CVEFeed Newsroom – Latest Cybersecurity Updates
The "Cyber Newsroom Feed" module is a live feed of the latest cyber news enriched with CVE and vulnerability data. The feed is updated every 5 minutes and includes the latest news from the cyber security industry. The feed is designed to provide users with a comprehensive overview of the latest cyber security news and trends.

-
Cybersecurity News
From Charging to Hijacking: The Autel MaxiCharger Vulnerability
Image: Sector 7The transition to electric vehicles (EVs) is rapidly gaining momentum, but the recent Pwn2Own Automotive 2024 competition in Tokyo has revealed a concerning vulnerability: EV chargers t ...

-
Cybersecurity News
CVE-2024-45032 (CVSS 10): Siemens Issues Critical Security Patch for Industrial Edge Management
Siemens has released a critical security advisory for its Industrial Edge Management platform, warning of an Authorization Bypass vulnerability that could have serious implications for industrial netw ...

-
Cybersecurity News
CVE-2024-45411: Twig Sandbox Bypass Vulnerability Puts PHP Applications at Risk
A critical security vulnerability has been discovered in Twig, a widely used PHP template engine, potentially allowing attackers to bypass sandbox restrictions and execute malicious code. The vulnerab ...

-
Cybersecurity News
CVE-2024-6596 (CVSS 9.8): Critical Code Injection Flaw Found in Endress+Hauser Products
CERT@VDE coordinated with Endress+Hauser, a well-known leader in industrial automation and instrumentation, has issued a security advisory for a critical vulnerability (CVE-2024-6596) affecting severa ...

-
Cybersecurity News
Microsoft’s September Patch Tuesday: A Patchwork of Urgency with 4 Zero-Days Under Attack
This September’s edition of Microsoft’s Patch Tuesday addresses 79 vulnerabilities, including 6 critical and 71 important severity issues. Among these, four zero-day vulnerabilities were actively expl ...

-
Cybersecurity News
CVE-2024-42500 (CVSS 9.3): Critical HPE HP-UX Vulnerability Demands Immediate Action
A critical vulnerability has been discovered in HPE HP-UX’s Network File System (NFSv4), leaving systems open to potential denial-of-service (DoS) attacks. This vulnerability, tracked as CVE-2024-4250 ...
-
Cybersecurity News
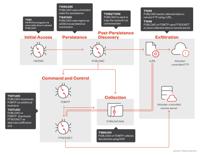
Earth Preta’s Cyber Arsenal Expands: New Malware and Strategies Target APAC Governments
A new report from Trend Micro has revealed that Earth Preta, the notorious cyber espionage group, has significantly evolved its tactics and malware arsenal, posing a heightened threat to government en ...

-
TheCyberThrone
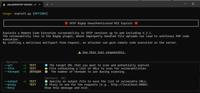
CISA KEV Catalog Update Part III-September 2024
The US CISA has added below vulnerabilities to the Known exploited vulnerabilities catalog based on the evidence of active exploitation. These vulnerabilities are part of this month microsoft patch tu ...
-
Cybersecurity News
CVE-2024-8517: Critical SPIP Flaw Leaves Websites Vulnerable to Remote Attacks, PoC Published
The popular open-source content management system (CMS), SPIP, is facing a critical security vulnerability that could allow unauthenticated attackers to execute malicious code on affected servers. The ...

-
TheCyberThrone
Microsoft Patch Tuesday – September 2024
Microsoft patched 79 CVEs in its September 2024 Patch Tuesday release, with seven rated critical, 71 rated as important, and one rated as moderate. This includes patches for 4 Zeroday vulnerabilities. ...


