CVEFeed Newsroom – Latest Cybersecurity Updates
The "Cyber Newsroom Feed" module is a live feed of the latest cyber news enriched with CVE and vulnerability data. The feed is updated every 5 minutes and includes the latest news from the cyber security industry. The feed is designed to provide users with a comprehensive overview of the latest cyber security news and trends.

-
TheCyberThrone
EchoLeak Vulnerability in Microsoft 365 Copilot
Skip to contentOverviewEchoLeak is a critical zero-click vulnerability found in Microsoft 365 Copilot, revealed in 2025 by AIM Security. The flaw allowed attackers to steal sensitive enterprise data w ...

-
Daily CyberSecurity
Next.js Flaw (CVE-2025-49826, CVSS 7.5): Cache Poisoning Leads to Denial-of-Service
A cache poisoning vulnerability (CVE-2025-49826) with a CVSS score of 7.5 has been disclosed in Next.js, the popular React-based web development framework. The flaw, found in versions >=15.1.0 <15.1.8 ...

-
Daily CyberSecurity
Microsoft Edge Alert: Two High-Severity Flaws (CVE-2025-6554, CVE-2025-49713) Allow Remote Code Execution, One Actively Exploited
Microsoft has released Edge Stable Channel Version 138.0.3351.65, an update that addresses critical browser vulnerabilities impacting Chromium-based Microsoft Edge. The patch includes fixes for two hi ...

-
Daily CyberSecurity
PHP Flaws: CVE-2025-1735 (SQLi/Crash) & CVE-2025-6491 (SOAP DoS) Threaten PHP Apps
🔐 Access to This Vulnerability Report Requires Support This article is available to verified supporters only - contribute to read the full report Contribute with Google Or choose another support optio ...

-
Daily CyberSecurity
Apache Under Attack: Critical RCE Flaws in Tomcat & Camel Spark Thousands of Exploit Attempts
In a recent deep-dive analysis, Palo Alto Networks’ Unit 42 revealed disturbing insights into a surge of cyberattacks targeting critical vulnerabilities in Apache Tomcat and Apache Camel. These flaws, ...
-
Daily CyberSecurity
Critical HIKVISION applyCT Flaw (CVE-2025-34067, CVSS 10.0): Unauthenticated RCE Via Fastjson
Image: PeiQi0 A newly disclosed vulnerability in HIKVISION’s widely deployed security management platform, applyCT (previously known as HikCentral), has put countless surveillance and monitoring infra ...
-
Daily CyberSecurity
Anthropic MCP Server Flaws: Path Traversal & Symlink Attacks Allow RCE
Image: Cymulate Cymulate Research Labs has revealed Anthropic’s Filesystem MCP Server vulnerabilities. Two newly disclosed flaws—CVE-2025-53110 and CVE-2025-53109—exposes systems to unauthorized acces ...
-
Daily CyberSecurity
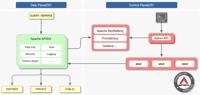
Apache APISIX Flaw (CVE-2025-46647): Token Issuer Bypass in OpenID Connect Allows Cross-Issuer Access
Apache APISIX, a high-performance and AI-ready API gateway trusted for managing traffic across microservices and LLM-based applications, has been found vulnerable to a token issuer validation flaw in ...

-
Daily CyberSecurity
Exposed JDWP Debug Ports Under Attack: Cryptominers Infiltrating Java Apps in Hours
The Wiz Research Team has uncovered a stealthy and rapidly executed exploitation chain leveraging a misconfigured Java Debug Wire Protocol (JDWP) interface to deploy crypto-mining malware in TeamCity ...

-
Daily CyberSecurity
Critical Lucee Flaw (CVE-2025-34074, CVSS 9.4): Authenticated RCE Via Scheduled Task Abuse, Metasploit Module Out
A critical security flaw has been discovered in Lucee, the high-performance, open-source CFML (ColdFusion Markup Language) application server. Tracked as CVE-2025-34074 and carrying a CVSS score of 9. ...


