CVE-2024-12856
Four-Faith Industrial Router adjust_sys_time OS Command Injection
Description
The Four-Faith router models F3x24 and F3x36 are affected by an operating system (OS) command injection vulnerability. At least firmware version 2.0 allows authenticated and remote attackers to execute arbitrary OS commands over HTTP when modifying the system time via apply.cgi. Additionally, this firmware version has default credentials which, if not changed, would effectively change this vulnerability into an unauthenticated and remote OS command execution issue.
INFO
Published Date :
Dec. 27, 2024, 4:15 p.m.
Last Modified :
Sept. 25, 2025, 7:15 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
Affected Products
The following products are affected by CVE-2024-12856
vulnerability.
Even if cvefeed.io is aware of the exact versions of the
products
that
are
affected, the information is not represented in the table below.
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | HIGH | [email protected] |
Public PoC/Exploit Available at Github
CVE-2024-12856 has a 3 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-12856.
| URL | Resource |
|---|---|
| https://ducklingstudio.blog.fc2.com/blog-entry-392.html | Exploit Third Party Advisory |
| https://vulncheck.com/advisories/four-faith-time | Third Party Advisory |
| https://vulncheck.com/blog/four-faith-cve-2024-12856 | Exploit Third Party Advisory |
| https://vulncheck.com/blog/four-faith-cve-2024-12856 | Exploit Third Party Advisory |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-12856 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-12856
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
An exploit for Four-Faith routers to get a reverse shell
cve poc
Python
A repo for output of an intrusion prediction project
Jupyter Notebook Python Standard ML
The Firmware Security Testing Methodology (FSTM) is composed of nine stages tailored to enable security researchers, software developers, consultants, and Information Security professionals with conducting firmware security assessments.
iot-security-testing iot firmware-analysis penetration-testing-framework iot-testing embedded-security reverse-engineering firmware security security-tools
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-12856 vulnerability anywhere in the article.
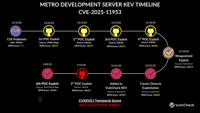
-
Daily CyberSecurity
Silent Intrusion: “Metro4Shell” Exploited in the Wild Since December
Image: VulCheck A new report from VulnCheck reveals that CVE-2025-11953, a critical flaw in the Metro development server dubbed “Metro4Shell,” was being actively weaponized in the wild as early as lat ... Read more

-
The Hacker News
CISA Adds Actively Exploited Sierra Wireless Router Flaw Enabling RCE Attacks
Dec 13, 2025Ravie LakshmananNetwork Security / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added a high-severity flaw impacting Sierra Wireless AirLink A ... Read more

-
CybersecurityNews
RondoDox Botnet Exploits 50+ Vulnerabilities to Attack Routers, CCTV Systems and Web Servers
Since its emergence in early 2025, RondoDox has rapidly become one of the most pervasive IoT-focused botnets in operation, targeting a wide range of network-connected devices—from consumer routers to ... Read more

-
Daily CyberSecurity
RondoDox Botnet Unleashed: New Malware Uses ‘Exploit Shotgun’ to Target 50+ Router and IoT Flaws
Trend Micro has uncovered a rapidly expanding botnet campaign dubbed RondoDox, which is targeting a wide spectrum of internet-exposed devices — from routers and DVRs to CCTV systems and industrial net ... Read more

-
The Register
RondoDox botnet fires 'exploit shotgun' at nearly every router and internet-connected home device
A new RondoDox botnet campaign uses an "exploit shotgun" - fire at everything, see what hits - to target 56 vulnerabilities across at least 30 different vendors' routers, DVRs, CCTV systems, web serve ... Read more

-
BleepingComputer
RondoDox botnet targets 56 n-day flaws in worldwide attacks
A new large-scale botnet called RondoDox is targeting 56 vulnerabilities in more than 30 distinct devices, including flaws first disclosed during Pwn2Own hacking competitions. The attacker focuses on ... Read more

-
Trend Micro
RondoDox: From Targeting Pwn2Own Vulnerabilities to Shotgunning Exploits
Cyber Threats Trend™ Research and ZDI Threat Hunters have identified a large-scale RondoDox botnet campaign exploiting over 50 vulnerabilities across more than 30 vendors, including flaws first seen i ... Read more

-
The Hacker News
RondoDox Botnet Exploits Flaws in TBK DVRs and Four-Faith Routers to Launch DDoS Attacks
Cybersecurity researchers are calling attention to a malware campaign that's targeting security flaws in TBK digital video recorders (DVRs) and Four-Faith routers to rope the devices into a new botnet ... Read more
-
Daily CyberSecurity
RondoDox: Sophisticated Botnet Exploits TBK DVRs & Four-Faith Routers for DDoS Attacks
RondoDox downloader shell script | Image: FortiGuard Labs FortiGuard Labs has uncovered a stealthy and highly adaptive botnet dubbed RondoDox, which is actively exploiting two critical vulnerabilities ... Read more

-
Cybersecurity News
“Gayfemboy” Botnet Leveraging 0-Day Exploit in Four-Faith Industrial Routers
XLab has released a report on the Gayfemboy botnet, a rapidly evolving threat leveraging a 0-day vulnerability in Four-Faith industrial routers. This botnet, initially a modest derivative of the infam ... Read more

-
BleepingComputer
New Mirai botnet targets industrial routers with zero-day exploits
A relatively new Mirai-based botnet has been growing in sophistication and is now leveraging zero-day exploits for security flaws in industrial routers and smart home devices. Exploitation of previous ... Read more

-
security.nl
Securitybedrijf meldt actief misbruik van lek in industriële routers Four-Faith
Aanvallers maken actief misbruik van een kwetsbaarheid in industriële routers van fabrikant Four-Faith en het is onduidelijk of er updates beschikbaar zijn om het probleem te verhelpen, zo meldt secur ... Read more

-
Cybersecurity News
IBM’s HashiCorp Acquisition Under Scrutiny: CMA Investigates Competition Concerns
The United Kingdom’s Competition and Markets Authority (CMA) recently announced that it would launch an investigation into IBM’s $6.4 billion acquisition of HashiCorp, a software company specializing ... Read more

-
BleepingComputer
Hackers exploit Four-Faith router flaw to open reverse shells
Threat actors are exploiting a post-authentication remote command injection vulnerability in Four-Faith routers tracked as CVE-2024-12856 to open reverse shells back to the attackers. The malicious ac ... Read more

-
The Hacker News
⚡ THN Weekly Recap: Top Cybersecurity Threats, Tools and Tips
Cybersecurity / Hacking News Every week, the digital world faces new challenges and changes. Hackers are always finding new ways to breach systems, while defenders work hard to keep our data safe. Whe ... Read more

-
Hackread - Latest Cybersecurity, Tech, Crypto & Hacking News
Critical Flaw Exposes Four-Faith Routers to Remote Exploitation
SUMMARY: Vulnerability: CVE-2024-12856 impacts Four-Faith routers (models F3x24 and F3x36), allowing remote code execution. Exploit Path: Attackers use the /apply.cgi endpoint to exploit the adj_time_ ... Read more

-
Cybersecurity News
Four-Faith Industrial Routers Under Attack: CVE-2024-12856 Exploited in the Wild
VulnCheck, a renowned cybersecurity research organization, has recently issued a warning concerning active exploitation of a critical vulnerability affecting Four-Faith industrial routers. The vulnera ... Read more

-
The Hacker News
15,000+ Four-Faith Routers Exposed to New Exploit Due to Default Credentials
Vulnerability / Threat Intelligence A high-severity flaw impacting select Four-Faith routers has come under active exploitation in the wild, according to new findings from VulnCheck. The vulnerability ... Read more
The following table lists the changes that have been made to the
CVE-2024-12856 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
CVE Modified by [email protected]
Sep. 25, 2025
Action Type Old Value New Value Added CWE CWE-1392 -
Initial Analysis by [email protected]
Sep. 19, 2025
Action Type Old Value New Value Added CPE Configuration AND OR *cpe:2.3:o:four-faith:f3x36_firmware:2.0:*:*:*:*:*:*:* OR cpe:2.3:h:four-faith:f3x36:-:*:*:*:*:*:*:* Added CPE Configuration AND OR *cpe:2.3:o:four-faith:f3x24_firmware:2.0:*:*:*:*:*:*:* OR cpe:2.3:h:four-faith:f3x24:-:*:*:*:*:*:*:* Added Reference Type VulnCheck: https://ducklingstudio.blog.fc2.com/blog-entry-392.html Types: Exploit, Third Party Advisory Added Reference Type VulnCheck: https://vulncheck.com/advisories/four-faith-time Types: Third Party Advisory Added Reference Type CISA-ADP: https://vulncheck.com/blog/four-faith-cve-2024-12856 Types: Exploit, Third Party Advisory Added Reference Type VulnCheck: https://vulncheck.com/blog/four-faith-cve-2024-12856 Types: Exploit, Third Party Advisory -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Dec. 27, 2024
Action Type Old Value New Value Added Reference https://vulncheck.com/blog/four-faith-cve-2024-12856 -
New CVE Received by [email protected]
Dec. 27, 2024
Action Type Old Value New Value Added Description The Four-Faith router models F3x24 and F3x36 are affected by an operating system (OS) command injection vulnerability. At least firmware version 2.0 allows authenticated and remote attackers to execute arbitrary OS commands over HTTP when modifying the system time via apply.cgi. Additionally, this firmware version has default credentials which, if not changed, would effectively change this vulnerability into an unauthenticated and remote OS command execution issue. Added CVSS V3.1 AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H Added CWE CWE-78 Added Reference https://ducklingstudio.blog.fc2.com/blog-entry-392.html Added Reference https://vulncheck.com/advisories/four-faith-time Added Reference https://vulncheck.com/blog/four-faith-cve-2024-12856


