CVEFeed Newsroom – Latest Cybersecurity Updates
The "Cyber Newsroom Feed" module is a live feed of the latest cyber news enriched with CVE and vulnerability data. The feed is updated every 5 minutes and includes the latest news from the cyber security industry. The feed is designed to provide users with a comprehensive overview of the latest cyber security news and trends.
-
Daily CyberSecurity
Roundcube Alert: High-Severity SVG XSS and CSS Sanitizer Flaws Threaten Webmail Privacy
The maintainers of Roundcube Webmail, one of the world’s most widely used open-source email solutions, have issued security updates for their 1.6 and 1.5 LTS branches. The patches address two high-sev ...

-
Daily CyberSecurity
Early-Boot Attack: UEFI Flaw in ASRock, ASUS, & MSI Boards Lets Hackers Bypass OS Security via PCIe
A fundamental breakdown in how modern computers secure themselves during the boot process has been exposed, leaving systems vulnerable to physical attacks that can bypass operating system defenses ent ...
-
Daily CyberSecurity
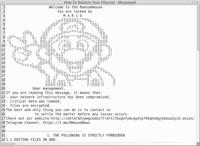
Mario’s Deadly Upgrade: RansomHouse Unveils Dual-Key Encryption to Defeat Backups and Recovery
Ransom Note | Image: Unit 42 Jolly Scorpius, the cybercriminal group behind the notorious RansomHouse operation, has rolled out a major overhaul of its encryption engine, ditching its previously simpl ...

-
AttackIQ
React2Shell (CVE-2025-55182): Critical Remote Code Execution (RCE) in React Server Components
Vulnerability Overview React2Shell (CVE-2025-55182) is a critical (CVSS 10.0) pre-authentication Remote Code Execution (RCE) vulnerability affecting the react-server package used by React Server Compo ...

-
BleepingComputer
Clop ransomware targets Gladinet CentreStack in data theft attacks
The Clop ransomware gang (also known as Cl0p) is targeting Internet-exposed Gladinet CentreStack file servers in a new data theft extortion campaign. Gladinet CentreStack enables businesses to securel ...

-
BleepingComputer
New password spraying attacks target Cisco, PAN VPN gateways
An automated campaign is targeting multiple VPN platforms, with credential-based attacks being observed on Palo Alto Networks GlobalProtect and Cisco SSL VPN. On December 11, threat monitoring platfor ...

-
TheCyberThrone
Cisco Hits Perfect 10 with Secure Email Gateway Bug
Cisco’s CVE-2025-20393 is a CVSS 10.0 zero-day in Cisco AsyncOS that gives unauthenticated attackers full root control over Cisco Secure Email Gateway and Secure Email and Web Manager when the Spam Qu ...

-
The Hacker News
HPE OneView Flaw Rated CVSS 10.0 Allows Unauthenticated Remote Code Execution
Dec 18, 2025Ravie LakshmananVulnerability / Enterprise Security Hewlett Packard Enterprise (HPE) has resolved a maximum-severity security flaw in OneView Software that, if successfully exploited, co ...

-
CybersecurityNews
CISA Adds ASUS Embedded Malicious Code Vulnerability to KEV List Following Active Exploitation
CISA has added a new ASUS vulnerability to its Known Exploited Vulnerabilities (KEV) catalog, signaling urgent risk for affected users and organizations. The flaw, tracked as CVE-2025-59374, affects A ...

-
security.nl
Kritiek beveiligingslek in FreeBSD maakt remote code execution mogelijk
Een kritiek beveiligingslek in FreeBSD maakt remote code execution mogelijk, waarbij een aanvaller in hetzelfde netwerksegment moet zitten als het doelwit. Er zijn beveiligingsupdates uitgebracht om h ...


