CVE-2025-41115
Incorrect privilege assignment
Description
SCIM provisioning was introduced in Grafana Enterprise and Grafana Cloud in April to improve how organizations manage users and teams in Grafana by introducing automated user lifecycle management. In Grafana versions 12.x where SCIM provisioning is enabled and configured, a vulnerability in user identity handling allows a malicious or compromised SCIM client to provision a user with a numeric externalId, which in turn could allow to override internal user IDs and lead to impersonation or privilege escalation. This vulnerability applies only if all of the following conditions are met: - `enableSCIM` feature flag set to true - `user_sync_enabled` config option in the `[auth.scim]` block set to true
INFO
Published Date :
Nov. 21, 2025, 3:15 p.m.
Last Modified :
Jan. 8, 2026, 4:39 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] | ||||
| CVSS 3.1 | CRITICAL | [email protected] |
Solution
- Upgrade Grafana to a patched version.
- Ensure SCIM provisioning is securely configured.
- Disable SCIM if not actively used.
Public PoC/Exploit Available at Github
CVE-2025-41115 has a 3 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2025-41115.
| URL | Resource |
|---|---|
| https://grafana.com/security/security-advisories/CVE-2025-41115 | Broken Link |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2025-41115 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2025-41115
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
Mirror of https://github.com/nomi-sec/PoC-in-GitHub
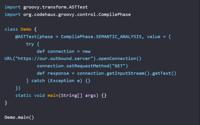
Exploit and test stand for CVE-2025-41115
Python Shell
CVE-2025-41115
Python
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2025-41115 vulnerability anywhere in the article.

-
The Cyber Express
Cyble Research Discovers ShadowHS, an In-Memory Linux Framework for Long-Term Access
Cyble Research & Intelligence Labs (CRIL) has uncovered a post-exploitation Linux framework called ShadowHS, designed for stealthy, in-memory operations. Unlike traditional malware, ShadowHS leverages ... Read more

-
The Cyber Express
Apache Syncope Passwords at Risk from Newly Disclosed CVE-2025-65998
A critical security flaw has been uncovered in Apache Syncope, the widely used open-source identity management system, potentially putting organizations at risk of exposing sensitive password informat ... Read more
-
The Cyber Express
CISA Adds Oracle Identity Manager Vulnerability to KEV Database
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added an Oracle Identity Manager vulnerability to its Known Exploited Vulnerabilities database after the SANS Internet Storm Center ... Read more

-
The Cyber Express
Grafana Flags Maximum-Severity SCIM Vulnerability Enabling Privilege Escalation
Grafana Labs has issued a warning regarding a maximum-severity security flaw, identified as CVE-2025-41115, affecting its Enterprise product. The vulnerability can allow attackers to impersonate admin ... Read more

-
BleepingComputer
Grafana warns of max severity admin spoofing vulnerability
Grafana Labs is warning of a maximum severity vulnerability (CVE-2025-41115) in its Enterprise product that can be exploited to treat new users as administrators or for privilege escalation. The issue ... Read more

-
The Hacker News
Grafana Patches CVSS 10.0 SCIM Flaw Enabling Impersonation and Privilege Escalation
Nov 21, 2025Ravie LakshmananVulnerability / Threat Mitigation Grafana has released security updates to address a maximum severity security flaw that could allow privilege escalation or user imperson ... Read more
The following table lists the changes that have been made to the
CVE-2025-41115 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Initial Analysis by [email protected]
Jan. 08, 2026
Action Type Old Value New Value Added CVSS V3.1 AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Added CPE Configuration OR *cpe:2.3:a:grafana:grafana:*:*:*:*:enterprise:*:*:* versions from (including) 12.0.0 up to (excluding) 12.2.1 Added Reference Type Grafana Labs: https://grafana.com/security/security-advisories/CVE-2025-41115 Types: Broken Link -
New CVE Received by [email protected]
Nov. 21, 2025
Action Type Old Value New Value Added Description SCIM provisioning was introduced in Grafana Enterprise and Grafana Cloud in April to improve how organizations manage users and teams in Grafana by introducing automated user lifecycle management. In Grafana versions 12.x where SCIM provisioning is enabled and configured, a vulnerability in user identity handling allows a malicious or compromised SCIM client to provision a user with a numeric externalId, which in turn could allow to override internal user IDs and lead to impersonation or privilege escalation. This vulnerability applies only if all of the following conditions are met: - `enableSCIM` feature flag set to true - `user_sync_enabled` config option in the `[auth.scim]` block set to true Added CVSS V3.1 AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H Added Reference https://grafana.com/security/security-advisories/CVE-2025-41115 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Nov. 21, 2025
Action Type Old Value New Value Added CWE CWE-266