CVE-2025-36911
Cisco Wi-Fi Key-Based Pairing Information Disclosure Vulnerability
Description
In key-based pairing, there is a possible ID due to a logic error in the code. This could lead to remote (proximal/adjacent) information disclosure of user's conversations and location with no additional execution privileges needed. User interaction is not needed for exploitation.
INFO
Published Date :
Jan. 15, 2026, 6:16 p.m.
Last Modified :
Jan. 28, 2026, 5:16 a.m.
Remotely Exploit :
No
Source :
[email protected]
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | HIGH | 134c704f-9b21-4f2e-91b3-4a467353bcc0 |
Solution
- Review and correct the key-based pairing logic.
- Validate pairing process inputs carefully.
- Implement secure data handling practices.
- Test for unintended information exposure.
Public PoC/Exploit Available at Github
CVE-2025-36911 has a 30 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2025-36911.
| URL | Resource |
|---|---|
| https://source.android.com/docs/security/bulletin/pixel/2026/2026-01-01 | |
| https://whisperpair.eu/ | Exploit |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2025-36911 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2025-36911
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
BLUE-SPY (Bluetooth Low Energy Universal Exploit - Security Penetration Testing) is a professional security assessment tool for analyzing CVE-2025-36911 vulnerabilities in Google's Fast Pair protocol implementation.
Python
ESP32-DIV HaleHound Edition for Cheap Yellow Display - Multi-protocol offensive security toolkit
bluetooth cc1101 cheap-yellow-display cyd esp32 hacking nrf24l01 offensive-security pentest security security-tools subghz wifi esp32-diy
C++ C
Mirror of https://github.com/nomi-sec/PoC-in-GitHub
🛡️ Scan for CVE-2025-36911 vulnerabilities with WPair, a research tool designed for Android developers using Kotlin. Secure your applications effectively.
🔍 Scan and research CVE-2025-36911 vulnerabilities with WPair, a specialized tool for Android built in Kotlin, ensuring your applications remain secure.
aliases appengine-java coronavirus covid-19 dart email encrypted epidemiology evernote firebase flask flutter hacktoberfest markdown note-taking notes privacy secure simplelogin snippets
Kotlin
Exploit of the CVE-2025-36911 vulnerability in Python for testing our own equipment
cve-2025-36911 pentesting
Python
Whisper pair bluetooth exploit for linux (POC for educational purposes)
Python
Whisper pair bluetooth exploit for android (POC for educational purposes)
Kotlin Batchfile
Whisper pair bluetooth exploit for windows (POC for educational purposes)
Python
Whisper Pair python script
Python
A security research tool that identifies and demonstrates the CVE-2025-36911: Fast Pair Pairing Mode Bypass vulnerability
Scans for BLE devices and identifies potentially vulnerable devices * based on device name, manufacturer ID, and advertised security information
C++
WhisperPair Python
ble bluetooth cve esp32 esp32-c6-devkitc-1-n8 exploit python security vulnerability fast-pair
C++ Python
A Vulnerablity Scanner for Whisper Pair (CVE-2025-36911)
Python
whisperPAIR poc
Python
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2025-36911 vulnerability anywhere in the article.

-
Kaspersky
How to protect yourself from Bluetooth-headset tracking and the WhisperPair attack | Kaspersky official blog
A newly discovered vulnerability named WhisperPair can turn Bluetooth headphones and headsets from many well-known brands into personal tracking beacons — regardless of whether the accessories are cur ... Read more

-
CybersecurityNews
WPair – Scanner Tool to Detect WhisperPair Flaw in Google’s Fast Pair Protocol
WPair is an Android application designed to identify and demonstrate the CVE-2025-36911 vulnerability affecting millions of Bluetooth audio devices worldwide. The tool addresses a critical authenticat ... Read more

-
CybersecurityNews
WhisperPair Attack Allows Hijacking of Laptops, Earbuds Without User Consent – Millions Affected
A critical vulnerability in Google’s Fast Pair protocol that allows attackers to hijack Bluetooth audio accessories and track users without their knowledge or consent. Security researchers from KU Le ... Read more
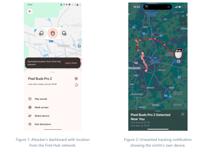
-
Daily CyberSecurity
WhisperPair: Critical Fast Pair Flaw Exposes Headphones to Hijacking
Image: Researchers Your high-end Bluetooth headphones might be listening to more than just your music. A new report from Researchers with KU Leuven’s Computer Security and Industrial Cryptography grou ... Read more

-
BleepingComputer
Critical WhisperPair flaw lets hackers track, eavesdrop via Bluetooth audio devices
Security researchers have discovered a critical vulnerability in Google's Fast Pair protocol that can allow attackers to hijack Bluetooth audio accessories, track users, and eavesdrop on their convers ... Read more
The following table lists the changes that have been made to the
CVE-2025-36911 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
CVE Modified by [email protected]
Jan. 28, 2026
Action Type Old Value New Value Added Reference https://source.android.com/docs/security/bulletin/pixel/2026/2026-01-01 Removed Reference https://source.android.com/security/bulletin/pixel/2026-01-01 Removed Reference Type https://source.android.com/security/bulletin/pixel/2026-01-01 Types: Vendor Advisory -
Initial Analysis by [email protected]
Jan. 21, 2026
Action Type Old Value New Value Added CWE NVD-CWE-noinfo Added CPE Configuration OR *cpe:2.3:o:google:android:-:*:*:*:*:*:*:* Added Reference Type Google Devices: https://source.android.com/security/bulletin/pixel/2026-01-01 Types: Vendor Advisory Added Reference Type CISA-ADP: https://whisperpair.eu/ Types: Exploit -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Jan. 15, 2026
Action Type Old Value New Value Added CVSS V3.1 AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:N Added Reference https://whisperpair.eu/ -
New CVE Received by [email protected]
Jan. 15, 2026
Action Type Old Value New Value Added Description In key-based pairing, there is a possible ID due to a logic error in the code. This could lead to remote (proximal/adjacent) information disclosure of user's conversations and location with no additional execution privileges needed. User interaction is not needed for exploitation. Added Reference https://source.android.com/security/bulletin/pixel/2026-01-01


