CVE-2024-58136
Yiiframework Yii Improper Protection of Alternate Path Vulnerability - [Actively Exploited]
Description
Yii 2 before 2.0.52 mishandles the attaching of behavior that is defined by an __class array key, a CVE-2024-4990 regression, as exploited in the wild in February through April 2025.
INFO
Published Date :
April 10, 2025, 3:15 a.m.
Last Modified :
Nov. 5, 2025, 7:28 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
Yii Framework contains an improper protection of alternate path vulnerability that may allow a remote attacker to execute arbitrary code. This vulnerability could affect other products that implement Yii, including—but not limited to—Craft CMS, as represented by CVE-2025-32432.
Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable.
Unknown
This vulnerability affects a common open-source component, third-party library, or a protocol used by different products. For more information, please see: https://www.yiiframework.com/news/709/please-upgrade-to-yii-2-0-52 ; https://nvd.nist.gov/vuln/detail/CVE-2024-58136
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] | ||||
| CVSS 3.1 | CRITICAL | [email protected] |
Solution
- Update Yii 2 to version 2.0.52 or later.
- Review and apply security patches if available.
- Test the application thoroughly after updating.
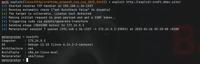
Public PoC/Exploit Available at Github
CVE-2024-58136 has a 2 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-58136.
| URL | Resource |
|---|---|
| https://github.com/yiisoft/yii2/commit/40fe496eda529fd1d933b56a1022ec32d3cd0b12 | Patch |
| https://github.com/yiisoft/yii2/compare/2.0.51...2.0.52 | Issue Tracking |
| https://github.com/yiisoft/yii2/pull/20232 | Patch |
| https://github.com/yiisoft/yii2/pull/20232#issuecomment-2252459709 | Issue Tracking |
| https://www.yiiframework.com/news/709/please-upgrade-to-yii-2-0-52 | Vendor Advisory |
| https://sensepost.com/blog/2025/investigating-an-in-the-wild-campaign-using-rce-in-craftcms/ | Exploit Third Party Advisory |
| https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-58136 | US Government Resource |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-58136 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-58136
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
CISA Bot is a GitHub bot that automatically monitors the Cybersecurity and Infrastructure Security Agency (CISA) Known Exploited Vulnerabilities (KEV) Catalog. When new vulnerabilities are published in the KEV, the bot creates GitHub issues in this repository with detailed information about each vulnerability.
Python
:beetle: Repository of CVE found by OCD people
cve exploit exploits advisory vulnerability vulnerabilities
Python Shell
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-58136 vulnerability anywhere in the article.

-
security.nl
VS meldt actief misbruik van kwetsbaarheden in Craft CMS
Aanvallers maken actief misbruik van twee kwetsbaarheden in Craft CMS, een contentmanagementsysteem voor het opzetten van websites, vergelijkbaar met WordPress. Dat meldt het Cybersecurity and Infrast ... Read more

-
TheCyberThrone
CISA adds Yii Framework and Commvault bugs to KEV Catalog
The Cybersecurity and Infrastructure Security Agency (CISA) has expanded its Known Exploited Vulnerabilities (KEV) Catalog, identifying two high-risk security flaws actively exploited in the wild. The ... Read more

-
The Hacker News
Hackers Exploit Critical Craft CMS Flaws; Hundreds of Servers Likely Compromised
Web Application Security / Vulnerability Threat actors have been observed exploiting two newly disclosed critical security flaws in Craft CMS in zero-day attacks to breach servers and gain unauthorize ... Read more
-
Daily CyberSecurity
Craft CMS Zero-Day CVE-2025-32432 Exploited with Metasploit Module Now Public
Image: Chocapikk_ Security researcher Chocapikk has published a Metasploit module for a critical zero-day vulnerability impacting Craft CMS, tracked as CVE-2025-32432 (CVSS 10). This remote code execu ... Read more

-
security.nl
Grootschalig misbruik van kritieke kwetsbaarheden in Craft CMS gemeld
Aanvallers maken op grote schaal misbruik van kritieke kwetsbaarheden in Craft CMS, zo meldt CERT Orange Cyberdefense. Updates zijn inmiddels beschikbaar, maar websites zijn al voor het uitkomen van d ... Read more

-
Cyber Security News
Critical Craft CMS RCE 0-Day Vulnerability Exploited in Attacks to Steal Data
According to security researchers at CERT Orange Cyberdefense, a critical remote code execution (RCE) vulnerability in Craft CMS is actively being exploited to breach servers and steal data. The vulne ... Read more

-
BleepingComputer
Craft CMS RCE exploit chain used in zero-day attacks to steal data
Two vulnerabilities impacting Craft CMS were chained together in zero-day attacks to breach servers and steal data, with exploitation ongoing, according to CERT Orange Cyberdefense. The vulnerabilitie ... Read more

-
Daily CyberSecurity
CVE-2025-32432 (CVSS 10): Craft CMS Hit by Critical RCE Flaw Exploited in the Wild
Craft CMS, a widely used content management system for developers and agencies, has disclosed a critical vulnerability tracked as CVE-2025-32432, affecting multiple major versions. The vulnerability, ... Read more

-
Daily CyberSecurity
Urgent: Yii 2 Vulnerability CVE-2024-58136 Under Active Exploit
A critical security vulnerability, tracked as CVE-2024-58136 (CVSS 9.1), has been uncovered in the popular PHP web application framework Yii 2, affecting versions prior to 2.0.52. With over 25 million ... Read more
The following table lists the changes that have been made to the
CVE-2024-58136 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Nov. 05, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-58136 Types: US Government Resource -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-58136 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-58136 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-58136 -
Modified Analysis by [email protected]
Jul. 30, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://sensepost.com/blog/2025/investigating-an-in-the-wild-campaign-using-rce-in-craftcms/ Types: Exploit, Third Party Advisory -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Jul. 30, 2025
Action Type Old Value New Value Added Reference https://sensepost.com/blog/2025/investigating-an-in-the-wild-campaign-using-rce-in-craftcms/ -
CVE CISA KEV Update by 9119a7d8-5eab-497f-8521-727c672e3725
May. 03, 2025
Action Type Old Value New Value Added Date Added 2025-05-02 Added Due Date 2025-05-23 Added Required Action Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable. Added Vulnerability Name Yiiframework Yii Improper Protection of Alternate Path Vulnerability -
Initial Analysis by [email protected]
Apr. 28, 2025
Action Type Old Value New Value Added CVSS V3.1 AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Added CWE NVD-CWE-Other Added CPE Configuration OR *cpe:2.3:a:yiiframework:yii:*:*:*:*:*:*:*:* versions up to (excluding) 2.0.52 Added Reference Type MITRE: https://github.com/yiisoft/yii2/commit/40fe496eda529fd1d933b56a1022ec32d3cd0b12 Types: Patch Added Reference Type MITRE: https://github.com/yiisoft/yii2/compare/2.0.51...2.0.52 Types: Issue Tracking Added Reference Type MITRE: https://github.com/yiisoft/yii2/pull/20232 Types: Patch Added Reference Type MITRE: https://github.com/yiisoft/yii2/pull/20232#issuecomment-2252459709 Types: Issue Tracking Added Reference Type MITRE: https://www.yiiframework.com/news/709/please-upgrade-to-yii-2-0-52 Types: Vendor Advisory -
New CVE Received by [email protected]
Apr. 10, 2025
Action Type Old Value New Value Added Description Yii 2 before 2.0.52 mishandles the attaching of behavior that is defined by an __class array key, a CVE-2024-4990 regression, as exploited in the wild in February through April 2025. Added CVSS V3.1 AV:N/AC:H/PR:N/UI:N/S:C/C:H/I:H/A:H Added CWE CWE-424 Added Reference https://github.com/yiisoft/yii2/commit/40fe496eda529fd1d933b56a1022ec32d3cd0b12 Added Reference https://github.com/yiisoft/yii2/compare/2.0.51...2.0.52 Added Reference https://github.com/yiisoft/yii2/pull/20232 Added Reference https://github.com/yiisoft/yii2/pull/20232#issuecomment-2252459709 Added Reference https://www.yiiframework.com/news/709/please-upgrade-to-yii-2-0-52