CVE-2025-32432
Craft CMS Allows Remote Code Execution
Description
Craft is a flexible, user-friendly CMS for creating custom digital experiences on the web and beyond. Starting from version 3.0.0-RC1 to before 3.9.15, 4.0.0-RC1 to before 4.14.15, and 5.0.0-RC1 to before 5.6.17, Craft is vulnerable to remote code execution. This is a high-impact, low-complexity attack vector. This issue has been patched in versions 3.9.15, 4.14.15, and 5.6.17, and is an additional fix for CVE-2023-41892.
INFO
Published Date :
April 25, 2025, 3:15 p.m.
Last Modified :
April 28, 2025, 8:57 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] | ||||
| CVSS 3.1 | CRITICAL | [email protected] |
Solution
- Upgrade Craft CMS to version 3.9.15 or later.
- Upgrade Craft CMS to version 4.14.15 or later.
- Upgrade Craft CMS to version 5.6.17 or later.
Public PoC/Exploit Available at Github
CVE-2025-32432 has a 20 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2025-32432.
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2025-32432 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2025-32432
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
Mirror of https://github.com/nomi-sec/PoC-in-GitHub
None
Python Shell Makefile C
Acunetix v25.5.250613157 - 17 Jun 2025
AI修复生成的CVE-2025-32432的poc
Python
CVE-2025-32432
Python
None
Python
PoCs
Python JavaScript EJS
监控Github最新网络安全相关的仓库...
cve cybersecurity github spider
Shell Python Nix
CVE-2025-32432 checker and exploit
Go
This repository contains a proof-of-concept exploit script for CVE-2025-32432, a pre-authentication Remote Code Execution (RCE) vulnerability affecting CraftCMS versions 4.x and 5.x. The vulnerability exists in the asset transform generation feature of CraftCMS.
Python
CraftCMS RCE Checker (CVE-2025-32432)
Go
Provides security patches for out-of-date Craft CMS installs
PHP
None
HTML Python Shell
本项目借鉴了vulhub仓库的模式,用户只需执行一条docker命令即可轻松部署漏洞环境。
这是一个每天同步Vulnerability-Wiki中docs-base中内容的项目
HTML
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2025-32432 vulnerability anywhere in the article.

-
The Hacker News
Experts Reports Sharp Increase in Automated Botnet Attacks Targeting PHP Servers and IoT Devices
Oct 29, 2025Ravie LakshmananVulnerability / Internet of Things Cybersecurity researchers are calling attention to a spike in automated attacks targeting PHP servers, IoT devices, and cloud gateways ... Read more

-
The Cyber Express
22 Vulnerabilities Under Attack – And Another That Could Be
Cyble researchers detailed 22 vulnerabilities under active attack in a blog post today – and nine of them aren’t in CISA’s Known Exploited Vulnerabilities (KEV) catalog. Twelve of the vulnerabilities ... Read more
-
Daily CyberSecurity
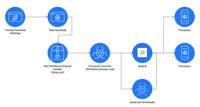
YouTube Downloader Sites Are Now Hiding Proxyware to Hijack Your Bandwidth
Attack Flow | Image: ASEC Cybercriminals are once again exploiting popular online habits—this time leveraging YouTube video download sites as bait for distributing Proxyware malware. AhnLab SEcurity i ... Read more

-
The Hacker News
Threat Actor Mimo Targets Magento and Docker to Deploy Crypto Miners and Proxyware
Jul 23, 2025Ravie LakshmananMalware / Cryptocurrency The threat actor behind the exploitation of vulnerable Craft Content Management System (CMS) instances has shifted its tactics to target Magento ... Read more

-
Daily CyberSecurity
Mimo Strikes Magento: New Campaign Shifts to Cryptojacking, Proxyjacking, & Stealthy Persistence
The once Craft CMS-focused threat actor known as Mimo—or Mimo’lette—has resurfaced with new vigor, broadening its scope and evolving into a persistent adversary. In its latest campaign, detailed by th ... Read more

-
Daily CyberSecurity
Critical Lucee Flaw (CVE-2025-34074, CVSS 9.4): Authenticated RCE Via Scheduled Task Abuse, Metasploit Module Out
A critical security flaw has been discovered in Lucee, the high-performance, open-source CFML (ColdFusion Markup Language) application server. Tracked as CVE-2025-34074 and carrying a CVSS score of 9. ... Read more

-
security.nl
VS meldt actief misbruik van kwetsbaarheden in Craft CMS
Aanvallers maken actief misbruik van twee kwetsbaarheden in Craft CMS, een contentmanagementsysteem voor het opzetten van websites, vergelijkbaar met WordPress. Dat meldt het Cybersecurity and Infrast ... Read more

-
The Hacker News
Hackers Exploit Critical Craft CMS Flaws; Hundreds of Servers Likely Compromised
Web Application Security / Vulnerability Threat actors have been observed exploiting two newly disclosed critical security flaws in Craft CMS in zero-day attacks to breach servers and gain unauthorize ... Read more

-
Daily CyberSecurity
Windows 11 25H2 Update: Minor Changes Expected in October 2025
Microsoft now schedules major version updates for Windows 11 every October, with the upcoming release set for October 2025—namely, Windows 11 version 25H2. References to this version have already begu ... Read more
-
Daily CyberSecurity
Craft CMS Zero-Day CVE-2025-32432 Exploited with Metasploit Module Now Public
Image: Chocapikk_ Security researcher Chocapikk has published a Metasploit module for a critical zero-day vulnerability impacting Craft CMS, tracked as CVE-2025-32432 (CVSS 10). This remote code execu ... Read more

-
Daily CyberSecurity
CISA Warns of Critical Vulnerabilities in Planet Technology Products
CISA has issued a new security advisory highlighting critical vulnerabilities impacting several Planet Technology products, including UNI-NMS-Lite, NMS-500, NMS-1000V, WGS-804HPT-V2, and WGS-4215-8T2S ... Read more

-
security.nl
Grootschalig misbruik van kritieke kwetsbaarheden in Craft CMS gemeld
Aanvallers maken op grote schaal misbruik van kritieke kwetsbaarheden in Craft CMS, zo meldt CERT Orange Cyberdefense. Updates zijn inmiddels beschikbaar, maar websites zijn al voor het uitkomen van d ... Read more

-
Cyber Security News
Critical Craft CMS RCE 0-Day Vulnerability Exploited in Attacks to Steal Data
According to security researchers at CERT Orange Cyberdefense, a critical remote code execution (RCE) vulnerability in Craft CMS is actively being exploited to breach servers and steal data. The vulne ... Read more

-
BleepingComputer
Craft CMS RCE exploit chain used in zero-day attacks to steal data
Two vulnerabilities impacting Craft CMS were chained together in zero-day attacks to breach servers and steal data, with exploitation ongoing, according to CERT Orange Cyberdefense. The vulnerabilitie ... Read more

-
Daily CyberSecurity
CVE-2025-32432 (CVSS 10): Craft CMS Hit by Critical RCE Flaw Exploited in the Wild
Craft CMS, a widely used content management system for developers and agencies, has disclosed a critical vulnerability tracked as CVE-2025-32432, affecting multiple major versions. The vulnerability, ... Read more
The following table lists the changes that have been made to the
CVE-2025-32432 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Initial Analysis by [email protected]
Apr. 28, 2025
Action Type Old Value New Value Added CVSS V3.1 AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H Added CWE NVD-CWE-noinfo Added CPE Configuration OR *cpe:2.3:a:craftcms:craft_cms:*:*:*:*:*:*:*:* versions from (including) 3.0.0 up to (excluding) 3.9.15 *cpe:2.3:a:craftcms:craft_cms:*:*:*:*:*:*:*:* versions from (including) 4.0.0 up to (excluding) 4.14.15 *cpe:2.3:a:craftcms:craft_cms:*:*:*:*:*:*:*:* versions from (including) 5.0.0 up to (excluding) 5.6.17 Added Reference Type GitHub, Inc.: https://github.com/craftcms/cms/blob/3.x/CHANGELOG.md#3915---2025-04-10-critical Types: Broken Link Added Reference Type GitHub, Inc.: https://github.com/craftcms/cms/blob/4.x/CHANGELOG.md#41415---2025-04-10-critical Types: Product Added Reference Type GitHub, Inc.: https://github.com/craftcms/cms/blob/5.x/CHANGELOG.md#5617---2025-04-10-critical Types: Product Added Reference Type GitHub, Inc.: https://github.com/craftcms/cms/commit/e1c85441fa47eeb7c688c2053f25419bc0547b47 Types: Patch Added Reference Type GitHub, Inc.: https://github.com/craftcms/cms/security/advisories/GHSA-f3gw-9ww9-jmc3 Types: Third Party Advisory Added Reference Type CISA-ADP: https://sensepost.com/blog/2025/investigating-an-in-the-wild-campaign-using-rce-in-craftcms/ Types: Exploit, Press/Media Coverage -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Apr. 25, 2025
Action Type Old Value New Value Added Reference https://sensepost.com/blog/2025/investigating-an-in-the-wild-campaign-using-rce-in-craftcms/ -
New CVE Received by [email protected]
Apr. 25, 2025
Action Type Old Value New Value Added Description Craft is a flexible, user-friendly CMS for creating custom digital experiences on the web and beyond. Starting from version 3.0.0-RC1 to before 3.9.15, 4.0.0-RC1 to before 4.14.15, and 5.0.0-RC1 to before 5.6.17, Craft is vulnerable to remote code execution. This is a high-impact, low-complexity attack vector. This issue has been patched in versions 3.9.15, 4.14.15, and 5.6.17, and is an additional fix for CVE-2023-41892. Added CVSS V3.1 AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:L Added CWE CWE-94 Added Reference https://github.com/craftcms/cms/blob/3.x/CHANGELOG.md#3915---2025-04-10-critical Added Reference https://github.com/craftcms/cms/blob/4.x/CHANGELOG.md#41415---2025-04-10-critical Added Reference https://github.com/craftcms/cms/blob/5.x/CHANGELOG.md#5617---2025-04-10-critical Added Reference https://github.com/craftcms/cms/commit/e1c85441fa47eeb7c688c2053f25419bc0547b47 Added Reference https://github.com/craftcms/cms/security/advisories/GHSA-f3gw-9ww9-jmc3