CVE-2024-8504
VICIdial Authenticated Remote Code Execution
Description
An attacker with authenticated access to VICIdial as an "agent" can execute arbitrary shell commands as the "root" user. This attack can be chained with CVE-2024-8503 to execute arbitrary shell commands starting from an unauthenticated perspective.
INFO
Published Date :
Sept. 10, 2024, 8:15 p.m.
Last Modified :
Nov. 4, 2025, 5:16 p.m.
Remotely Exploit :
Yes !
Source :
bbf0bd87-ece2-41be-b873-96928ee8fab9
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | HIGH | 134c704f-9b21-4f2e-91b3-4a467353bcc0 |
Public PoC/Exploit Available at Github
CVE-2024-8504 has a 2 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-8504.
| URL | Resource |
|---|---|
| https://korelogic.com/Resources/Advisories/KL-001-2024-012.txt | |
| https://www.vicidial.org/vicidial.php | |
| http://seclists.org/fulldisclosure/2024/Sep/26 |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-8504 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-8504
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
CVE-2024-8504
Python
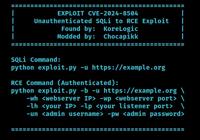
VICIdial Unauthenticated SQLi to RCE Exploit (CVE-2024-8503 and CVE-2024-8504)
Python
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-8504 vulnerability anywhere in the article.
-
Cybersecurity News
Apache Roller Patches CSRF Flaw CVE-2024-46911 in Latest Update
The Apache Software Foundation has released a security update for Apache Roller, a popular Java-based blogging platform. This update addresses a critical Cross-site Request Forgery (CSRF) vulnerabilit ... Read more
-
Cybersecurity News
Google Pays $55,000 Bounty for Chrome Security Flaw
Google has released a Stable Channel update for Chrome on Windows, Mac, and Linux, bringing the browser to version 129.0.6668.100/.101. The update is expected to roll out over the next few days and in ... Read more

-
Cybersecurity News
Microsoft’s October 2024 Patch Tuesday: Zero-Day Exploits and Critical Vulnerabilities Patched
Microsoft’s October 2024 Patch Tuesday delivered a crucial set of security updates, addressing a total of 121 vulnerabilities across its ecosystem. This includes three critical vulnerabilities and 114 ... Read more

-
Cybersecurity News
CyberVolk: From Hacktivism to Ransomware – Researcher Exposes New Threat
CyberVolk dialog window | Image: Rapid7Cybersecurity researchers at Rapid7 Labs have released a detailed report on CyberVolk, a politically motivated hacktivist group that transitioned into using rans ... Read more

-
Cybersecurity News
CVE-2024-5102: Avast Antivirus Flaw Could Allow Hackers to Delete Files and Run Code as SYSTEM
A high-severity vulnerability (CVE-2024-5102) has been discovered in Avast Antivirus for Windows, potentially allowing attackers to gain elevated privileges and wreak havoc on users’ systems. This fla ... Read more
-
Cybersecurity News
CVE-2024-20432 (CVSS 9.9): Cisco Nexus Dashboard Fabric Controller Exposed to RCE
Cisco has issued a security advisory addressing a critical vulnerability (CVE-2024-20432) in its Nexus Dashboard Fabric Controller (NDFC). This flaw, which carries a severity rating of 9.9 out of 10 o ... Read more
-
Cybersecurity News
PoC Exploit Releases for Zimbra RCE Flaw CVE-2024-45519: Mass Exploitation Detected
Image: ptswarmZimbra, one of the most widely used email and collaboration platforms globally, has recently been identified as vulnerable to a critical security flaw that could allow attackers to take ... Read more

-
Cybersecurity News
CVE-2024-8940 (CVSS 10): Critical Flaw in Scriptcase Low-Code Platform Leaves Developers at Risk
Developers using the popular low-code platform Scriptcase are urged to update their software immediately after discovering three critical vulnerabilities that could expose their applications to seriou ... Read more
-
Cybersecurity News
30 Exploitable Flaws: Alarming Study on Home Router Defaults
A study titled “Exposed by Default: A Security Analysis of Home Router Default Settings” has shed light on the pervasive vulnerabilities present in home routers, highlighting significant risks associa ... Read more
-
Cybersecurity News
Unmasking “Marko Polo”: The Infostealer Gang Targeting Thousands
Marko Polo infection chain (Source: Recorded Future)Researchers at Recorded Future have uncovered a large-scale cyberattack affecting tens of thousands of devices worldwide. It was later revealed that ... Read more

-
Cybersecurity News
CISA Flags Two Actively Exploited Vulnerabilities: Critical Threats to Windows and WhatsUp Gold
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning, adding two actively exploited security flaws to its Known Exploited Vulnerabilities (KEV) catalog, urging immedia ... Read more
-
Cybersecurity News
Critical Flaws Found in VICIdial Contact Center Suite: CVE-2024-8503 and CVE-2024-8504, PoC Published
In a concerning development for call centers using VICIdial, a popular open-source contact center solution, two high-severity security vulnerabilities have been discovered that could lead to severe da ... Read more

-
seclists.org
KL-001-2024-012: VICIdial Authenticated Remote Code Execution
Full Disclosure mailing list archives KL-001-2024-012: VICIdial Authenticated Remote Code Execution From: KoreLogic Disclosures via Fulldisclosure <fulldisclosure () seclists org> Date: Tue, 10 Sep 20 ... Read more
The following table lists the changes that have been made to the
CVE-2024-8504 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Nov. 04, 2025
Action Type Old Value New Value Added Reference http://seclists.org/fulldisclosure/2024/Sep/26 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Sep. 12, 2024
Action Type Old Value New Value Added CVSS V3.1 CISA-ADP AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H -
CVE Received by bbf0bd87-ece2-41be-b873-96928ee8fab9
Sep. 10, 2024
Action Type Old Value New Value Added Description An attacker with authenticated access to VICIdial as an "agent" can execute arbitrary shell commands as the "root" user. This attack can be chained with CVE-2024-8503 to execute arbitrary shell commands starting from an unauthenticated perspective. Added Reference KoreLogic https://korelogic.com/Resources/Advisories/KL-001-2024-012.txt [No types assigned] Added Reference KoreLogic https://www.vicidial.org/vicidial.php [No types assigned] Added CWE KoreLogic CWE-78


