CVE-2025-54322
Xspeeder SXZOS Remote Code Execution Vulnerability
Description
Xspeeder SXZOS through 2025-12-26 allows root remote code execution via base64-encoded Python code in the chkid parameter to vLogin.py. The title and oIP parameters are also used.
INFO
Published Date :
Dec. 27, 2025, 2:15 p.m.
Last Modified :
Jan. 9, 2026, 8:33 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] | ||||
| CVSS 3.1 | CRITICAL | MITRE-CVE | ||||
| CVSS 3.1 | CRITICAL | [email protected] |
Solution
- Sanitize all user-supplied input.
- Validate and restrict input for chkid parameter.
- Disable or restrict access to vLogin.py.
- Update Xspeeder SXZOS to the latest version.
Public PoC/Exploit Available at Github
CVE-2025-54322 has a 3 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2025-54322.
| URL | Resource |
|---|---|
| https://pwn.ai/blog/cve-2025-54322-zeroday-unauthenticated-root-rce-affecting-70-000-hosts | Exploit Third Party Advisory |
| https://www.xspeeder.com | Product |
| https://pwn.ai/blog/cve-2025-54322-zeroday-unauthenticated-root-rce-affecting-70-000-hosts | Exploit Third Party Advisory |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2025-54322 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2025-54322
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
None
Python
CVE-2025-54322 - XSpeeder SXZOS Pre-Auth RCE 0day Finder Quick
Python
爬取secwiki和xuanwu.github.io/sec.today,分析安全信息站点、安全趋势、提取安全工作者账号(twitter,weixin,github等)
Python HTML
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2025-54322 vulnerability anywhere in the article.
-
Daily CyberSecurity
One Request to Rule Them All: Critical Trendnet Flaw (CVE-2025-15471) Allows Total Takeover
A critical pre-authentication command injection vulnerability has been uncovered in the Trendnet TEW-713RE Wi-Fi extender, allowing remote attackers to seize full control of the device with a single H ... Read more

-
Daily CyberSecurity
CVE-2025-60262: Critical Misconfiguration in H3C Wireless Gear Hands Control to Hackers
A glaring configuration oversight in select H3C wireless controllers and access points has opened the door for remote attackers to seize root-level control of the devices. The vulnerability, tracked a ... Read more
-
Daily CyberSecurity
Self-Hosters Beware: 3 Critical Coolify Flaws Grant Root Access
The self-hosting community is on high alert following the disclosure of three critical vulnerabilities in Coolify, the open-source platform designed to simplify application deployment. Security resear ... Read more

-
Daily CyberSecurity
The 1000Hz Illusion: NVIDIA Unveils G-SYNC Pulsar and DLSS 4.5 at CES 2026
As CES 2026 approaches, NVIDIA unveiled a slate of consumer-facing updates for gamers and creators during its pre-show event. Highlights include G-SYNC Pulsar technology, capable of delivering 1000Hz- ... Read more

-
Daily CyberSecurity
CVE-2025-14026: Forcepoint DLP Flaw Lets Attackers Unchain Restricted Python
A high-severity vulnerability in the Forcepoint One DLP Client has been disclosed, revealing a method for attackers to break out of a vendor-imposed “sandbox” and execute arbitrary code on protected e ... Read more
-
Daily CyberSecurity
Google Patches High-Severity “WebView” Flaw in Chrome 143
Google has announced an important security update for the Stable channel of its Chrome browser, rolling out patches to Windows, Mac, and Linux users to address a high-severity vulnerability that could ... Read more

-
Daily CyberSecurity
Zero-Day Chronomaly Exploit Grants Root Access to Vulnerable Linux Kernels
Cybersecurity researcher farazsth98 has presented new findings related to an exploited security issue in Linux kernel flaw that could be abused by an attacker to privilege escalation. The vulnerabilit ... Read more

-
Daily CyberSecurity
CVE-2025-67732: Dify Patch Fixes High-Severity Plaintext API Key Exposure
Dify, the popular open-source platform used by developers to build Large Language Model (LLM) applications and RAG pipelines, has patched a high-severity vulnerability that could leave administrators ... Read more
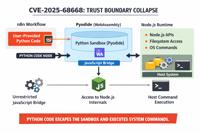
-
Daily CyberSecurity
n8n Sandbox Escape: How CVE-2025-68668 Turns Workflows into Weapons
A critical vulnerability in the popular workflow automation platform n8n has been dissected in a new analysis by security researcher Rhoda Smart, revealing how a feature designed for flexibility becam ... Read more

-
Daily CyberSecurity
The Robotics Revolution: NVIDIA Unveils Physical AI and the Jetson T4000 at CES 2026
At CES 2026 this year, NVIDIA shifted its focus decisively from the digital realm of generative AI toward “Physical AI”—systems designed to interact directly with the real world. NVIDIA CEO Jensen Hua ... Read more

-
Daily CyberSecurity
The Desk-Side Revolution: NVIDIA’s DGX Spark Update Delivers 2.5× AI Speed Boost
As downloads of open-source AI models and frameworks are expected to surge explosively in 2026, NVIDIA announced a major update to its desktop AI development platform, DGX Spark, at CES 2026. This upd ... Read more

-
Daily CyberSecurity
CVE-2025-68428: Critical Flaw in jsPDF Library Allows Server-Side File Theft
A critical vulnerability has been discovered in jsPDF, one of the most popular JavaScript libraries for generating PDF documents. The flaw, assigned a scorching CVSS score of 9.2, allows attackers to ... Read more

-
Daily CyberSecurity
Aiohttp Patches Seven Vulnerabilities Including High-Severity DoS Risks
Maintainers of aiohttp, the popular asynchronous HTTP client/server framework for Python, have released a sweeping security update addressing seven distinct vulnerabilities. The update, version 3.13.3 ... Read more
-
Daily CyberSecurity
Apache SIS Patch Blocks XML Attack That Leaks Server Files
The Apache Software Foundation has issued a security advisory for the Apache Spatial Information System (SIS), a key Java library used for developing geospatial applications. A newly discovered vulner ... Read more

-
Daily CyberSecurity
CVE-2025-66518: High-Severity Flaw in Apache Kyuubi Exposes Local Server Files
Apache Kyuubi, the distributed gateway designed to provide secure, serverless SQL access to massive data lakes, has patched a high-severity vulnerability that could allow unauthorized access to the se ... Read more
-
Daily CyberSecurity
Attacking from Within: How Adobe ColdFusion Admins Can Weaponize Remote Shares
Image: Brian Adobe has issued critical updates for its ColdFusion platform after security researcher Brian Reilly uncovered a clever logic flaw that allows authenticated administrators to turn a stand ... Read more
-
Daily CyberSecurity
New TCC Bypass (CVE-2025-43530) Exposes macOS to Unchecked Automation
Apple’s privacy fortress, the Transparency, Consent, and Control (TCC) framework, has been breached once again. Security researcher Mickey Jin (@patch1t) has disclosed a sophisticated new vulnerabilit ... Read more
-
Daily CyberSecurity
Riot Games Login Outage Traced to Expired SSL Certificate
odified Chrome TLS certificate error page Source: urlscan) The well-known game developer Riot Games recently suffered another widespread service disruption after failing to renew an expired digital ce ... Read more

-
Daily CyberSecurity
Systems over Slop: Nadella’s 2026 AI Vision Sparks “Microslop” Revolt
As the first week of 2026 unfolds, Microsoft CEO Satya Nadella published his latest reflections on the state of the AI industry on his newly launched personal blog, SN Scratchpad. In the post, he urge ... Read more

-
Daily CyberSecurity
CVE-2026-21440: New AdonisJS 9.2 Critical Flaw Allows Arbitrary File Writes and RCE
A critical security vulnerability has been discovered in AdonisJS, a popular full-stack Node.js web framework known for its focus on ergonomics and speed. The flaw, assigned a CVSS score of 9.2, resid ... Read more
The following table lists the changes that have been made to the
CVE-2025-54322 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Initial Analysis by [email protected]
Jan. 09, 2026
Action Type Old Value New Value Added CVSS V3.1 AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Added CWE CWE-94 Added CPE Configuration OR *cpe:2.3:o:xspeeder:sxzos:*:*:*:*:*:*:*:* versions up to (including) 2025-12-26 Added Reference Type CISA-ADP: https://pwn.ai/blog/cve-2025-54322-zeroday-unauthenticated-root-rce-affecting-70-000-hosts Types: Exploit, Third Party Advisory Added Reference Type MITRE: https://pwn.ai/blog/cve-2025-54322-zeroday-unauthenticated-root-rce-affecting-70-000-hosts Types: Exploit, Third Party Advisory Added Reference Type MITRE: https://www.xspeeder.com Types: Product -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Dec. 29, 2025
Action Type Old Value New Value Added Reference https://pwn.ai/blog/cve-2025-54322-zeroday-unauthenticated-root-rce-affecting-70-000-hosts -
New CVE Received by [email protected]
Dec. 27, 2025
Action Type Old Value New Value Added Description Xspeeder SXZOS through 2025-12-26 allows root remote code execution via base64-encoded Python code in the chkid parameter to vLogin.py. The title and oIP parameters are also used. Added CVSS V3.1 AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H Added CWE CWE-95 Added Reference https://pwn.ai/blog/cve-2025-54322-zeroday-unauthenticated-root-rce-affecting-70-000-hosts Added Reference https://www.xspeeder.com


