CVE-2025-6965
Integer Truncation on SQLite
Description
There exists a vulnerability in SQLite versions before 3.50.2 where the number of aggregate terms could exceed the number of columns available. This could lead to a memory corruption issue. We recommend upgrading to version 3.50.2 or above.
INFO
Published Date :
July 15, 2025, 2:15 p.m.
Last Modified :
Nov. 4, 2025, 10:16 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] | ||||
| CVSS 4.0 | HIGH | [email protected] |
Solution
- Upgrade SQLite to version 3.50.2 or later.
- Ensure aggregate terms do not exceed available columns.
Public PoC/Exploit Available at Github
CVE-2025-6965 has a 14 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2025-6965.
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2025-6965 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2025-6965
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
None
Python
None
PowerShell Shell
None
PowerShell
None
Dockerfile Python HCL
iOS 26 bypass process using the available libimobiledevice tools and CVE exploitation techniques discussed.
None
PowerShell
Standalone Container Security Tests
Guidelines for Building and Using SQLite3 Multiple Ciphers DLLs in UWP Applications
None
Shell
None
Dockerfile Python Smarty HTML
SQLite Memory Corruption Exploit
None
HTML TypeScript CSS JavaScript
None
DevSecOps Project. Live Deployed app on k8s using ArgoCD ;; https://orthosecure.health/ [old domain]
Dockerfile Python CSS JavaScript HTML Shell
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2025-6965 vulnerability anywhere in the article.

-
BleepingComputer
Microsoft updates Windows DLL that triggered security alerts
Microsoft has resolved a known issue that was causing security applications to incorrectly flag a core Windows component, the company said in a service alert posted this week. The list of affected sys ... Read more
-
Daily CyberSecurity
The Sleeper in Your Browser: How DarkSpectre Turned 8.8 Million Extensions into State-Aligned Spies
In a revelation that exposes a gaping hole in the browser extension ecosystem, Koi Security has unmasked a massive, state-aligned cyber-espionage operation that has been quietly gathering intelligence ... Read more

-
Daily CyberSecurity
Exim’s Poisoned Record: How a Failed Patch and SQL Injection Lead to Critical Heap Overflows
A new security advisory has revealed significant cracks in the armor of Exim, one of the world’s most popular mail transfer agents. Andrew Fasano, the Cyber Lead at the National Institute of Standards ... Read more

-
The Hacker News
Google’s AI ‘Big Sleep’ Finds 5 New Vulnerabilities in Apple’s Safari WebKit
Nov 04, 2025Ravie LakshmananArtificial Intelligence / Vulnerability Google's artificial intelligence (AI)-powered cybersecurity agent called Big Sleep has been credited by Apple for discovering as m ... Read more

-
seclists.org
APPLE-SA-09-15-2025-10 visionOS 26
Full Disclosure mailing list archives From: Apple Product Security via Fulldisclosure <fulldisclosure () seclists org> Date: Mon, 15 Sep 2025 16:37:23 -0700 -----BEGIN PGP SIGNED MESSAGE----- Hash: SH ... Read more

-
seclists.org
APPLE-SA-09-15-2025-9 watchOS 26
Full Disclosure mailing list archives From: Apple Product Security via Fulldisclosure <fulldisclosure () seclists org> Date: Mon, 15 Sep 2025 16:36:59 -0700 -----BEGIN PGP SIGNED MESSAGE----- Hash: SH ... Read more

-
seclists.org
APPLE-SA-09-15-2025-8 tvOS 26
Full Disclosure mailing list archives From: Apple Product Security via Fulldisclosure <fulldisclosure () seclists org> Date: Mon, 15 Sep 2025 16:36:37 -0700 -----BEGIN PGP SIGNED MESSAGE----- Hash: SH ... Read more

-
seclists.org
APPLE-SA-09-15-2025-5 macOS Tahoe 26
Full Disclosure mailing list archives From: Apple Product Security via Fulldisclosure <fulldisclosure () seclists org> Date: Mon, 15 Sep 2025 16:34:18 -0700 -----BEGIN PGP SIGNED MESSAGE----- Hash: SH ... Read more

-
seclists.org
APPLE-SA-09-15-2025-1 iOS 26 and iPadOS 26
Full Disclosure mailing list archives From: Apple Product Security via Fulldisclosure <fulldisclosure () seclists org> Date: Mon, 15 Sep 2025 16:31:32 -0700 -----BEGIN PGP SIGNED MESSAGE----- Hash: SH ... Read more

-
Daily CyberSecurity
Apple Watch Series 11: A New Era of Health and Connectivity
Apple has officially unveiled the Apple Watch Series 11, now equipped with a more scratch-resistant display glass, 5G connectivity, and an optical-based hypertension detection feature. Alongside it, t ... Read more
-
Daily CyberSecurity
Google Chrome Patches Critical ANGLE Vulnerability (CVE-2025-9478) Discovered by AI Agent Big Sleep
Google has released a critical security update for the Stable channel of Chrome, addressing a use-after-free vulnerability in ANGLE, the graphics engine that underpins WebGL and other rendering tasks. ... Read more

-
Daily CyberSecurity
URGENT: NetScaler Zero-Day CVE-2025-7775 Under Active Attack
The Cloud Software Group (CSG) has released urgent security updates to address three high-severity vulnerabilities affecting NetScaler ADC and NetScaler Gateway appliances. The flaws, tracked as CVE-2 ... Read more

-
Daily CyberSecurity
PoC Code Available for Critical SQLite Vulnerability (CVE-2025-6965)
Privacy & Transparencysecurityonline.info and our partners ask for your consent to use your personal data, and to store and/or access information on your device. This includes using your personal data ... Read more
-
Daily CyberSecurity
A New Bridge Between Worlds? Google’s Quick Share May Be Coming to iPhone
At the end of 2024, reports surfaced suggesting that Google was working on a Quick Share feature for iOS and macOS, designed to let users seamlessly transfer files from Android devices to Apple platfo ... Read more
-
Daily CyberSecurity
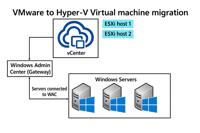
Microsoft Unveils a New Tool to Help Businesses Ditch VMware for Hyper-V
For reasons of compliance and data governance, many large enterprises prefer to purchase servers for on-premises deployment, then rely on virtualization technology to create multiple virtual machines ... Read more

-
Daily CyberSecurity
A New Home for Gemini: Google Unveils Next-Gen Smart Home Devices
At the recent Made by Google event in New York, Google unveiled the Pixel 10 series, Pixel Watch 4, and Pixel Buds 2a. Keen-eyed attendees, however, also noticed what appeared to be a new smart speake ... Read more

-
Daily CyberSecurity
A Glassy Future: Apple to Launch Foldable iPhone, Eyeing a Radical 2027 Redesign
Rumors have long circulated that Apple plans to launch its first foldable iPhone in 2026, and according to information obtained by Bloomberg, the company intends to reintroduce the Touch ID fingerprin ... Read more

-
CybersecurityNews
Weekly Cybersecurity Newsletter: Chrome 0-Day, VMware Flaws Patched, Fortiweb Hack, Teams Abuse, and More
It’s been a busy seven days for security alerts. Google is addressing another actively exploited zero-day in Chrome, and VMware has rolled out key patches for its own set of vulnerabilities. We’ll als ... Read more

-
Daily CyberSecurity
Google’s Big Sleep AI Foils Live Zero-Day Exploit in SQLite (CVE-2025-6965)
In a demonstration of artificial intelligence applied to cybersecurity, Google has revealed that its AI agent, Big Sleep, has successfully identified and neutralized a critical vulnerability before it ... Read more

-
CybersecurityNews
Google’s AI Tool Big Sleep Uncovered Critical SQLite 0-Day Vulnerability and Blocks Active Exploitation
Google’s revolutionary AI-powered security tool, Big Sleep, has achieved a groundbreaking milestone by discovering and preventing the exploitation of a critical SQLite 0-day vulnerability, marking the ... Read more
The following table lists the changes that have been made to the
CVE-2025-6965 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Nov. 04, 2025
Action Type Old Value New Value Added Reference http://www.openwall.com/lists/oss-security/2025/09/06/1 -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Nov. 03, 2025
Action Type Old Value New Value Added Reference http://seclists.org/fulldisclosure/2025/Sep/49 Added Reference http://seclists.org/fulldisclosure/2025/Sep/53 Added Reference http://seclists.org/fulldisclosure/2025/Sep/56 Added Reference http://seclists.org/fulldisclosure/2025/Sep/57 Added Reference http://seclists.org/fulldisclosure/2025/Sep/58 -
Initial Analysis by [email protected]
Jul. 22, 2025
Action Type Old Value New Value Added CVSS V3.1 AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Added CPE Configuration OR *cpe:2.3:a:sqlite:sqlite:*:*:*:*:*:*:*:* versions up to (excluding) 3.50.2 Added Reference Type Google Inc.: https://www.sqlite.org/src/info/5508b56fd24016c13981ec280ecdd833007c9d8dd595edb295b984c2b487b5c8 Types: Patch -
New CVE Received by [email protected]
Jul. 15, 2025
Action Type Old Value New Value Added Description There exists a vulnerability in SQLite versions before 3.50.2 where the number of aggregate terms could exceed the number of columns available. This could lead to a memory corruption issue. We recommend upgrading to version 3.50.2 or above. Added CVSS V4.0 AV:N/AC:H/AT:P/PR:L/UI:N/VC:L/VI:H/VA:L/SC:L/SI:H/SA:L/E:X/CR:X/IR:X/AR:X/MAV:X/MAC:X/MAT:X/MPR:X/MUI:X/MVC:X/MVI:X/MVA:X/MSC:X/MSI:X/MSA:X/S:N/AU:N/R:U/V:D/RE:L/U:Green Added CWE CWE-197 Added Reference https://www.sqlite.org/src/info/5508b56fd24016c13981ec280ecdd833007c9d8dd595edb295b984c2b487b5c8


