CVE-2024-45409
The Ruby SAML library vulnerable to a SAML authentication bypass via Incorrect XPath selector
Description
The Ruby SAML library is for implementing the client side of a SAML authorization. Ruby-SAML in <= 12.2 and 1.13.0 <= 1.16.0 does not properly verify the signature of the SAML Response. An unauthenticated attacker with access to any signed saml document (by the IdP) can thus forge a SAML Response/Assertion with arbitrary contents. This would allow the attacker to log in as arbitrary user within the vulnerable system. This vulnerability is fixed in 1.17.0 and 1.12.3.
INFO
Published Date :
Sept. 10, 2024, 7:15 p.m.
Last Modified :
Nov. 21, 2024, 9:37 a.m.
Remotely Exploit :
Yes !
Source :
[email protected]
Affected Products
The following products are affected by CVE-2024-45409
vulnerability.
Even if cvefeed.io is aware of the exact versions of the
products
that
are
affected, the information is not represented in the table below.
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] | ||||
| CVSS 3.1 | CRITICAL | [email protected] |
Solution
- Update the ruby-saml package.
- Upgrade the affected packages.
Public PoC/Exploit Available at Github
CVE-2024-45409 has a 5 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-45409.
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-45409 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-45409
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
Proof-of-concept exploits and reproduction labs for CVEs analyzed by the Exploit Intelligence Platform
cves exploits proof-of-concept
Shell Python PHP Ruby JavaScript C# Java HTML C GDB
Ruby-SAML / GitLab Authentication Bypass (CVE-2024-45409) exploit
Python
None
Python
一个 CVE 漏洞预警知识库,无 exp/poc,部分包含修复方案。A knowledge base of CVE security vulnerability, no PoCs/exploits.
Ostorlab KEV: One-command to detect most remotely known exploitable vulnerabilities. Sourced from CISA KEV, Google's Tsunami, Ostorlab's Asteroid and Bug Bounty programs.
cisa-kev vulnerability 0day cisa exploits
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-45409 vulnerability anywhere in the article.

-
Daily CyberSecurity
Critical Authentication Bypass Flaws Discovered in Ruby SAML Library (CVE-2025-66567 & CVE-2025-66568)
A pair of critical security vulnerabilities has been disclosed in the Ruby SAML library, a foundational tool used by developers to implement client-side SAML authorization. Both flaws carry a critical ... Read more

-
Daily CyberSecurity
Critical JWE Ruby Flaw (CVE-2025-54887) Bypasses AES-GCM Authentication, Exposing Encrypted Data
A severe security vulnerability has been uncovered in the Ruby implementation of JSON Web Encryption (JWE), tracked as CVE-2025-54887, carrying a CVSS score of 9.1. The flaw stems from missing authent ... Read more

-
Daily CyberSecurity
Critical Node-SAML Flaw (CVE-2025-54369) Exposes SAML 2.0 to Authentication Bypass
A critical vulnerability has been discovered in the popular open-source Node.js library Node-SAML, used to implement SAML 2.0 authentication workflows. Tracked as CVE-2025-54369 and scoring a CVSS v4 ... Read more

-
Daily CyberSecurity
GitLab Releases Security Updates: XSS and Authorization Bypass Flaws Patched
GitLab has released security updates for its Community Edition (CE) and Enterprise Edition (EE), addressing multiple vulnerabilities that could allow attackers to perform cross-site scripting (XSS) at ... Read more

-
The Cyber Express
December 2024 Cyble Report: Malware, Phishing, and IoT Vulnerabilities on the Rise
The latest Sensor Intelligence Report from Cyble, dated December 4–10, 2024, sheds light on a troubling increase in cyber threats, including malware intrusions, phishing scams, and attacks targeting v ... Read more

-
Cybersecurity News
CVE-2024-11274: GitLab Vulnerability Exposes User Accounts
GitLab has issued an important security update addressing a range of vulnerabilities affecting multiple versions of its platform. The update, which includes versions 17.6.2, 17.5.4, and 17.4.6 for Com ... Read more

-
Cybersecurity News
CVE-2024-9693: GitLab Issues Critical Patch for Kubernetes Agent
GitLab has released a critical security update addressing a high-severity vulnerability that could grant unauthorized access to Kubernetes clusters. Versions 17.5.2, 17.4.4, and 17.3.7 of both the Com ... Read more

-
Cybersecurity News
CVE-2024-45656: A 9.8 Severity Threat to IBM Power Systems Security
A critical vulnerability has been discovered in IBM Power Systems servers, potentially allowing unauthorized access and complete control over affected systems. The flaw, identified as CVE-2024-45656, ... Read more

-
Cybersecurity News
CVE-2024-38821 (CVSS 9.1) Allows Authorization Bypass in Spring WebFlux Applications
In a recent security advisory, Spring Security disclosed CVE-2024-38821, a critical vulnerability impacting WebFlux applications, with a CVSS severity score of 9.1. The flaw enables an “authorization ... Read more
-
Cybersecurity News
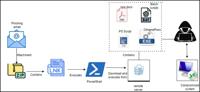
Healthcare Under Fire: HeptaX Campaign Steals and Manipulates Sensitive Data
Infection chain | Image: CRILCyble Research and Intelligence Labs (CRIL) has recently uncovered a covert and sophisticated cyberespionage campaign dubbed “HeptaX,” which exploits Remote Desktop Protoc ... Read more

-
Cybersecurity News
CVE-2024-20424 (CVSS 9.9): Cisco FMC Software Vulnerability Grants Attackers Root Access
Cisco has issued a critical security advisory warning of a command injection vulnerability in its Secure Firewall Management Center (FMC) Software. Tracked as CVE-2024-20424 and assigned a CVSS score ... Read more

-
The Cyber Express
Cyble Sensors Uncover Cyberattacks Targeting Key Vulnerabilities
Cyble’s Vulnerability Intelligence unit has spotlighted a series of cyberattacks targeting critical vulnerabilities in various software systems, including the Ruby SAML library, D-Link NAS devices, an ... Read more
-
Cybersecurity News
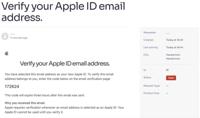
$50,000 Bounty: Researcher Reveals Critical Zendesk Email Spoofing Flaw (CVE-2024-49193)
Image: DanielIn a detailed analysis by security researcher Daniel, a serious vulnerability in Zendesk’s email management system, tracked as CVE-2024-49193, has been revealed. This flaw exposes compani ... Read more

-
Help Net Security
Week in review: Microsoft fixes two exploited zero-days, SOC teams are losing trust in security tools
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Microsoft patches two zero-days exploited in the wild (CVE-2024-43573, CVE-2024-43572) For October 202 ... Read more

-
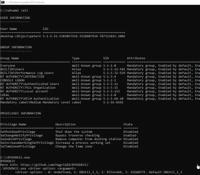
Help Net Security
Exploit code for critical GitLab auth bypass flaw released (CVE-2024-45409)
If you run a self-managed GitLab installation with configured SAML-based authentication and you haven’t upgraded it since mid-September, do it now, because security researchers have published an analy ... Read more
-
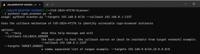
Cybersecurity News
Exploit Releases for TeamViewer Flaws (CVE-2024-7479 & CVE-2024-7481) Let Unprivileged Users Load Arbitrary Kernel Drivers
Image: Peter GabaldonSecurity researcher Peter Gabaldon published the technical details and proof-of-concept exploit code for two high-severity vulnerabilities, CVE-2024-7479 and CVE-2024-7481, which ... Read more
-
Cybersecurity News
Researcher Releases Open-Source Scanner for CVE-2024-47176 CUPS Vulnerability
Renowned security researcher Marcus Hutchins has unveiled a new open-source tool designed to help administrators and security professionals identify vulnerable instances of the Common Unix Printing Sy ... Read more
-
Cybersecurity News
Researchers Detail Ruby-SAML/GitLab Flaw (CVE-2024-45409) Allows SAML Authentication Bypass
In a recent analysis conducted by Harsh Jaiswal and Rahul Maini at ProjectDiscovery, a critical vulnerability, CVE-2024-45409, was uncovered, exposing a flaw in Ruby-SAML and OmniAuth-SAML libraries, ... Read more

-
Cybersecurity News
CISA Warns of Critical Flaws in TEM Opera Plus FM Transmitter Products Used in Critical Infrastructure
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an advisory regarding two critical vulnerabilities in the TEM Opera Plus FM Family Transmitter products, widely used in crit ... Read more
-
Cybersecurity News
Researcher Details RCE Flaw (CVE-2024-36435) in Supermicro BMC IPMI Firmware
A newly discovered critical vulnerability, CVE-2024-36435, has been uncovered in several Supermicro enterprise products, potentially exposing organizations to significant security risks. Discovered by ... Read more
The following table lists the changes that have been made to the
CVE-2024-45409 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Nov. 21, 2024
Action Type Old Value New Value Added Reference https://lists.debian.org/debian-lts-announce/2024/11/msg00006.html Added Reference https://news.ycombinator.com/item?id=41586031 Added Reference https://security.netapp.com/advisory/ntap-20240926-0008/ Added Reference https://ssoready.com/blog/engineering/ruby-saml-pwned-by-xml-signature-wrapping-attacks/ -
Initial Analysis by [email protected]
Sep. 20, 2024
Action Type Old Value New Value Added CVSS V3.1 NIST AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Changed Reference Type https://github.com/omniauth/omniauth-saml/security/advisories/GHSA-cvp8-5r8g-fhvq No Types Assigned https://github.com/omniauth/omniauth-saml/security/advisories/GHSA-cvp8-5r8g-fhvq Vendor Advisory Changed Reference Type https://github.com/SAML-Toolkits/ruby-saml/commit/1ec5392bc506fe43a02dbb66b68741051c5ffeae No Types Assigned https://github.com/SAML-Toolkits/ruby-saml/commit/1ec5392bc506fe43a02dbb66b68741051c5ffeae Patch Changed Reference Type https://github.com/SAML-Toolkits/ruby-saml/commit/4865d030cae9705ee5cdb12415c654c634093ae7 No Types Assigned https://github.com/SAML-Toolkits/ruby-saml/commit/4865d030cae9705ee5cdb12415c654c634093ae7 Patch Changed Reference Type https://github.com/SAML-Toolkits/ruby-saml/security/advisories/GHSA-jw9c-mfg7-9rx2 No Types Assigned https://github.com/SAML-Toolkits/ruby-saml/security/advisories/GHSA-jw9c-mfg7-9rx2 Vendor Advisory Added CPE Configuration OR *cpe:2.3:a:onelogin:ruby-saml:*:*:*:*:*:*:*:* versions up to (excluding) 1.12.3 *cpe:2.3:a:onelogin:ruby-saml:*:*:*:*:*:*:*:* versions from (including) 1.13.0 up to (excluding) 1.17.0 Added CPE Configuration OR *cpe:2.3:a:omniauth:omniauth_saml:*:*:*:*:*:ruby:*:* versions up to (including) 1.10.3 *cpe:2.3:a:omniauth:omniauth_saml:2.0.0:*:*:*:*:ruby:*:* *cpe:2.3:a:omniauth:omniauth_saml:2.1.0:*:*:*:*:ruby:*:* Added CPE Configuration OR *cpe:2.3:a:gitlab:gitlab:*:*:*:*:*:*:*:* versions up to (excluding) 16.11.10 *cpe:2.3:a:gitlab:gitlab:*:*:*:*:*:*:*:* versions from (including) 17.0.0 up to (excluding) 17.0.8 *cpe:2.3:a:gitlab:gitlab:*:*:*:*:*:*:*:* versions from (including) 17.1.0 up to (excluding) 17.1.8 *cpe:2.3:a:gitlab:gitlab:*:*:*:*:*:*:*:* versions from (including) 17.2.0 up to (excluding) 17.2.7 *cpe:2.3:a:gitlab:gitlab:*:*:*:*:*:*:*:* versions from (including) 17.3.0 up to (excluding) 17.3.3 -
CVE Modified by [email protected]
Sep. 11, 2024
Action Type Old Value New Value Added Reference GitHub, Inc. https://github.com/omniauth/omniauth-saml/security/advisories/GHSA-cvp8-5r8g-fhvq [No types assigned] -
CVE Received by [email protected]
Sep. 10, 2024
Action Type Old Value New Value Added Description The Ruby SAML library is for implementing the client side of a SAML authorization. Ruby-SAML in <= 12.2 and 1.13.0 <= 1.16.0 does not properly verify the signature of the SAML Response. An unauthenticated attacker with access to any signed saml document (by the IdP) can thus forge a SAML Response/Assertion with arbitrary contents. This would allow the attacker to log in as arbitrary user within the vulnerable system. This vulnerability is fixed in 1.17.0 and 1.12.3. Added Reference GitHub, Inc. https://github.com/SAML-Toolkits/ruby-saml/security/advisories/GHSA-jw9c-mfg7-9rx2 [No types assigned] Added Reference GitHub, Inc. https://github.com/SAML-Toolkits/ruby-saml/commit/1ec5392bc506fe43a02dbb66b68741051c5ffeae [No types assigned] Added Reference GitHub, Inc. https://github.com/SAML-Toolkits/ruby-saml/commit/4865d030cae9705ee5cdb12415c654c634093ae7 [No types assigned] Added CWE GitHub, Inc. CWE-347 Added CVSS V3.1 GitHub, Inc. AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:N