CVE-2024-28000
WordPress LiteSpeed Cache plugin <= 6.3.0.1 - Unauthenticated Privilege Escalation vulnerability
Description
Incorrect Privilege Assignment vulnerability in LiteSpeed Technologies LiteSpeed Cache litespeed-cache allows Privilege Escalation.This issue affects LiteSpeed Cache: from 1.9 through 6.3.0.1.
INFO
Published Date :
Aug. 21, 2024, 2:15 p.m.
Last Modified :
June 17, 2025, 7:15 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] | ||||
| CVSS 3.1 | CRITICAL | [email protected] |
Solution
- Update the 'LiteSpeed Cache' plugin to version 6.4 or later through the administrative dashboard.
Public PoC/Exploit Available at Github
CVE-2024-28000 has a 9 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-28000.
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-28000 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-28000
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
None
HTML Python Shell
WordPress Vulnarable Plugins Scanner
Go
CVE-2024-28000 Exploit for litespeed-cache =<6.3 allows Privilege Escalation with creation of administrator account
Go
CVE-2024-28000 LiteSpeed Cache Privilege Escalation Scan&Exp
Python
PoC for the CVE-2024 Litespeed Cache Privilege Escalation
Python
LiteSpeed Cache Privilege Escalation PoC - CVE-2024-28000
abdal ebrasha exploit poc wordpress cve-2024-28000 litespeed-cache-privilege privilege-escalation-poc
C#
LiteSpeed Cache Privilege Escalation PoC
Python
0Day CVE-2024-28000 Auto Exploiter on WordPress LiteSpeed Cache plugin
0day auto cve exploit hack rce shell wordpress
None
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-28000 vulnerability anywhere in the article.

-
BleepingComputer
ACF plugin bug gives hackers admin on 50,000 WordPress sites
A critical-severity vulnerability in the Advanced Custom Fields: Extended (ACF Extended) plugin for WordPress can be exploited remotely by unauthenticated attackers to obtain administrative permission ... Read more

-
Daily CyberSecurity
LiteSpeed Cache Flaw (CVE-2025-12450): 7 Million WordPress Sites Exposed to XSS Attack
A security flaw has been discovered in the LiteSpeed Cache for WordPress (LSCWP) plugin, one of the most popular optimization tools in the WordPress ecosystem, with over 7 million active installations ... Read more

-
BleepingComputer
LiteSpeed Cache WordPress plugin bug lets hackers get admin access
The free version of the popular WordPress plugin LiteSpeed Cache has fixed a dangerous privilege elevation flaw on its latest release that could allow unauthenticated site visitors to gain admin right ... Read more

-
The Hacker News
LiteSpeed Cache Plugin Vulnerability Poses Significant Risk to WordPress Websites
Vulnerability / Website Security A high-severity security flaw has been disclosed in the LiteSpeed Cache plugin for WordPress that could allow an unauthenticated threat actor to elevate their privileg ... Read more

-
Cybersecurity News
Over 6 Million Sites at Risk: Severe Privilege Escalation Flaw CVE-2024-50550 in LiteSpeed Cache Plugin
Rafie Muhammad, a Security Researcher at Patchstack, reveals a severe security vulnerability in the LiteSpeed Cache plugin—a popular WordPress caching plugin with over six million active installations ... Read more

-
Cybersecurity News
CVE-2024-47374: LiteSpeed Cache Plugin Flaw Threatens Millions of WordPress Sites
A significant security vulnerability has been discovered in the LiteSpeed Cache plugin for WordPress, a widely used tool with over 6 million active installations. The flaw is an unauthenticated stored ... Read more

-
Cybersecurity News
Versa Networks Exposes Critical API Vulnerability in Versa Director (CVE-2024-45229)
Versa Networks has issued a security advisory regarding a vulnerability discovered in its Versa Director product, CVE-2024-45229. This vulnerability, which carries a CVSS score of 6.6, could potential ... Read more
-
Cybersecurity News
Sophisticated Cyber Espionage: Earth Baxia Uses CVE-2024-36401 and Cobalt Strike to Infiltrate APAC
Overview of the attack chain | Image: Trend MicroIn a recent report from Trend Micro, the cyber espionage group Earth Baxia has been identified targeting government organizations in Taiwan and potenti ... Read more
-
Cybersecurity News
Ajina.Banker: Unmasking the Android Malware Targeting Central Asian Banks
Screenshot of the sample found on the VirusTotal platformCybersecurity analysts at Group-IB have uncovered a sophisticated malware campaign targeting bank customers in Central Asia. Dubbed “Ajina.Bank ... Read more
-
Cybersecurity News
BadIIS Malware : 35+ IIS Servers Compromised in DragonRank Campaign
A recent report from Cisco Talos has exposed a new threat actor named DragonRank, a Chinese-speaking group specializing in SEO manipulation and cyberattacks. This group operates by exploiting vulnerab ... Read more

-
The Hacker News
Critical Security Flaw Found in LiteSpeed Cache Plugin for WordPress
WordPress / Webinar Security Cybersecurity researchers have discovered yet another critical security flaw in the LiteSpeed Cache plugin for WordPress that could allow unauthenticated users to take con ... Read more

-
Cybersecurity News
Black Basta’s Evolving Tactics and the Rising Role of LLMs in Cyber Attack
On the latest episode of the Microsoft Threat Intelligence podcast, host Sherrod DeGrippo and her expert guests delved into the cutting-edge techniques employed by cybercriminal groups, with a particu ... Read more

-
BleepingComputer
LiteSpeed Cache bug exposes 6 million WordPress sites to takeover attacks
Yet, another critical severity vulnerability has been discovered in LiteSpeed Cache, a caching plugin for speeding up user browsing in over 6 million WordPress sites. The flaw, tracked as CVE-2024-440 ... Read more

-
Cybersecurity News
CVE-2024-44000 (CVSS 9.8): Litespeed Cache flaw exposes millions of WordPress sites to takeover attacks
A significant security vulnerability has been uncovered in the popular LiteSpeed Cache plugin for WordPress, which boasts over 5 million active installations. The vulnerability, discovered by Rafie Mu ... Read more

-
Cybersecurity News
North Korea Targets DeFi and Crypto Companies with Advanced Social Engineering Attacks
Please enable JavaScriptThe FBI has warned sternly about North Korean state-sponsored hackers employing highly sophisticated social engineering tactics to infiltrate decentralized finance (DeFi) and c ... Read more

-
Cybersecurity News
CVE-2024-38106: 0-Day Windows Kernel Vulnerability Exploited in the Wild, PoC Published
Recently, security researcher Sergey Kornienko from PixiePoint Security published an analysis and proof-of-concept (PoC) exploit for a critical zero-day vulnerability in the Windows Kernel, identified ... Read more

-
Cybersecurity News
Researcher Identifies ToddyCat-Inspired APT Attack Leveraging ICMP Backdoor and Microsoft Exchange Flaws
Image: KasperskyCybersecurity researchers at Kaspersky’s Global Emergency Response Team (GERT) have uncovered a sophisticated attack involving an ICMP backdoor, bearing striking similarities to the ta ... Read more

-
Cybersecurity News
Google TAG Uncovers Watering Hole Attacks on Mongolian Government Websites
In a revealing report, Google’s Threat Analysis Group (TAG) has uncovered a series of sophisticated watering hole attacks targeting Mongolian government websites between November 2023 and July 2024. T ... Read more
-
Cybersecurity News
ESET Uncovers Zero-Day Vulnerabilities in WPS Office, Exploited by APT-C-60
Overview of the exploit’s control flow | Image: ESETESET researchers have identified two severe vulnerabilities in WPS Office for Windows, widely exploited by the APT-C-60 cyberespionage group, which ... Read more
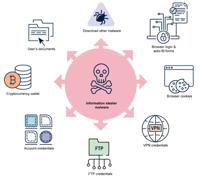
-
Cybersecurity News
Critical Flaw Discovered in Popular Python Library Pandas
Information Stealer Malware on the Rise: ACSC Issues Urgent Cybersecurity WarningThe Australian Cyber Security Centre (ACSC) has issued a warning about the escalating threat of information stealer mal ... Read more
The following table lists the changes that have been made to the
CVE-2024-28000 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Jun. 17, 2025
Action Type Old Value New Value Added Reference https://packetstorm.news/files/id/200819/ Added Reference https://thehackernews.com/2024/08/critical-flaw-in-wordpress-litespeed.html?m=1 Added Reference https://www.exploit-db.com/exploits/52328 -
Initial Analysis by [email protected]
Mar. 07, 2025
Action Type Old Value New Value Added CVSS V3.1 AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Added CWE NVD-CWE-Other Added CPE Configuration OR *cpe:2.3:a:litespeedtech:litespeed_cache:*:*:*:*:*:wordpress:*:* versions from (including) 1.9 from (excluding) 6.4 Added Reference Type Patchstack: https://patchstack.com/articles/critical-privilege-escalation-in-litespeed-cache-plugin-affecting-5-million-sites?_s_id=cve Types: Exploit Added Reference Type Patchstack: https://patchstack.com/database/vulnerability/litespeed-cache/wordpress-litespeed-cache-plugin-6-3-0-1-unauthenticated-privilege-escalation-vulnerability?_s_id=cve Types: Third Party Advisory -
CVE Modified by [email protected]
Aug. 21, 2024
Action Type Old Value New Value Changed Description Incorrect Privilege Assignment vulnerability in LiteSpeed Technologies LiteSpeed Cache allows Privilege Escalation.This issue affects LiteSpeed Cache: from n/a through 6.3.0.1. Incorrect Privilege Assignment vulnerability in LiteSpeed Technologies LiteSpeed Cache litespeed-cache allows Privilege Escalation.This issue affects LiteSpeed Cache: from 1.9 through 6.3.0.1. -
CVE Received by [email protected]
Aug. 21, 2024
Action Type Old Value New Value Added Description Incorrect Privilege Assignment vulnerability in LiteSpeed Technologies LiteSpeed Cache allows Privilege Escalation.This issue affects LiteSpeed Cache: from n/a through 6.3.0.1. Added Reference Patchstack https://patchstack.com/database/vulnerability/litespeed-cache/wordpress-litespeed-cache-plugin-6-3-0-1-unauthenticated-privilege-escalation-vulnerability?_s_id=cve [No types assigned] Added Reference Patchstack https://patchstack.com/articles/critical-privilege-escalation-in-litespeed-cache-plugin-affecting-5-million-sites?_s_id=cve [No types assigned] Added CWE Patchstack CWE-266 Added CVSS V3.1 Patchstack AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H


