CVEFeed Newsroom – Latest Cybersecurity Updates
The "Cyber Newsroom Feed" module is a live feed of the latest cyber news enriched with CVE and vulnerability data. The feed is updated every 5 minutes and includes the latest news from the cyber security industry. The feed is designed to provide users with a comprehensive overview of the latest cyber security news and trends.

-
BleepingComputer
Over 29,000 Exchange servers unpatched against high-severity flaw
Over 29,000 Exchange servers exposed online remain unpatched against a high-severity vulnerability that can let attackers move laterally in Microsoft cloud environments, potentially leading to complet ...

-
CybersecurityNews
Xerox FreeFlow Vulnerabilities leads to SSRF and RCE Attacks
An urgent security update has been released for Xerox FreeFlow Core software, addressing two critical vulnerabilities that could allow attackers to execute remote code and perform server-side request ...

-
Daily CyberSecurity
Microsoft Edge Gets Three More Years of Security Updates on Windows 10
With Windows 10’s lifecycle nearing its end and Microsoft already rolling out the Extended Security Updates (ESU) program for both home and enterprise users—enterprise coverage lasting until October 2 ...

-
Daily CyberSecurity
Apple Is Reportedly Launching a $599 MacBook to Take On Chromebooks
Reports have long suggested that Apple is planning to reintroduce a more affordable MacBook, rumored to feature the A18 Pro processor. According to sources cited by the DigiTimes, components for this ...

-
Daily CyberSecurity
The New Price of AI Chips for China: NVIDIA and AMD Will Give 15% of Revenue to U.S. Governmen
Reuters reports that NVIDIA and AMD have both reached agreements with the U.S. government allowing them to export certain artificial intelligence chips to the Chinese market—on the condition that 15% ...

-
Daily CyberSecurity
Linus Torvalds Slams Google Engineer’s Code as ‘Garbage’ and Rejects It for Linux 6.17
Recently, Palmer Dabbelt of Google’s Android team came under sharp criticism from Linus Torvalds for submitting code to the Linux kernel. The submission concerned RISC-V patches for Linux Kernel 6.17, ...
-
Daily CyberSecurity
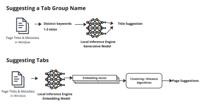
Firefox’s New AI Feature Is Causing Major CPU Spikes and Draining Batteries
Image: Mozilla In its recent v141.0 release, Firefox introduced support for managing tab groups through a built-in artificial intelligence model. For example, when a user creates a new tab group, the ...

-
CybersecurityNews
WinRAR 0-Day in Phishing Attacks to Deploy RomCom Malware
A critical zero-day vulnerability has been identified in WinRAR that cybercriminals are actively exploiting through sophisticated phishing campaigns to distribute RomCom malware. The flaw, designated ...

-
The Cyber Express
BadCam Attack Turns Trusted Linux Webcams into Stealthy USB Weapons
A new class of USB-based attacks has come to light. These attacks are not just targeting removable devices, but existing, trusted peripherals already connected to systems: Linux webcams. Attackers can ...

-
The Hacker News
WinRAR Zero-Day Under Active Exploitation – Update to Latest Version Immediately
The maintainers of the WinRAR file archiving utility have released an update to address an actively exploited zero-day vulnerability. Tracked as CVE-2025-8088 (CVSS score: 8.8), the issue has been des ...


