CVE-2025-31324
SAP NetWeaver Unrestricted File Upload Vulnerability - [Actively Exploited]
Description
SAP NetWeaver Visual Composer Metadata Uploader is not protected with a proper authorization, allowing unauthenticated agent to upload potentially malicious executable binaries that could severely harm the host system. This could significantly affect the confidentiality, integrity, and availability of the targeted system.
INFO
Published Date :
April 24, 2025, 5:15 p.m.
Last Modified :
Oct. 31, 2025, 9:56 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
SAP NetWeaver Visual Composer Metadata Uploader contains an unrestricted file upload vulnerability that allows an unauthenticated agent to upload potentially malicious executable binaries.
Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable.
Known Detected Feb 26, 2026
https://me.sap.com/notes/3594142 ; https://nvd.nist.gov/vuln/detail/CVE-2025-31324
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] | ||||
| CVSS 3.1 | CRITICAL | [email protected] |
Solution
- Implement strict authorization checks for metadata uploads.
- Restrict access to the Visual Composer Metadata Uploader.
- Review and enforce file type validation rules.
Public PoC/Exploit Available at Github
CVE-2025-31324 has a 41 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2025-31324.
| URL | Resource |
|---|---|
| https://me.sap.com/notes/3594142 | Permissions Required |
| https://url.sap/sapsecuritypatchday | Vendor Advisory |
| https://onapsis.com/blog/active-exploitation-of-sap-vulnerability-cve-2025-31324/ | Third Party Advisory |
| https://www.bleepingcomputer.com/news/security/sap-fixes-suspected-netweaver-zero-day-exploited-in-attacks/ | Press/Media Coverage |
| https://www.theregister.com/2025/04/25/sap_netweaver_patch/ | Press/Media Coverage |
| https://onapsis.com/blog/active-exploitation-of-sap-vulnerability-cve-2025-31324/ | Third Party Advisory |
| https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-31324 | US Government Resource |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2025-31324 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2025-31324
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
SAP Network Topology Scanner - Discover, fingerprint, and assess SAP systems
Python Batchfile Rich Text Format
Simple burp plugin that checks for known endpoints and misconfigurations in SAP applications.
Java
Mirror of https://github.com/nomi-sec/PoC-in-GitHub
Proof-of-Concept 0day for SAP NetWeaver created by ShinyHunters
Python
Acunetix v25.5.250613157 - 17 Jun 2025
None
HTML
None
Python Shell
sap netweaver 0day poc by shinyhunters (scattered lapsus$ hunters) affecting all 7.x CVE-2025-31324
Python
SAP NetWeaver Visual Composer Metadata Uploader <= 7.50 CVE-2025-31324 PoC
Python
sap-netweaver-cve-2025-31324-check
None
Python Java
Research Purposes only
Java Python
CVE-2025-31324 & CVE-2025-42999 vulnerability and compromise assessment tool
cve-2025-31324 insecure-deserialization sap-netweaver security-tools cve-2025-42999 missing-authorization-check vcframework
Python
A Python-based security scanner for identifying the CVE-2025-31324 vulnerability in SAP Visual Composer systems, and detecting known Indicators of Compromise (IOCs) such as malicious .jsp.
Python
🔍 A simple Bash script to detect malicious JSP webshells, including those used in exploits of SAP NetWeaver CVE-2025-31324.
Shell PowerShell
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2025-31324 vulnerability anywhere in the article.

-
Hackread - Cybersecurity News, Data Breaches, AI and More
Report Finds Just 1% of Security Flaws Drive Most Cyberattacks in 2025
While thousands of security flaws are reported every year, a new investigation has found that the vast majority are never actually used. Instead, a small group of “routinely targeted” flaws are doing ... Read more

-
CybersecurityNews
CISA Expands KEV Catalog with 1,484 New Vulnerabilities as Active Exploitation Surges 20% in 2025
The United States Cybersecurity and Infrastructure Security Agency (CISA) has significantly expanded its Known Exploited Vulnerabilities (KEV) Catalog to 1,484 vulnerabilities as of December 2025, mar ... Read more

-
Red Canary
Red Canary’s best of 2025
A look back at the year’s most popular research, guides, videos, and more. December 17, 20252025 brought some big changes to Red Canary; you might have noticed some more blue in our branding. But even ... Read more

-
The Hacker News
Chinese Hackers Have Started Exploiting the Newly Disclosed React2Shell Vulnerability
Dec 05, 2025Ravie LakshmananVulnerability / Software Security Two hacking groups with ties to China have been observed weaponizing the newly disclosed security flaw in React Server Components (RSC) ... Read more

-
Help Net Security
When IT fails, OT pays the price
State groups, criminal crews, and hybrid operators are all using familiar IT entry points to reach systems that support industrial processes, according to the latest Operational Technology Threat Repo ... Read more

-
Daily CyberSecurity
Trustwave Confirms ‘Trinity of Chaos’ Alliance: Scattered LAPSUS$ Hunters Form EaaS Supergroup
Researchers from Trustwave SpiderLabs’ Cyber Threat Intelligence team have identified the formation of a new federated threat alliance uniting three of the most infamous cybercriminal collectives of r ... Read more

-
BleepingComputer
CISA orders feds to patch VMware Tools flaw exploited by Chinese hackers
On Thursday, CISA warned U.S. government agencies to secure their systems against attacks exploiting a high-severity vulnerability in Broadcom's VMware Aria Operations and VMware Tools software. Track ... Read more

-
Daily CyberSecurity
SAP Patches Critical 10.0 Flaw in NetWeaver: Unauthenticated RCE Risk
SAP has released its October 2025 Security Patch Day, addressing 13 new security notes and 3 updates across multiple enterprise products. The update includes a critical vulnerability (CVE-2025-42944) ... Read more

-
BleepingComputer
Chinese hackers exploiting VMware zero-day since October 2024
Broadcom has patched a high-severity privilege escalation vulnerability in its VMware Aria Operations and VMware Tools software, which has been exploited in zero-day attacks since October 2024. While ... Read more

-
The Cyber Express
22 Vulnerabilities Under Attack – And Another That Could Be
Cyble researchers detailed 22 vulnerabilities under active attack in a blog post today – and nine of them aren’t in CISA’s Known Exploited Vulnerabilities (KEV) catalog. Twelve of the vulnerabilities ... Read more

-
Help Net Security
Microsoft, Adobe, SAP deliver critical fixes for September 2025 Patch Tuesday
On September 2025 Patch Tuesday, Microsoft has released patches for 80+ vulnerabilities in its various software products, but the good news is that none of them are actively exploited. Among the criti ... Read more

-
TheCyberThrone
SAP Patch Tuesday: Key Vulnerabilities in September 2025
September 9, 2025The September 2025 SAP Patch Tuesday brings a critical batch of security updates addressing a diverse portfolio of vulnerabilities across prominent SAP platforms, reinforcing the impo ... Read more

-
Kaspersky
IT threat evolution in Q2 2025. Non-mobile statistics
IT threat evolution in Q2 2025. Non-mobile statistics IT threat evolution in Q2 2025. Mobile statistics The statistics in this report are based on detection verdicts returned by Kaspersky products unl ... Read more

-
Hackread - Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Jaguar Land Rover Cyberattack Disrupts Production and Sales Operations
Jaguar Land Rover is restoring systems after a cyberattack disrupted production and sales, with a hacker group previously linked to the M&S data breach claiming responsibility for the breach. Jaguar L ... Read more
-
DataBreaches.Net
Jaguar Land Rover production impacted by cyberattack; Scattered Spider/ShinyHunters claims responsibility
Chris Vallance and Theo Leggett of the BBC report: A cyber-attack has “severely disrupted” Jaguar Land Rover (JLR) vehicle production, including at its two main UK plants. The company, which is owned ... Read more

-
Daily CyberSecurity
Kaspersky Report: Vulnerabilities Are Exploding, and Attackers Are Adapting
Kaspersky Labs has published its Q2 2025 vulnerability analysis, revealing an alarming rise in both the number of vulnerabilities registered and their exploitation in the wild. The findings show that ... Read more

-
Kaspersky
Exploits and vulnerabilities in Q2 2025
Vulnerability registrations in Q2 2025 proved to be quite dynamic. Vulnerabilities that were published impact the security of nearly every computer subsystem: UEFI, drivers, operating systems, browser ... Read more

-
CybersecurityNews
Weekly Cybersecurity News Recap : Apple 0-day, Chrome, Copilot Vulnerabilities and Cyber Attacks
This past week was packed with high-severity disclosures and active exploitation reports across the global threat landscape. At the forefront, Apple rushed out emergency patches for yet another zero-d ... Read more

-
Help Net Security
Week in review: Covertly connected and insecure Android VPN apps, Apple fixes exploited zero-day
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Android VPN apps used by millions are covertly connected AND insecure Three families of Android VPN ap ... Read more
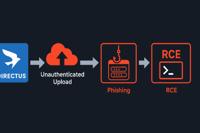
-
Daily CyberSecurity
CVE-2025-55746: Critical Directus Flaw Exposes Servers to Unauthenticated File Upload and RCE
The Directus project has disclosed a critical vulnerability tracked as CVE-2025-55746 (CVSS 9.3) that could allow unauthenticated attackers to upload or modify files on vulnerable servers. Directus, a ... Read more
The following table lists the changes that have been made to the
CVE-2025-31324 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Oct. 31, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-31324 Types: US Government Resource -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-31324 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-31324 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-31324 -
Modified Analysis by [email protected]
May. 06, 2025
Action Type Old Value New Value -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
May. 02, 2025
Action Type Old Value New Value Added Reference https://onapsis.com/blog/active-exploitation-of-sap-vulnerability-cve-2025-31324/ -
Initial Analysis by [email protected]
May. 02, 2025
Action Type Old Value New Value Added CVSS V3.1 AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Added CPE Configuration OR *cpe:2.3:a:sap:netweaver:7.50:*:*:*:*:*:*:* Added Reference Type SAP SE: https://me.sap.com/notes/3594142 Types: Permissions Required Added Reference Type CISA-ADP: https://onapsis.com/blog/active-exploitation-of-sap-vulnerability-cve-2025-31324/ Types: Third Party Advisory Added Reference Type SAP SE: https://url.sap/sapsecuritypatchday Types: Vendor Advisory Added Reference Type CVE: https://www.bleepingcomputer.com/news/security/sap-fixes-suspected-netweaver-zero-day-exploited-in-attacks/ Types: Press/Media Coverage Added Reference Type CVE: https://www.theregister.com/2025/04/25/sap_netweaver_patch/ Types: Press/Media Coverage -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
May. 01, 2025
Action Type Old Value New Value Added Reference https://onapsis.com/blog/active-exploitation-of-sap-vulnerability-cve-2025-31324/ -
CVE CISA KEV Update by 9119a7d8-5eab-497f-8521-727c672e3725
Apr. 30, 2025
Action Type Old Value New Value Added Date Added 2025-04-29 Added Due Date 2025-05-20 Added Required Action Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable. Added Vulnerability Name SAP NetWeaver Unrestricted File Upload Vulnerability -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Apr. 26, 2025
Action Type Old Value New Value Added Reference https://www.bleepingcomputer.com/news/security/sap-fixes-suspected-netweaver-zero-day-exploited-in-attacks/ Added Reference https://www.theregister.com/2025/04/25/sap_netweaver_patch/ -
New CVE Received by [email protected]
Apr. 24, 2025
Action Type Old Value New Value Added Description SAP NetWeaver Visual Composer Metadata Uploader is not protected with a proper authorization, allowing unauthenticated agent to upload potentially malicious executable binaries that could severely harm the host system. This could significantly affect the confidentiality, integrity, and availability of the targeted system. Added CVSS V3.1 AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H Added CWE CWE-434 Added Reference https://me.sap.com/notes/3594142 Added Reference https://url.sap/sapsecuritypatchday