CVE-2024-47575
Fortinet FortiManager Missing Authentication Vulnerability - [Actively Exploited]
Description
A missing authentication for critical function in FortiManager 7.6.0, FortiManager 7.4.0 through 7.4.4, FortiManager 7.2.0 through 7.2.7, FortiManager 7.0.0 through 7.0.12, FortiManager 6.4.0 through 6.4.14, FortiManager 6.2.0 through 6.2.12, Fortinet FortiManager Cloud 7.4.1 through 7.4.4, FortiManager Cloud 7.2.1 through 7.2.7, FortiManager Cloud 7.0.1 through 7.0.12, FortiManager Cloud 6.4.1 through 6.4.7 allows attacker to execute arbitrary code or commands via specially crafted requests.
INFO
Published Date :
Oct. 23, 2024, 3:15 p.m.
Last Modified :
Oct. 24, 2025, 12:54 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
Fortinet FortiManager contains a missing authentication vulnerability in the fgfmd daemon that allows a remote, unauthenticated attacker to execute arbitrary code or commands via specially crafted requests.
Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable.
https://fortiguard.fortinet.com/psirt/FG-IR-24-423 ; https://nvd.nist.gov/vuln/detail/CVE-2024-47575
Affected Products
The following products are affected by CVE-2024-47575
vulnerability.
Even if cvefeed.io is aware of the exact versions of the
products
that
are
affected, the information is not represented in the table below.
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] | ||||
| CVSS 3.1 | CRITICAL | [email protected] |
Solution
- Update FortiManager to version 6.2.13, 6.4.15, 7.0.13, 7.2.8, 7.4.5 or 7.6.1 or later.
Public PoC/Exploit Available at Github
CVE-2024-47575 has a 50 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-47575.
| URL | Resource |
|---|---|
| https://fortiguard.fortinet.com/psirt/FG-IR-24-423 | Exploit Mitigation Vendor Advisory |
| https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-47575 | US Government Resource |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-47575 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-47575
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
None
None
Makefile Go PLpgSQL Dockerfile Smarty Shell HTML JavaScript TypeScript CSS
None
None
PoC for CVE-2024-47575
Python Shell
备份的漏洞库,3月开始我们来维护
None
CVE POC repo 자동 수집기
Python
None
None
HTML
wy876
Python
wy876 POC | wy876的poc仓库已删库,该项目为其仓库镜像
备份的漏洞库,3月开始我们来维护
2023HW漏洞整理,收集整理漏洞EXp/POC,大部分漏洞来源网络,目前收集整理了300多个poc/exp,长期更新。
漏洞文库 wiki.wy876.cn
HTML
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-47575 vulnerability anywhere in the article.

-
Daily CyberSecurity
“Dormant” Backdoors: Ivanti EPMM Zero-Days Exploited to Plant Long-Term Spies
Two critical zero-day vulnerabilities in Ivanti Endpoint Manager Mobile (EPMM) are currently being exploited in a widespread campaign to compromise enterprise networks across the globe. A new report f ... Read more

-
Daily CyberSecurity
Email Under Siege: Storm-2603 Exploits SmarterMail to Deploy Warlock Ransomware
A new report from ReliaQuest has uncovered a dangerous alliance between a China-based threat actor and a known ransomware strain. The group, identified as Storm-2603, has been caught actively exploiti ... Read more

-
Daily CyberSecurity
“Enjoy Your Admin Access”: Critical SmarterMail RCE Exploited in the Wild
Just weeks after a major vulnerability rocked the SmarterMail ecosystem, security researchers have uncovered a new, critical flaw that is already being weaponized in the wild. watchTowr Labs researche ... Read more

-
Daily CyberSecurity
Cisco Zero-Day Siege: Chinese Group UAT-9686 Deploys ‘Aqua’ Malware via CVSS 10 Root Exploit
A critical zero-day vulnerability in Cisco’s secure email appliances is under active siege by a sophisticated Chinese hacking group, granting them total control over sensitive network gateways. The ca ... Read more

-
Hackread - Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Critical SAP Vulnerability CVE-2025-42957 Actively Exploited by Hackers
Urgent security alert for SAP users! A critical vulnerability (CVE-2025-42957) allows attackers to take full control of your system. Find out if your SAP S/4HANA is at risk and what steps to take now ... Read more
-
Google Cloud
M-Trends 2025: Data, Insights, and Recommendations From the Frontlines
One of the ways threat actors keep up with the constantly evolving cyber defense landscape is by raising the level of sophistication of their attacks. This trend can be seen across many of our engagem ... Read more

-
TheCyberThrone
Threat Actors anchors Symlink trick on Fortinet Devices
The symlink trick is a post-exploitation technique used by attackers to maintain access to Fortinet devices even after initial vulnerabilities have been patched. This exploitation method leverages sym ... Read more

-
BleepingComputer
Critical FortiSwitch flaw lets hackers change admin passwords remotely
Fortinet has released security patches for a critical vulnerability in its FortiSwitch devices that can be exploited to change administrator passwords remotely. The company says Daniel Rozeboom of the ... Read more

-
TheCyberThrone
CVE-2024-55591 Exploit Code Released for FortiOS Flaw
Cybersecurity company watchTowr Labs has released the proof-of-concept (PoC) exploit code for a severe zero-day vulnerability, CVE-2024-55591, affecting Fortinet’s FortiOS and FortiProxy products. Thi ... Read more

-
TheCyberThrone
CVE-2023-37936 impacts Fortinet FortiSwitch
CVE-2023-37936 is a critical security vulnerability identified in Fortinet FortiSwitch devices. This vulnerability is particularly severe due to its potential to allow unauthorized code execution, lea ... Read more

-
TheCyberThrone
CISA adds Fortinet flaw CVE-2024-55591 to KEV Catalog
CVE-2024-55591 is a critical vulnerability affecting Fortinet’s FortiOS and FortiProxy devices. This vulnerability allows a remote attacker to bypass authentication mechanisms and gain super-admin pri ... Read more

-
Help Net Security
Fortinet fixes FortiOS zero-day exploited by attackers for months (CVE-2024-55591)
Fortinet has patched an authentication bypass vulnerability (CVE-2024-55591) affecting its FortiOS firewalls and FortiProxy web gateways that has been exploited as a zero-day by attackers to compromis ... Read more

-
BleepingComputer
Fortinet warns of auth bypass zero-day exploited to hijack firewalls
Attackers are exploiting a new authentication bypass zero-day vulnerability in FortiOS and FortiProxy to hijack Fortinet firewalls and breach enterprise networks. This security flaw (tracked as CVE-20 ... Read more

-
Cybersecurity News
Four-Faith Industrial Routers Under Attack: CVE-2024-12856 Exploited in the Wild
VulnCheck, a renowned cybersecurity research organization, has recently issued a warning concerning active exploitation of a critical vulnerability affecting Four-Faith industrial routers. The vulnera ... Read more

-
TheCyberThrone
Fortinet fixes several vulnerabilities including CVE-2023-34990
Fortinet has released patches for vulnerabilities affecting its popular products, including FortiClient VPN, FortiManager, and FortiWLM. These flaws range from password exposure to remote code executi ... Read more

-
Cybersecurity News
I-O DATA Routers Under Attack: Urgent Firmware Update Needed!
Multiple vulnerabilities have been discovered in I-O DATA routers UD-LT1 and UD-LT1/EX, and active exploitation is already underway. JPCERT/CC, a Japanese cybersecurity organization, issued a warning ... Read more
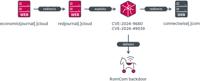
-
Cybersecurity News
RomCom Exploits Zero-Days in Firefox (CVE-2024-9680) & Windows (CVE-2024-49039) with No User Interaction
Exploit chain to compromise the victim | Image: ESETIn a recent cybersecurity report, ESET researchers have unveiled a coordinated attack by the Russia-aligned threat actor RomCom, exploiting zero-day ... Read more

-
TheCyberThrone
Broadcom repatched VMware bugs for the second time
Vmware vulnerabilities have been exploited in attacks after the initial released patches failed to fix the flawThe vulnerabilities are tracked as CVE-2024-38812 and CVE-2024-38813, released on Septem ... Read more

-
TheCyberThrone
Apache Kafka affected by CVE-2024-31141
The open-source event streaming platform Apache Kafka has been affected by a vulnerability the that could allow attackers to gain unauthorized access to sensitive information.The vulnerability tracked ... Read more

-
TheCyberThrone
CISA KEV Catalog Update Part IV- November 2024
The U.S. CISA added the following vulnerabilities to its Known Exploited Vulnerabilities catalogCVE-2024-1212 with a CVSS score of 10 and CWE-78, is a Progress Kemp LoadMaster OS command injection iss ... Read more
The following table lists the changes that have been made to the
CVE-2024-47575 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Oct. 24, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-47575 Types: US Government Resource -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-47575 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-47575 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-47575 -
Modified Analysis by [email protected]
Nov. 08, 2024
Action Type Old Value New Value -
CVE Modified by [email protected]
Nov. 07, 2024
Action Type Old Value New Value Changed Description A missing authentication for critical function in FortiManager 7.6.0, FortiManager 7.4.0 through 7.4.4, FortiManager 7.2.0 through 7.2.7, FortiManager 7.0.0 through 7.0.12, FortiManager 6.4.0 through 6.4.14, FortiManager 6.2.0 through 6.2.12, Fortinet FortiManager Cloud 7.4.1 through 7.4.4, FortiManager Cloud 7.2.1 through 7.2.7, FortiManager Cloud 7.0.1 through 7.0.13, FortiManager Cloud 6.4.1 through 6.4.7 allows attacker to execute arbitrary code or commands via specially crafted requests. A missing authentication for critical function in FortiManager 7.6.0, FortiManager 7.4.0 through 7.4.4, FortiManager 7.2.0 through 7.2.7, FortiManager 7.0.0 through 7.0.12, FortiManager 6.4.0 through 6.4.14, FortiManager 6.2.0 through 6.2.12, Fortinet FortiManager Cloud 7.4.1 through 7.4.4, FortiManager Cloud 7.2.1 through 7.2.7, FortiManager Cloud 7.0.1 through 7.0.12, FortiManager Cloud 6.4.1 through 6.4.7 allows attacker to execute arbitrary code or commands via specially crafted requests. -
Initial Analysis by [email protected]
Oct. 24, 2024
Action Type Old Value New Value Added CVSS V3.1 NIST AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Changed Reference Type https://fortiguard.fortinet.com/psirt/FG-IR-24-423 No Types Assigned https://fortiguard.fortinet.com/psirt/FG-IR-24-423 Exploit, Mitigation, Vendor Advisory Added CPE Configuration OR *cpe:2.3:a:fortinet:fortimanager:*:*:*:*:*:*:*:* versions from (including) 6.2.0 up to (excluding) 6.2.13 *cpe:2.3:a:fortinet:fortimanager:*:*:*:*:*:*:*:* versions from (including) 6.4.0 up to (excluding) 6.4.15 *cpe:2.3:a:fortinet:fortimanager:*:*:*:*:*:*:*:* versions from (including) 7.0.0 up to (excluding) 7.0.13 *cpe:2.3:a:fortinet:fortimanager:*:*:*:*:*:*:*:* versions from (including) 7.2.0 up to (excluding) 7.2.8 *cpe:2.3:a:fortinet:fortimanager:*:*:*:*:*:*:*:* versions from (including) 7.4.0 up to (excluding) 7.4.5 *cpe:2.3:a:fortinet:fortimanager:7.6.0:*:*:*:*:*:*:* *cpe:2.3:a:fortinet:fortimanager_cloud:*:*:*:*:*:*:*:* versions from (including) 6.4.1 up to (including) 6.4.7 *cpe:2.3:a:fortinet:fortimanager_cloud:*:*:*:*:*:*:*:* versions from (including) 7.0.1 up to (excluding) 7.0.13 *cpe:2.3:a:fortinet:fortimanager_cloud:*:*:*:*:*:*:*:* versions from (including) 7.2.1 up to (excluding) 7.2.8 *cpe:2.3:a:fortinet:fortimanager_cloud:*:*:*:*:*:*:*:* versions from (including) 7.4.1 up to (excluding) 7.4.5 -
CVE CISA KEV Update by 9119a7d8-5eab-497f-8521-727c672e3725
Oct. 24, 2024
Action Type Old Value New Value Added Vulnerability Name Fortinet FortiManager Missing Authentication Vulnerability Added Due Date 2024-11-13 Added Required Action Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable. Added Date Added 2024-10-23 -
CVE Received by [email protected]
Oct. 23, 2024
Action Type Old Value New Value Added Description A missing authentication for critical function in FortiManager 7.6.0, FortiManager 7.4.0 through 7.4.4, FortiManager 7.2.0 through 7.2.7, FortiManager 7.0.0 through 7.0.12, FortiManager 6.4.0 through 6.4.14, FortiManager 6.2.0 through 6.2.12, Fortinet FortiManager Cloud 7.4.1 through 7.4.4, FortiManager Cloud 7.2.1 through 7.2.7, FortiManager Cloud 7.0.1 through 7.0.13, FortiManager Cloud 6.4.1 through 6.4.7 allows attacker to execute arbitrary code or commands via specially crafted requests. Added Reference Fortinet, Inc. https://fortiguard.fortinet.com/psirt/FG-IR-24-423 [No types assigned] Added CWE Fortinet, Inc. CWE-306 Added CVSS V3.1 Fortinet, Inc. AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H


