CVE-2024-43202
Apache DolphinScheduler: Remote Code Execution Vulnerability
Description
Exposure of Remote Code Execution in Apache Dolphinscheduler. This issue affects Apache DolphinScheduler: before 3.2.2. We recommend users to upgrade Apache DolphinScheduler to version 3.2.2, which fixes the issue.
INFO
Published Date :
Aug. 20, 2024, 8:15 a.m.
Last Modified :
March 18, 2025, 3:57 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] | ||||
| CVSS 3.1 | CRITICAL | 134c704f-9b21-4f2e-91b3-4a467353bcc0 |
Public PoC/Exploit Available at Github
CVE-2024-43202 has a 1 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-43202.
| URL | Resource |
|---|---|
| https://github.com/apache/dolphinscheduler/pull/15758 | Issue Tracking Patch |
| https://lists.apache.org/thread/nlmdp7q7l7o3l27778vxc5px24ncr5r5 | Vendor Advisory |
| https://lists.apache.org/thread/qbhk9wqyxhrn4z7m4m343wqxpwg926nh | Vendor Advisory |
| https://www.cve.org/CVERecord?id=CVE-2023-49109 | Third Party Advisory |
| http://www.openwall.com/lists/oss-security/2024/08/20/2 | Mailing List Third Party Advisory |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-43202 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-43202
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
yasa
Dockerfile Shell
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-43202 vulnerability anywhere in the article.

-
Cybersecurity News
Citrix Workspace App Users Urged to Update Following Two Privilege Escalation Flaws
In a security advisory released recently, Cloud Software Group has disclosed two vulnerabilities affecting the widely used Citrix Workspace app for Windows. These vulnerabilities, identified as CVE-20 ... Read more
-
Cybersecurity News
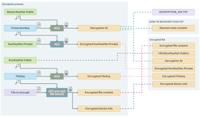
CosmicBeetle’s ScRansom Ransomware: A Growing Threat to European and Asian Businesses
Encryption scheme utilized by the latest ScRansom samples | Image: ESETIn a significant development tracked by ESET researchers, the threat actor known as CosmicBeetle has intensified its ransomware o ... Read more
-
Cybersecurity News
LNK Stomping (CVE-2024-38217): Microsoft Patches Years-Old Zero-Day Flaw
Image: Elastic SecurityMicrosoft’s September 2024 security update addresses a zero-day vulnerability affecting Smart App Control and SmartScreen. This vulnerability, dubbed “LNK stomping” (CVE-2024-38 ... Read more

-
Cybersecurity News
CVE-2024-6633 (CVSS 9.8): Critical Flaw in Fortra FileCatalyst Workflow
Fortra, a prominent provider of enterprise file transfer solutions, has released an urgent security advisory highlighting two critical vulnerabilities within its FileCatalyst Workflow product. Designa ... Read more

-
Cybersecurity News
SSN, Banking Details at Risk in Major Texas Credit Union Breach
The largest credit union in Texas, Texas Dow Employees Credit Union (TDECU), has reported a significant data breach affecting more than 500,000 individuals. The incident may have compromised Social Se ... Read more

-
Cybersecurity News
Google Chrome Faces Double Blow with New Zero-Day Flaw Exploits: CVE-2024-7965 and CVE-2024-7971
In a significant update to its security advisory, Google has confirmed that CVE-2024-7965, a high-severity zero-day vulnerability in the Chrome browser, has been actively exploited in the wild. This r ... Read more

-
Cybersecurity News
China-Nexus Group Velvet Ant Exploits Cisco Zero-Day (CVE-2024-20399)
At the beginning of 2024, the Chinese group Velvet Ant exploited a patched zero-day vulnerability (CVE-2024-20399, CVSS 6.7) in Cisco switches to gain control over devices and bypass threat detection ... Read more
-
Cybersecurity News
Exploit for CVE-2024-38054 Released: Elevation of Privilege Flaw in Windows Kernel Streaming WOW Thunk
Security researcher ‘Frost’ has released proof-of-concept exploit code for the CVE-2024-38054 vulnerability, escalating concerns over a recently patched Windows security flaw. This high-severity vulne ... Read more

-
Cyber Security News
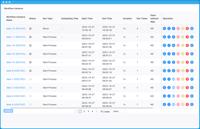
Apache DolphinScheduler Vulnerability Let Hackers Execute Remote Code
A critical vulnerability has been identified in Apache DolphinScheduler, a popular open-source workflow orchestration platform. This security flaw, designated as CVE-2024-43202, allows hackers to exec ... Read more
-
Cybersecurity News
CVE-2024-43202: RCE Vulnerability Discovered in Apache DolphinScheduler
The Apache DolphinScheduler project, renowned for its streamlined approach to data orchestration, has issued a critical security advisory warning users of a remote code execution (RCE) vulnerability. ... Read more

-
Cybersecurity News
F5 Issues Security Advisories for NGINX Plus (CVE-2024-39792) & BIG-IP Next Central Manager (CVE-2024-39809)
F5, a prominent provider of application delivery and security solutions, has recently released security advisories addressing vulnerabilities in two of its products: NGINX Plus and BIG-IP Next Central ... Read more

-
Cybersecurity News
PrestaShop Websites Under Attack: GTAG Websocket Skimmer Steals Credit Card Data
Security researchers at Sucuri have discovered a new credit card skimmer exploiting a vulnerability in PrestaShop websites. This sophisticated attack uses a WebSocket connection to pilfer sensitive cu ... Read more
The following table lists the changes that have been made to the
CVE-2024-43202 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Initial Analysis by [email protected]
Mar. 18, 2025
Action Type Old Value New Value Added CVSS V3.1 AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Added CPE Configuration OR *cpe:2.3:a:apache:dolphinscheduler:*:*:*:*:*:*:*:* versions from (including) 3.0.0 up to (excluding) 3.2.2 Added Reference Type CVE: http://www.openwall.com/lists/oss-security/2024/08/20/2 Types: Mailing List, Third Party Advisory Added Reference Type Apache Software Foundation: https://github.com/apache/dolphinscheduler/pull/15758 Types: Issue Tracking, Patch Added Reference Type Apache Software Foundation: https://lists.apache.org/thread/nlmdp7q7l7o3l27778vxc5px24ncr5r5 Types: Vendor Advisory Added Reference Type Apache Software Foundation: https://lists.apache.org/thread/qbhk9wqyxhrn4z7m4m343wqxpwg926nh Types: Vendor Advisory Added Reference Type Apache Software Foundation: https://www.cve.org/CVERecord?id=CVE-2023-49109 Types: Third Party Advisory -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Nov. 21, 2024
Action Type Old Value New Value Added Reference http://www.openwall.com/lists/oss-security/2024/08/20/2 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Aug. 20, 2024
Action Type Old Value New Value Added CVSS V3.1 CISA-ADP AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H -
CVE Received by [email protected]
Aug. 20, 2024
Action Type Old Value New Value Added Description Exposure of Remote Code Execution in Apache Dolphinscheduler. This issue affects Apache DolphinScheduler: before 3.2.2. We recommend users to upgrade Apache DolphinScheduler to version 3.2.2, which fixes the issue. Added Reference Apache Software Foundation https://github.com/apache/dolphinscheduler/pull/15758 [No types assigned] Added Reference Apache Software Foundation https://lists.apache.org/thread/nlmdp7q7l7o3l27778vxc5px24ncr5r5 [No types assigned] Added Reference Apache Software Foundation https://lists.apache.org/thread/qbhk9wqyxhrn4z7m4m343wqxpwg926nh [No types assigned] Added Reference Apache Software Foundation https://www.cve.org/CVERecord?id=CVE-2023-49109 [No types assigned] Added CWE Apache Software Foundation CWE-94


