
BleepingComputer
Android gets patches for Qualcomm flaws exploited in attacks
Google has released security patches for six vulnerabilities in Android's August 2025 security update, including two Qualcomm flaws exploited in targeted attacks. The two security bugs, tracked as CVE ... Read more

-
BleepingComputer
Google fixes Android zero-days exploited in attacks, 60 other flaws
Google has released patches for 62 vulnerabilities in Android's April 2025 security update, including two zero-days exploited in targeted attacks. One of the zero-days, a high-severity privilege escal ... Read more

-
BleepingComputer
Google fixes Android zero-day exploited by Serbian authorities
Google has released patches for 43 vulnerabilities in Android's March 2025 security update, including two zero-days exploited in targeted attacks. Serbian authorities have used one of the zero-days, a ... Read more

-
BleepingComputer
Google fixes Android kernel zero-day exploited in attacks
The February 2025 Android security updates patch 48 vulnerabilities, including a zero-day kernel vulnerability that has been exploited in the wild. This high-severity zero-day (tracked as CVE-2024-531 ... Read more

-
TheCyberThrone
Zeroday Vulnerabilities Prevailed in 2024 Analysis-Part II
This is the continuation of Zeroday vulnerabilities in 2024. Let’s delve deeply into the continuation of zero-day vulnerabilities of 2024, providing a comprehensive analysis.1. CVE-2023-46805: Authen ... Read more

-
The Hacker News
NoviSpy Spyware Installed on Journalist's Phone After Unlocking It With Cellebrite Tool
A Serbian journalist had his phone first unlocked by a Cellebrite tool and subsequently compromised by a previously undocumented spyware codenamed NoviSpy, according to a new report published by Amnes ... Read more

-
security.nl
Amnesty: Cellebrite gebruikt Androidlek om telefoons te ontgrendelen
maandag 16 december 2024, 12:03 door Redactie, 11 reactiesLaatst bijgewerkt: 16-12-2024, 14:38 Het forensisch bedrijf Cellebrite gebruikt een kwetsbaarheid in Android om de beveiliging van Androidtele ... Read more

-
security.nl
Amnesty: Cellebrite gebruikt Androidlek om beveiliging te omzeilen
maandag 16 december 2024, 12:03 door Redactie, 11 reactiesLaatst bijgewerkt: 16-12-2024, 14:38 Het forensisch bedrijf Cellebrite gebruikt een kwetsbaarheid in Android om de beveiliging van Androidtele ... Read more

-
Kaspersky
Advanced threat predictions for 2025
We at Kaspersky’s Global Research and Analysis Team monitor over 900 APT (advanced persistent threat) groups and operations. At the end of each year, we take a step back to assess the most complex and ... Read more

-
Cybersecurity News
Ivanti Connect Secure, Policy Secure and Secure Access Client Affected by Critical Vulnerabilities
Ivanti has released urgent security updates to address a range of vulnerabilities, including critical remote code execution (RCE) flaws, in its Connect Secure, Policy Secure, and Secure Access Client ... Read more

-
Cybersecurity News
CVE-2024-10575 (CVSS 10): Critical Flaw in Schneider Electric’s EcoStruxure IT Gateway
Schneider Electric has published a security notification about a critical vulnerability in its EcoStruxure™ IT Gateway platform, which connects IT infrastructure devices to the cloud for monitoring an ... Read more

-
Cybersecurity News
CVE-2024-50330 (CVSS 9.8): Unpatched Ivanti Endpoint Manager Vulnerable to RCE Attacks
Software company Ivanti has released urgent security updates for its Endpoint Manager to address a range of vulnerabilities, including several that could allow for remote code execution (RCE).The vuln ... Read more
-
Cybersecurity News
CVE-2024-8068 & CVE-2024-8069: Citrix Session Recording Manager Unauthenticated RCE Exploits Publicly Available
Security researchers at watchTowr have uncovered two critical vulnerabilities in Citrix Session Recording Manager that, when chained together, allow unauthenticated remote code execution (RCE) on Citr ... Read more

-
Cybersecurity News
CVE-2024-44102 (CVSS 10) Found in Siemens TeleControl Server Basic: Urgent Update Required
A critical security vulnerability has been discovered in Siemens TeleControl Server Basic V3.1, a software solution used for remote monitoring and control of industrial plants. The vulnerability, iden ... Read more

-
Cybersecurity News
CVE-2024-11068 (CVSS 9.8): Critical D-Link DSL-6740C Flaw, Immediate Replacement Advised
TWCERT/CC has issued multiple security advisories for the D-Link DSL-6740C modem, revealing a range of severe vulnerabilities that could expose users to remote attacks.The modem, which is no longer su ... Read more
-
Cybersecurity News
JavaScript Drive-By Attacks: New Exploits without 0-Day in Google Chrome
Ron Masas from Imperva Threat Research has uncovered a new way attackers can target Chrome users without relying on 0-day vulnerabilities. This approach leverages the File System Access API, which all ... Read more
-
Cybersecurity News
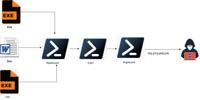
Fickle Stealer: The New Rust-Based Malware Masquerading as GitHub Desktop
Attack flow | Image: TrellixIn a recent report by Trellix researchers Mallikarjun Wali and Sangram Mohapatro, a new Rust-based malware called Fickle Stealer has surfaced, posing a significant threat t ... Read more

-
Help Net Security
Week in review: Zero-click flaw in Synology NAS devices, Google fixes exploited Android vulnerability
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Millions of Synology NAS devices vulnerable to zero-click attacks (CVE-2024-10443) Synology has releas ... Read more

-
Cybersecurity News
CISA Expands KEV Catalog with Four Actively Exploited Vulnerabilities
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an updated advisory regarding four security vulnerabilities actively exploited in the wild. These vulnerabilities, now included i ... Read more

-
The Cyber Express
Google Addresses Two Android Zero-Days Used in Targeted Attacks
In its November security update, Google has patched two critical Android zero-days actively exploited in targeted attacks, along with 49 additional vulnerabilities. Google flagged these zero-day flaws ... Read more
The following table lists the changes that have been made to the
CVE-2024-43047 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Oct. 28, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-43047 Types: US Government Resource -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-43047 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-43047 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-43047 -
CPE Deprecation Remap by [email protected]
Aug. 11, 2025
Action Type Old Value New Value Changed CPE Configuration OR *cpe:2.3:o:qualcomm:video_collaboration_vc1_firmware:-:*:*:*:*:*:*:* OR *cpe:2.3:o:qualcomm:video_collaboration_vc1_platform_firmware:-:*:*:*:*:*:*:* -
CPE Deprecation Remap by [email protected]
Aug. 11, 2025
Action Type Old Value New Value Changed CPE Configuration OR *cpe:2.3:o:qualcomm:video_collaboration_vc3_firmware:-:*:*:*:*:*:*:* OR *cpe:2.3:o:qualcomm:video_collaboration_vc3_platform_firmware:-:*:*:*:*:*:*:* -
CPE Deprecation Remap by [email protected]
Aug. 07, 2025
Action Type Old Value New Value Changed CPE Configuration OR *cpe:2.3:h:qualcomm:video_collaboration_vc3:-:*:*:*:*:*:*:* OR *cpe:2.3:h:qualcomm:video_collaboration_vc3_platform:-:*:*:*:*:*:*:* -
CPE Deprecation Remap by [email protected]
Aug. 07, 2025
Action Type Old Value New Value Changed CPE Configuration OR *cpe:2.3:h:qualcomm:video_collaboration_vc1:-:*:*:*:*:*:*:* OR *cpe:2.3:h:qualcomm:video_collaboration_vc1_platform:-:*:*:*:*:*:*:* -
Initial Analysis by [email protected]
Oct. 09, 2024
Action Type Old Value New Value Changed Reference Type https://docs.qualcomm.com/product/publicresources/securitybulletin/october-2024-bulletin.html No Types Assigned https://docs.qualcomm.com/product/publicresources/securitybulletin/october-2024-bulletin.html Patch, Vendor Advisory Added CWE NIST CWE-416 Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:fastconnect_6700_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:fastconnect_6700:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:fastconnect_6800_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:fastconnect_6800:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:fastconnect_6900_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:fastconnect_6900:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:fastconnect_7800_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:fastconnect_7800:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:qam8295p_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:qam8295p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:qca6174a_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:qca6174a:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:qca6391_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:qca6391:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:qca6426_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:qca6426:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:qca6436_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:qca6436:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:qca6574au_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:qca6574au:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:qca6584au_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:qca6584au:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:qca6595_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:qca6595:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:qca6595au_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:qca6595au:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:qca6688aq_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:qca6688aq:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:qca6696_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:qca6696:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:qca6698aq_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:qca6698aq:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:qcs410_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:qcs410:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:qcs610_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:qcs610:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:qcs6490_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:qcs6490:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:video_collaboration_vc1_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:video_collaboration_vc1:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:video_collaboration_vc3_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:video_collaboration_vc3:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:sa4150p_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:sa4150p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:sa4155p_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:sa4155p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:sa6145p_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:sa6145p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:sa6150p_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:sa6150p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:sa6155p_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:sa6155p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:sa8145p_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:sa8145p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:sa8150p_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:sa8150p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:sa8155p_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:sa8155p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:sa8195p_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:sa8195p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:sa8295p_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:sa8295p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:sd660_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:sd660:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:sd865_5g_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:sd865_5g:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:sg4150p_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:sg4150p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:snapdragon_660_mobile_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:snapdragon_660_mobile:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:snapdragon_680_4g_mobile_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:snapdragon_680_4g_mobile:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:snapdragon_685_4g_mobile_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:snapdragon_685_4g_mobile:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:snapdragon_8_gen_1_mobile_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:snapdragon_8_gen_1_mobile:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:snapdragon_865_5g_mobile_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:snapdragon_865_5g_mobile:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:snapdragon_865\+_5g_mobile_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:snapdragon_865\+_5g_mobile:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:snapdragon_870_5g_mobile_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:snapdragon_870_5g_mobile:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:snapdragon_888_5g_mobile_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:snapdragon_888_5g_mobile:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:snapdragon_888\+_5g_mobile_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:snapdragon_888\+_5g_mobile:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:snapdragon_auto_5g_modem-rf_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:snapdragon_auto_5g_modem-rf:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:snapdragon_auto_5g_modem-rf_gen_2_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:snapdragon_auto_5g_modem-rf_gen_2:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:snapdragon_x55_5g_modem-rf_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:snapdragon_x55_5g_modem-rf:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:snapdragon_xr2_5g_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:snapdragon_xr2_5g:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:sw5100_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:sw5100:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:sw5100p_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:sw5100p:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:sxr2130_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:sxr2130:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:wcd9335_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:wcd9335:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:wcd9341_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:wcd9341:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:wcd9370_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:wcd9370:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:wcd9375_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:wcd9375:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:wcd9380_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:wcd9380:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:wcd9385_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:wcd9385:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:wcn3950_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:wcn3950:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:wcn3980_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:wcn3980:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:wcn3988_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:wcn3988:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:wcn3990_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:wcn3990:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:wsa8810_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:wsa8810:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:wsa8815_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:wsa8815:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:wsa8830_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:wsa8830:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:qualcomm:wsa8835_firmware:-:*:*:*:*:*:*:* OR cpe:2.3:h:qualcomm:wsa8835:-:*:*:*:*:*:*:* -
CVE CISA KEV Update by 9119a7d8-5eab-497f-8521-727c672e3725
Oct. 09, 2024
Action Type Old Value New Value Added Due Date 2024-10-29 Added Vulnerability Name Qualcomm Multiple Chipsets Use-After-Free Vulnerability Added Required Action Apply remediations or mitigations per vendor instructions or discontinue use of the product if remediation or mitigations are unavailable. Added Date Added 2024-10-08 -
CVE Received by [email protected]
Oct. 07, 2024
Action Type Old Value New Value Added Description Memory corruption while maintaining memory maps of HLOS memory. Added Reference Qualcomm, Inc. https://docs.qualcomm.com/product/publicresources/securitybulletin/october-2024-bulletin.html [No types assigned] Added CWE Qualcomm, Inc. CWE-416 Added CVSS V3.1 Qualcomm, Inc. AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H


