CVE-2024-36268
Apache InLong TubeMQ Client: Remote Code Execution vulnerability
Description
Improper Control of Generation of Code ('Code Injection') vulnerability in Apache InLong. This issue affects Apache InLong: from 1.10.0 through 1.12.0, which could lead to Remote Code Execution. Users are advised to upgrade to Apache InLong's 1.13.0 or cherry-pick [1] to solve it. [1] https://github.com/apache/inlong/pull/10251
INFO
Published Date :
Aug. 2, 2024, 10:16 a.m.
Last Modified :
Nov. 21, 2024, 9:21 a.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] | ||||
| CVSS 3.1 | HIGH | 134c704f-9b21-4f2e-91b3-4a467353bcc0 |
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-36268.
| URL | Resource |
|---|---|
| https://lists.apache.org/thread/1w1yp1bg5sjvn46dszkf00tz1vfs0frc | Mailing List Vendor Advisory |
| http://www.openwall.com/lists/oss-security/2024/08/02/5 |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-36268 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-36268
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-36268 vulnerability anywhere in the article.

-
TheCyberThrone
CISA KEV Update September 2024 -Part V
The US CISA adds two vulnerabilities to its Known Exploited Vulnerabilities Catalog based on the evidence of active exploitationThe first vulnerability tracked as CVE-2024-43461, Microsoft Windows MSH ... Read more
-
Cybersecurity News
Windows 11 Surpasses Windows 10 as Dominant PC Gaming Platform
Please enable JavaScriptIn a notable development in the PC gaming landscape, Windows 11 has officially overtaken its predecessor, Windows 10, as the most widely adopted operating system among Steam us ... Read more

-
Cybersecurity News
Mekotio Trojan: A PowerShell-Based Threat Targeting Victims with Stealth and Persistence
The CYFIRMA Research and Advisory Team has identified a new and sophisticated cyber threat, dubbed the Mekotio Trojan. This malware leverages PowerShell, a powerful scripting language built into Windo ... Read more

-
Cybersecurity News
AISURU Botnet Identified in Massive DDoS Attack on Steam
A massive, coordinated DDoS attack disrupted Steam services globally and the Perfect World Esports platform in China on the weekend of August 24-26, coinciding with the launch of the highly anticipate ... Read more

-
Cybersecurity News
CVE-2024-43425: Moodle Remote Code Execution Vulnerability, PoC Published
A critical vulnerability (CVE-2024-43425) has been identified in Moodle, a widely-used Learning Management System. This flaw could enable attackers to execute malicious code on affected servers, poten ... Read more
-
Cybersecurity News
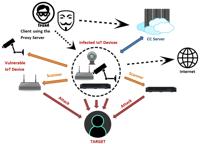
Hacking the Hacker: Researcher Found Critical Flaw (CVE-2024-45163) in Mirai Botnet
Image: FortinetSecurity researcher Jacob Masse has exposed a critical vulnerability within the Mirai botnet, the infamous malware that has plagued the Internet of Things (IoT) and server landscapes si ... Read more

-
Cybersecurity News
CVE-2024-28000 in LiteSpeed Cache Plugin Actively Exploited: Over 30,000 Attacks Blocked in 24 Hours
A critical security vulnerability in the widely used LiteSpeed Cache plugin for WordPress has come under active exploitation, with over 30,000 attack attempts blocked in just the past 24 hours, accord ... Read more
-
Cybersecurity News
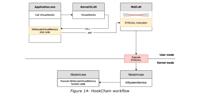
HookChain: The Technique That Bypass Exposes EDR in 94% of Security Solutions
Image Credit: M4v3r1ckIn an ever-evolving cybersecurity landscape, where threats are becoming more sophisticated by the day, the focus on Endpoint Detection and Response (EDR) systems has never been m ... Read more

-
TheCyberThrone
TheCyberThrone Security Week In Review – August 17, 2024
Welcome to TheCyberThrone cybersecurity week in review will be posted covering the important security happenings. This review is for the week ending Saturday, August 17, 2024.Microsoft Patch Tuesday-A ... Read more

-
TheCyberThrone
Zimbra addressed XSS and LFI vulnerabilities
Zimbra Collaboration disclosed three new security vulnerabilities. These flaws, impact Zimbra Collaboration versions 9.0 and 10.0, potentially exposing users to cross-site scripting (XSS) and local fi ... Read more

-
Cybersecurity News
CVE-2024-7593 (CVSS 9.8): Authentication Bypass in Ivanti vTM: Proof of Concept Available
Ivanti has issued a security advisory addressing a critical vulnerability (CVE-2024-7593) in its Virtual Traffic Manager (vTM), a software-based Layer 7 application delivery controller (ADC). The flaw ... Read more
-
Cybersecurity News
Ransomware Gangs’ New Tactic: Weaponizing Legitimate Entities
Part of a post on the Monti ransomware leak siteAccording to Sophos, cybercriminals are continually refining their methods of exerting pressure on victims. Over the past three years, the tactics emplo ... Read more

-
TheCyberThrone
TheCyberThrone Security Week In Review – August 10, 2024
Welcome to TheCyberThrone cybersecurity week in review will be posted covering the important security happenings. This review is for the week ending Saturday, August 10, 2024.Google Fixes Android Zero ... Read more
-
Cybersecurity News
PoC Exploit Released for Apache OFBiz Remote Code Execution Flaw (CVE-2024-38856)
Today, cybersecurity researcher Zeyad Azima from SecureLayer7 and Youssef Muhammad have published a proof-of-concept (PoC) exploit code for a critical vulnerability (CVE-2024-38856) in the Apache OFBi ... Read more

-
Cybersecurity News
Zero-Day Vulnerability: 18 Years of Exploiting the ‘0.0.0.0’ Flaw
A study revealed a hidden vulnerability that has plagued the world’s largest browsers for 18 years, leaving private and corporate networks susceptible to cyberattacks. Researchers from Oligo Security ... Read more

-
Cybersecurity News
Data Centers Alert: AMD Addresses SEV-SNP Vulnerabilities in EPYC Processors
AMD has released a security bulletin addressing three potential vulnerabilities in its Secure Encrypted Virtualization – Secure Nested Paging (SEV-SNP) technology. Discovered by a researcher, these vu ... Read more

-
TheCyberThrone
Google Fixes Android Zeroday Vulnerability CVE-2024-36971
Google has released patches for 46 bugs affecting its Android operating system in its August 2024 security update. This includes an actively exploited kernel vulnerability tracked as CVE-2024-36971 af ... Read more

-
Cybersecurity News
Linux Kernel Vulnerability CVE-2023-6817: Researcher Unveils Exploit Code
In a recent disclosure, a security researcher has published detailed technical insights and proof-of-concept exploit code for a critical vulnerability in the Linux kernel, identified as CVE-2023-6817. ... Read more

-
Cybersecurity News
Google Chrome Update Fixes Critical Code Execution Vulnerability (CVE-2024-7532)
Google has released a critical security update for its Chrome web browser on the Stable channel, addressing five vulnerabilities, one of which is rated as critical. The update, versions 127.0.6533.99/ ... Read more

-
TheCyberThrone
CISA adds CVE-2018-0824 to its KEV Catalog
The U.S. CISA added a deserialization of untrusted data vulnerability in Microsoft COM for Windows, tracked as CVE-2018-0824 with a CVSS score of 7.5, to its Known Exploited Vulnerabilities (KEV) cata ... Read more
The following table lists the changes that have been made to the
CVE-2024-36268 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Nov. 21, 2024
Action Type Old Value New Value Added Reference http://www.openwall.com/lists/oss-security/2024/08/02/5 -
Initial Analysis by [email protected]
Aug. 27, 2024
Action Type Old Value New Value Added CVSS V3.1 NIST AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Changed Reference Type https://lists.apache.org/thread/1w1yp1bg5sjvn46dszkf00tz1vfs0frc No Types Assigned https://lists.apache.org/thread/1w1yp1bg5sjvn46dszkf00tz1vfs0frc Mailing List, Vendor Advisory Added CPE Configuration OR *cpe:2.3:a:apache:inlong:*:*:*:*:*:*:*:* versions from (including) 1.10.0 up to (excluding) 1.13.0 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Aug. 22, 2024
Action Type Old Value New Value Added CWE CISA-ADP CWE-94 Added CVSS V3.1 CISA-ADP AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:H/A:L -
CVE Received by [email protected]
Aug. 02, 2024
Action Type Old Value New Value Added Description Improper Control of Generation of Code ('Code Injection') vulnerability in Apache InLong. This issue affects Apache InLong: from 1.10.0 through 1.12.0, which could lead to Remote Code Execution. Users are advised to upgrade to Apache InLong's 1.13.0 or cherry-pick [1] to solve it. [1] https://github.com/apache/inlong/pull/10251 Added Reference Apache Software Foundation https://lists.apache.org/thread/1w1yp1bg5sjvn46dszkf00tz1vfs0frc [No types assigned] Added CWE Apache Software Foundation CWE-94


