CVE-2025-0411
7-Zip Mark of the Web Bypass Vulnerability - [Actively Exploited]
Description
7-Zip Mark-of-the-Web Bypass Vulnerability. This vulnerability allows remote attackers to bypass the Mark-of-the-Web protection mechanism on affected installations of 7-Zip. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the handling of archived files. When extracting files from a crafted archive that bears the Mark-of-the-Web, 7-Zip does not propagate the Mark-of-the-Web to the extracted files. An attacker can leverage this vulnerability to execute arbitrary code in the context of the current user. Was ZDI-CAN-25456.
INFO
Published Date :
Jan. 25, 2025, 5:15 a.m.
Last Modified :
Oct. 27, 2025, 5:05 p.m.
Remotely Exploit :
No
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
7-Zip contains a protection mechanism failure vulnerability that allows remote attackers to bypass the Mark-of-the-Web security feature to execute arbitrary code in the context of the current user.
Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable.
Unknown
https://www.7-zip.org/history.txt ; https://nvd.nist.gov/vuln/detail/CVE-2025-0411
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.0 | HIGH | [email protected] | ||||
| CVSS 3.1 | HIGH | [email protected] |
Solution
- Update 7-Zip to the latest version.
- Ensure all archives are extracted securely.
- Educate users about handling untrusted archives.
Public PoC/Exploit Available at Github
CVE-2025-0411 has a 18 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2025-0411.
| URL | Resource |
|---|---|
| https://www.zerodayinitiative.com/advisories/ZDI-25-045/ | Third Party Advisory VDB Entry |
| http://www.openwall.com/lists/oss-security/2025/01/24/6 | Mailing List |
| https://security.netapp.com/advisory/ntap-20250207-0005/ | Third Party Advisory |
| https://www.vicarius.io/vsociety/posts/cve-2025-0411-7-zip-mitigation-vulnerability | Mitigation |
| https://www.vicarius.io/vsociety/posts/cve-2025-0411-detection-7-zip-vulnerability | Mitigation |
| https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-0411 | US Government Resource |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2025-0411 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2025-0411
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
Mirror of https://github.com/nomi-sec/PoC-in-GitHub
None
Shell
None
CVE-2025-0411
C++
Rust Macros No Recoil Guide 🚀 Boost Aim Like a Pro in C and Python
CVE-2025-0411 7-Zip Mark-of-the-Web Bypass
This repository contains POC scenarios as part of CVE-2025-0411 MotW bypass.
7zip cve cve-2025-0411 cve-2025-0411-poc payload-delivery poc
C++
None
C++
None
Python C++
None
HTML Python Shell
7-Zip Mark-of-the-Web绕过漏洞PoC(CVE-2025-0411)
C++
This repository contains POC scenarios as part of CVE-2025-0411 MotW bypass.
7zip cve cve-2025-0411 cve-2025-0411-poc payload-delivery poc
This repository contains POC scenarios as part of CVE-2025-0411 MotW bypass.
7zip cve payload-delivery poc cve-2025-0411 cve-2025-0411-poc
C++
None
Python Dockerfile C++ Shell JavaScript TypeScript HTML CSS PHP Blade
CISA Bot is a GitHub bot that automatically monitors the Cybersecurity and Infrastructure Security Agency (CISA) Known Exploited Vulnerabilities (KEV) Catalog. When new vulnerabilities are published in the KEV, the bot creates GitHub issues in this repository with detailed information about each vulnerability.
Python
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2025-0411 vulnerability anywhere in the article.

-
Daily CyberSecurity
The 7-Zip Trap: How a 25-Year-Old Domain Was Weaponized to Turn Your PC into a Proxy Bot
Security researchers have recently unveiled a sophisticated stratagem wherein adversaries gained control of the domain 7zip[.]com to proliferate deleterious software. It is paramount to note that the ... Read more
-
Daily CyberSecurity
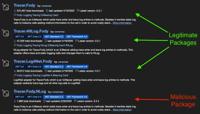
5-Year Threat: Malicious NuGet Package Used Homoglyphs and Typosquatting to Steal Crypto Wallets
Image: Socket A malicious NuGet package masquerading as a popular .NET logging tool has been caught stealing cryptocurrency wallet data for over five years. The package, Tracer.Fody.NLog, successfully ... Read more

-
CybersecurityNews
New TamperedChef Malware Leverages Productivity Tools to Gain Access and Exfiltrate Sensitive Data
A sophisticated malware campaign has emerged that weaponizes seemingly legitimate productivity tools to infiltrate systems and steal sensitive information. The TamperedChef malware represents a concer ... Read more

-
Daily CyberSecurity
TamperedChef Malware Rises: Deceptive Apps Use Signed Binaries and SEO Poisoning to Hijack Browsers
Field Effect’s Threat Intelligence team has uncovered a new wave of the TamperedChef malware campaign, leveraging digitally signed binaries, deceptive packaging, and browser hijackers to deliver malwa ... Read more

-
CybersecurityNews
7-Zip Arbitrary File Write Vulnerability Let Attackers Execute Arbitrary Code
A newly disclosed security vulnerability in the popular 7-Zip file compression software has raised significant concerns in the cybersecurity community. CVE-2025-55188, discovered and reported by secur ... Read more

-
Trend Micro
Proactive Security Insights for SharePoint Attacks (CVE-2025-53770 and CVE-2025-53771)
Key takeaways CVE-2025-53770 and CVE-2025-53771 are vulnerabilities affecting on-premise Microsoft SharePoint Servers, which enables an attacker to upload malicious files and extract cryptographic sec ... Read more
-
Daily CyberSecurity
Two Vulnerabilities in 7-Zip Could Trigger Denial of Service
Researchers have disclosed two newly identified vulnerabilities in 7-Zip, one of the world’s most widely used open-source file archivers. Both issues—CVE-2025-53816 and CVE-2025-53817—affect versions ... Read more

-
Cyber Security News
WinZip MotW Bypass Vulnerability Let Hackers Execute Malicious Code Silently
Cybersecurity researchers have discovered a critical vulnerability in WinZip that enables attackers to bypass Windows’ Mark-of-the-Web (MotW) security feature, potentially allowing malicious code to e ... Read more

-
Daily CyberSecurity
CVE-2025-33028: WinZip Flaw Exposes Users to Silent Code Execution via MotW Bypass, No Patch
A security flaw has been unearthed in WinZip, the popular file compression utility, placing millions of users at risk of silent code execution. Tracked as CVE-2025-33028, this vulnerability enables a ... Read more

-
Kaspersky
Protecting against attacks in ZIP, RAR, CAB, MSI, ISO and other archives | Kaspersky official blog
Archiving programs designed to simplify file storage and transfers have become common tools not only for users but also for attackers. Malicious archives are regularly found in both targeted attacks a ... Read more

-
Help Net Security
WinRAR MotW bypass flaw fixed, update ASAP (CVE-2025-31334)
WinRAR users, upgrade your software as soon as possible: a vulnerability (CVE-2025-31334) that could allow attackers to bypass Windows’ Mark of the Web (MotW) security warning and execute arbitrary co ... Read more

-
TheCyberThrone
TheCyberThrone CyberSecurity Newsletter Top 5 Articles – March 2025
Welcome to TheCyberThrone cybersecurity month in review will be posted covering the important security happenings . This review is for the month ending March 2025Subscribers favorite #1CVE-2025-0411 i ... Read more

-
Cyber Security News
WinRAR “Mark of the Web” Bypass Vulnerability Let Attackers Arbitrary Code
A newly disclosed vulnerability in WinRAR allows attackers to bypass a core Windows security mechanism, enabling arbitrary code execution on affected systems. Tracked as CVE-2025-31334, this flaw impa ... Read more
-
Daily CyberSecurity
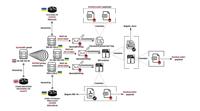
Bulletproof Hosting Fuels Russia-Linked Intrusion Sets’ Global Cyber Campaign
Layout of UAC-0006’s spam infrastructure by the end of 2023 and early 2024 | Image: IntrinsecA recent report by Intrinsec has uncovered the activities of Russia-aligned intrusion sets, UAC-0050 and UA ... Read more

-
The Hacker News
⚡ THN Weekly Recap: Top Cybersecurity Threats, Tools and Tips [10 February]
Cybersecurity / Weekly Recap In cybersecurity, the smallest crack can lead to the biggest breaches. A leaked encryption key, an unpatched software bug, or an abandoned cloud storage bucket—each one se ... Read more

-
The Hacker News
XE Hacker Group Exploits VeraCore Zero-Day to Deploy Persistent Web Shells
Threat actors have been observed exploiting multiple security flaws in various software products, including Progress Telerik UI for ASP.NET AJAX and Advantive VeraCore, to drop reverse shells and web ... Read more

-
Help Net Security
Week in review: Exploited 7-Zip 0-day flaw, crypto-stealing malware found on App Store, Google Play
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Russian cybercrooks exploiting 7-Zip zero-day vulnerability (CVE-2025-0411) CVE-2025-0411, a Mark-of-t ... Read more

-
Ars Technica
7-Zip 0-day was exploited in Russia’s ongoing invasion of Ukraine
Researchers said they recently discovered a zero-day vulnerability in the 7-Zip archiving utility that was actively exploited as part of Russia's ongoing invasion of Ukraine. The vulnerability allowed ... Read more

-
Help Net Security
Cybercrime gang exploited VeraCore zero-day vulnerabilities for years (CVE-2025-25181, CVE-2024-57968)
XE Group, a cybercriminal outfit that has been active for over a decade, has been quietly exploiting zero-day vulnerabilities (CVE-2025-25181, CVE-2024-57968) in VeraCore software, a popular solution ... Read more

-
Help Net Security
Swap EOL Zyxel routers, upgrade Netgear ones!
There will be no patches for EOL Zyxel routers under attack via CVE-2024-40891, the company has confirmed. Meanwhile, Netgear has issued patches for critical flaws affecting its routers and wireless a ... Read more
The following table lists the changes that have been made to the
CVE-2025-0411 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Oct. 27, 2025
Action Type Old Value New Value Added CPE Configuration OR *cpe:2.3:a:netapp:active_iq_unified_manager:-:*:*:*:*:windows:*:* Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-0411 Types: US Government Resource -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-0411 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-0411 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-0411 -
Initial Analysis by [email protected]
Feb. 12, 2025
Action Type Old Value New Value Added CVSS V3.1 NIST AV:L/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:H Added CWE NIST NVD-CWE-noinfo Added CPE Configuration OR *cpe:2.3:a:7-zip:7-zip:*:*:*:*:*:*:*:* versions up to (excluding) 24.09 Changed Reference Type http://www.openwall.com/lists/oss-security/2025/01/24/6 No Types Assigned http://www.openwall.com/lists/oss-security/2025/01/24/6 Mailing List Changed Reference Type https://security.netapp.com/advisory/ntap-20250207-0005/ No Types Assigned https://security.netapp.com/advisory/ntap-20250207-0005/ Third Party Advisory Changed Reference Type https://www.vicarius.io/vsociety/posts/cve-2025-0411-7-zip-mitigation-vulnerability No Types Assigned https://www.vicarius.io/vsociety/posts/cve-2025-0411-7-zip-mitigation-vulnerability Mitigation Changed Reference Type https://www.vicarius.io/vsociety/posts/cve-2025-0411-detection-7-zip-vulnerability No Types Assigned https://www.vicarius.io/vsociety/posts/cve-2025-0411-detection-7-zip-vulnerability Mitigation Changed Reference Type https://www.zerodayinitiative.com/advisories/ZDI-25-045/ No Types Assigned https://www.zerodayinitiative.com/advisories/ZDI-25-045/ Third Party Advisory, VDB Entry -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Feb. 07, 2025
Action Type Old Value New Value Added Reference https://security.netapp.com/advisory/ntap-20250207-0005/ -
CVE CISA KEV Update by 9119a7d8-5eab-497f-8521-727c672e3725
Feb. 07, 2025
Action Type Old Value New Value Added Date Added 2025-02-06 Added Due Date 2025-02-27 Added Vulnerability Name 7-Zip Mark of the Web Bypass Vulnerability Added Required Action Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable. -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Jan. 29, 2025
Action Type Old Value New Value Added Reference https://www.vicarius.io/vsociety/posts/cve-2025-0411-7-zip-mitigation-vulnerability Added Reference https://www.vicarius.io/vsociety/posts/cve-2025-0411-detection-7-zip-vulnerability -
New CVE Received by [email protected]
Jan. 25, 2025
Action Type Old Value New Value Added Description 7-Zip Mark-of-the-Web Bypass Vulnerability. This vulnerability allows remote attackers to bypass the Mark-of-the-Web protection mechanism on affected installations of 7-Zip. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the handling of archived files. When extracting files from a crafted archive that bears the Mark-of-the-Web, 7-Zip does not propagate the Mark-of-the-Web to the extracted files. An attacker can leverage this vulnerability to execute arbitrary code in the context of the current user. Was ZDI-CAN-25456. Added CVSS V3 AV:L/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:H Added CWE CWE-693 Added Reference https://www.zerodayinitiative.com/advisories/ZDI-25-045/ -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Jan. 25, 2025
Action Type Old Value New Value Added Reference http://www.openwall.com/lists/oss-security/2025/01/24/6