CVE-2024-7965
Google Chromium V8 Inappropriate Implementation Vulnerability - [Actively Exploited]
Description
Inappropriate implementation in V8 in Google Chrome prior to 128.0.6613.84 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: High)
INFO
Published Date :
Aug. 21, 2024, 9:15 p.m.
Last Modified :
Oct. 24, 2025, 2:06 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
Google Chromium V8 contains an inappropriate implementation vulnerability that allows a remote attacker to potentially exploit heap corruption via a crafted HTML page. This vulnerability could affect multiple web browsers that utilize Chromium, including, but not limited to, Google Chrome, Microsoft Edge, and Opera.
Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable.
Unknown
https://chromereleases.googleblog.com/2024/08/stable-channel-update-for-desktop_21.html; https://nvd.nist.gov/vuln/detail/CVE-2024-7965
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | HIGH | [email protected] | ||||
| CVSS 3.1 | HIGH | 134c704f-9b21-4f2e-91b3-4a467353bcc0 |
Solution
- Upgrade Chrome to version 128.0.6613.84 or later.
- Upgrade Microsoft Edge to version 128.0.2739.42 or later.
- Update affected packages.
Public PoC/Exploit Available at Github
CVE-2024-7965 has a 6 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-7965.
| URL | Resource |
|---|---|
| https://chromereleases.googleblog.com/2024/08/stable-channel-update-for-desktop_21.html | Release Notes |
| https://issues.chromium.org/issues/356196918 | Permissions Required |
| https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-7965 | US Government Resource |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-7965 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-7965
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
hacks for your school wifi, all here!
None
A bunch of V8 resources (with a security focus)
browser-exploitation v8
CVE-2024-7965是Google Chrome浏览器中V8 JavaScript引擎的一个高危漏洞。该漏洞源于V8引擎在处理特定JavaScript代码时实现不当,导致堆内存损坏。攻击者可通过诱导用户访问包含特制JavaScript的恶意网页,利用此漏洞在Chrome渲染器中执行任意代码。
cve exp poc cve-2024-7965
JavaScript
None
This repository contains PoC for CVE-2024-7965. This is the vulnerability in the V8 that occurs only within ARM64.
JavaScript
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-7965 vulnerability anywhere in the article.

-
Cyber Security News
Chrome Use-After-Free Vulnerabilities Exploited in the Wild
Google Chrome has faced a series of high-profile security incidents involving Use-After-Free (UAF) vulnerabilities, several of which have been actively exploited in the wild. These flaws, rooted in im ... Read more

-
Cybersecurity News
SAP Patches Critical BusinessObjects Vulnerability with October Security Updates
SAP has released its monthly security patch updates, addressing several vulnerabilities across its product portfolio. The October Security Patch Day includes six new security notes and six updates to ... Read more

-
Cybersecurity News
Authd Vulnerability (CVE-2024-9313) Allows User Impersonation on Ubuntu Systems
A high-severity vulnerability, CVE-2024-9313 ((CVSS 8.8)), has been discovered in Authd, an authentication daemon used for secure identity and access management in Ubuntu machines. This flaw could all ... Read more
-
Cybersecurity News
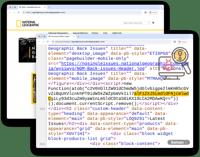
Cybercriminals Exploit CosmicSting Vulnerability, Hacking Thousands of Adobe Commerce and Magento Stores
Malware in the National Geographic store | Image: SansecIn a significant cybersecurity breach this summer, cybercriminals compromised approximately 5% of all Adobe Commerce and Magento stores, affecti ... Read more
-
Cybersecurity News
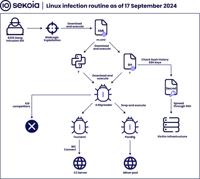
Hadooken & K4Spreader Malware: 8220 Gang’s Latest Cloud Hijacking Tools
Linux infection routine | Image: Sekoia’s Threat Detection & Research (TDR) teamThe notorious 8220 Gang, a China-based intrusion set first identified in 2018, continues to expand its arsenal with two ... Read more

-
Cybersecurity News
Severe Unauthenticated RCE Flaw (CVSS 9.9) in GNU/Linux Systems Awaiting Full Disclosure
A critical security vulnerability affecting all GNU/Linux systems—and potentially others—has been identified by renowned security researcher Simone Margaritelli. The vulnerability, which allows for un ... Read more

-
Cybersecurity News
CVE-2024-8956 (CVSS 9.1): PTZOptics Cameras Vulnerable to Remote Attacks
A recently disclosed security flaw, CVE-2024-8956, poses a significant risk to users of certain PTZ cameras, including popular models from PTZOptics. This vulnerability, rated CVSS 9.1, opens the door ... Read more

-
Cybersecurity News
GreyNoise Intelligence Uncovers New Internet Noise Storm with Potential China Link and Cryptic “LOVE” Message
GreyNoise Intelligence has recently released findings regarding a new and increasingly complex wave of “Noise Storms” – massive, enigmatic surges of fake traffic that have baffled experts since 2020. ... Read more
-
Cybersecurity News
Critical Security Flaws in Camaleon CMS Put Web Servers at Risk – Users Urged to Upgrade Immediately
In a significant development for website owners and administrators using Camaleon CMS, a critical security update has been released to address several vulnerabilities, some of which are already being ... Read more
-
Cybersecurity News
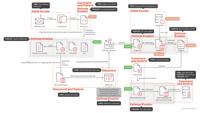
Sophisticated Cyber Espionage: Earth Baxia Uses CVE-2024-36401 and Cobalt Strike to Infiltrate APAC
Overview of the attack chain | Image: Trend MicroIn a recent report from Trend Micro, the cyber espionage group Earth Baxia has been identified targeting government organizations in Taiwan and potenti ... Read more
-
Cybersecurity News
PoC Exploit Released for CVE-2024-7965 Zero-Day Chrome Vulnerability
Technical specifics and a proof-of-concept (PoC) exploit have been made available for a recently uncovered zero-day vulnerability, CVE-2024-7965, in the V8 JavaScript engine. Analyzed by experts at BI ... Read more
-
Cybersecurity News
BadIIS Malware : 35+ IIS Servers Compromised in DragonRank Campaign
A recent report from Cisco Talos has exposed a new threat actor named DragonRank, a Chinese-speaking group specializing in SEO manipulation and cyberattacks. This group operates by exploiting vulnerab ... Read more

-
Cybersecurity News
CVE-2024-8522 (CVSS 10): LearnPress SQLi Flaw Leaves 90K+ WordPress Sites at Risk
A critical SQL injection vulnerability has been discovered in LearnPress, a popular WordPress plugin used to create and manage online courses. The flaw, tracked as CVE-2024-8522, carries a maximum CVS ... Read more

-
TheCyberThrone
CISA KEV Update Part II – September 2024.
The US CISA added below vulnerabilities to the Known Exploited Vulnerability Catalog based on the evidence of active exploitationCVE-2024-40766 SonicWall SonicOS contains an improper access control vu ... Read more

-
Cybersecurity News
ECDSA Vulnerability in YubiKey: What You Need to Know
OLYMPUS DIGITAL CAMERAIn a recent security advisory, Yubico disclosed a moderate vulnerability (CVE-2024-45678) affecting several of its hardware security devices, including the widely-used YubiKey 5 ... Read more

-
The Hacker News
RansomHub Ransomware Group Targets 210 Victims Across Critical Sectors
Threat actors linked to the RansomHub ransomware group encrypted and exfiltrated data from at least 210 victims since its inception in February 2024, the U.S. government said. The victims span various ... Read more

-
The Register
Check your IP cameras: There's a new Mirai botnet on the rise
in brief A series of IP cameras still used all over the world, despite being well past their end of life, have been exploited to create a new Mirai botnet. The vulnerability (CVSS 8.7, CVE-2024-7029) ... Read more

-
The Hacker News
North Korean Hackers Deploy FudModule Rootkit via Chrome Zero-Day Exploit
Rootkit / Threat Intelligence A recently patched security flaw in Google Chrome and other Chromium web browsers was exploited as a zero-day by North Korean actors in a campaign designed to deliver the ... Read more

-
The Hacker News
Atlassian Confluence Vulnerability Exploited in Crypto Mining Campaigns
Cryptojacking / Vulnerability Threat actors are actively exploiting a now-patched, critical security flaw impacting the Atlassian Confluence Data Center and Confluence Server to conduct illicit crypto ... Read more

-
TheCyberThrone
CISA adds CVE-2024-7965 Chrome bug to its KEV catalog
The U.S. CISA added Google Chrome vulnerability to its Known Exploited Vulnerability Catalog following the mass exploitation in the wild.CVE-2024-7965; Google Chromium V8 contains an inappropriate imp ... Read more
The following table lists the changes that have been made to the
CVE-2024-7965 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Oct. 24, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-7965 Types: US Government Resource -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-7965 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-7965 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-7965 -
Reanalysis by [email protected]
Sep. 18, 2024
Action Type Old Value New Value Added CPE Configuration OR *cpe:2.3:a:microsoft:edge_chromium:*:*:*:*:*:*:*:* versions up to (excluding) 128.0.2739.42 -
CVE CISA KEV Update by 9119a7d8-5eab-497f-8521-727c672e3725
Aug. 29, 2024
Action Type Old Value New Value Added Vulnerability Name Google Chromium V8 Inappropriate Implementation Vulnerability Added Required Action Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable. Added Due Date 2024-09-18 Added Date Added 2024-08-28 -
Initial Analysis by [email protected]
Aug. 26, 2024
Action Type Old Value New Value Added CVSS V3.1 NIST AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H Changed Reference Type https://chromereleases.googleblog.com/2024/08/stable-channel-update-for-desktop_21.html No Types Assigned https://chromereleases.googleblog.com/2024/08/stable-channel-update-for-desktop_21.html Release Notes Changed Reference Type https://issues.chromium.org/issues/356196918 No Types Assigned https://issues.chromium.org/issues/356196918 Permissions Required Added CWE NIST CWE-787 Added CPE Configuration OR *cpe:2.3:a:google:chrome:*:*:*:*:*:*:*:* versions up to (excluding) 128.0.6613.84 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Aug. 22, 2024
Action Type Old Value New Value Added CWE CISA-ADP CWE-358 Added CVSS V3.1 CISA-ADP AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H -
CVE Received by [email protected]
Aug. 21, 2024
Action Type Old Value New Value Added Description Inappropriate implementation in V8 in Google Chrome prior to 128.0.6613.84 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: High) Added Reference Chrome https://chromereleases.googleblog.com/2024/08/stable-channel-update-for-desktop_21.html [No types assigned] Added Reference Chrome https://issues.chromium.org/issues/356196918 [No types assigned]